
A Complete Guide to Building an Internal Cyber Security Team
A robust IT security team is essential for safeguarding an organization's critical data and infrastructure. Effective leadership and strategic structuring are key to ensuring your security team is prepared to face emerging cyber threats. This comprehensive guide will explore the various aspects of cybersecurity leadership, from defining IT security team roles to minimizing conflict and preventing the dangers of an understaffed team. Whether you're leading a small company or managing a large organization, this guide offers practical insights to help you build, lead, and optimize your security team for success.
1. Defining IT Security Team Roles: Building a Strong Foundation
The first step in creating an effective IT security team is to understand the different roles that contribute to a well-rounded and efficient team. These roles can vary depending on the size and complexity of your organization, but generally include:
- Chief Information Security Officer (CISO): The CISO is responsible for overseeing the entire cybersecurity strategy and ensuring alignment with business goals.
- Security Analysts: These team members monitor and analyze security systems for potential vulnerabilities, intrusions, and other threats.
- Security Engineers: Security engineers design, implement, and maintain security tools and systems to protect organizational assets.
- Incident Response Team: This specialized group focuses on identifying, managing, and mitigating security breaches and incidents.
- Compliance and Risk Management Specialists: These professionals ensure your security practices adhere to relevant regulations and standards.
2. Reducing Conflict Between IT and Security Teams
In many organizations, conflict arises between the IT team and the security team. IT often prioritizes operational efficiency and system functionality, while the security team focuses on preventing risks and vulnerabilities. This misalignment can lead to tension and inefficiencies.
To foster collaboration between these teams, consider the following strategies:
- Promote Communication: Regular meetings and cross-functional training sessions can help bridge the gap between teams and foster a shared understanding of each other’s priorities.
- Align Goals: Ensure that both IT and security teams are working toward the same organizational objectives, with a clear understanding of the role each team plays in achieving them.
- Encourage Joint Problem-Solving: When issues arise, encourage both teams to collaborate on solutions that balance security needs with operational efficiency.
GRC Software Solutions Build For Security Team
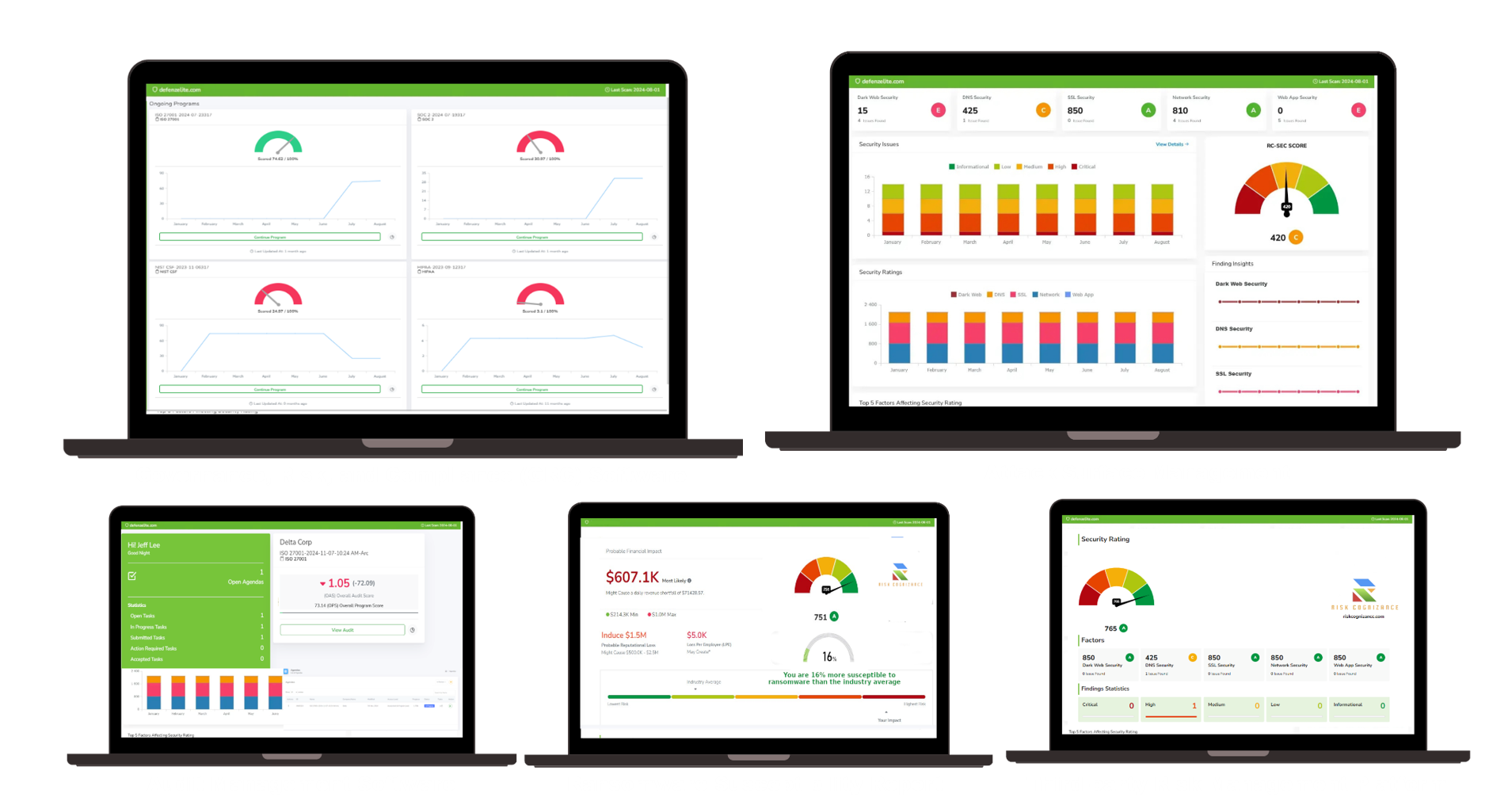
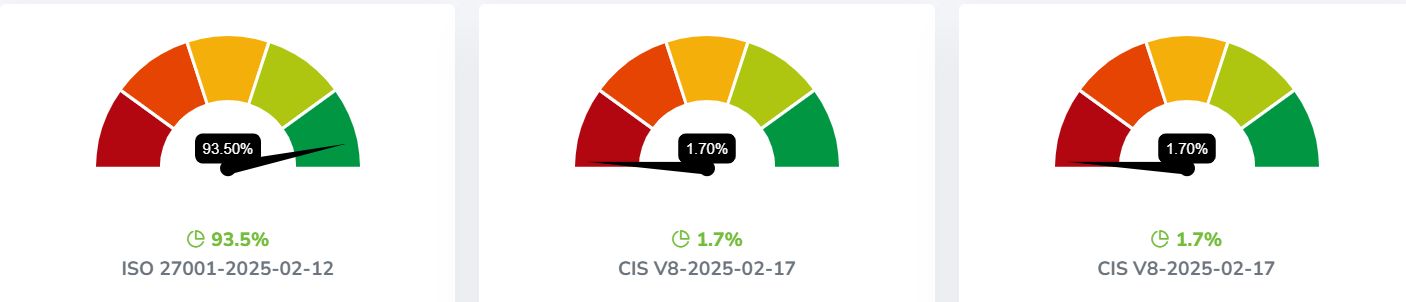
3. The Dangers of an Understaffed IT Security Team
An understaffed IT security team can be a significant vulnerability for an organization. With fewer personnel, there is a higher chance of missing critical threats, delays in incident response, and an increased risk of burnout for security professionals. The dangers of an understaffed team include:
- Increased Risk Exposure: Without sufficient coverage, there may be gaps in monitoring, detection, and response capabilities, leaving the organization exposed to cyberattacks.
- Delayed Incident Response: A lack of resources can hinder the speed at which incidents are addressed, increasing the potential for greater damage.
- Employee Burnout: Security professionals in understaffed teams may experience high stress and burnout, leading to decreased productivity and turnover.
To mitigate these risks, ensure your IT security team is adequately staffed with the right mix of skills and experience. Consider investing in security automation tools to supplement human resources and enhance the team’s efficiency.
4. IT Security Team Makeup for Small Companies
For small businesses, building an effective IT security team can be challenging due to limited resources. However, with the right approach, even a small team can provide robust security.
The ideal IT security team structure for a small company includes:
- IT Security Manager or CISO: Even in a small company, having a dedicated leader to oversee cybersecurity strategy is crucial.
- Security Analyst: This role involves monitoring systems for vulnerabilities, running security audits, and responding to incidents.
- Network Engineer (with Security Expertise): This person ensures that the organization’s network infrastructure is secure, and can manage firewalls, VPNs, and other security measures.
- Outsourced Support: Small companies may also choose to partner with managed security service providers (MSSPs) to supplement their internal team and access specialized expertise without needing to hire full-time staff.
5. IT Security Team Structure: Best Practices
When designing the structure of your IT security team, it’s important to consider the size of your organization, your specific security needs, and the complexity of your IT infrastructure. Best practices for structuring your security team include:
- Tiered Security Structure: Organize your security team into tiers based on expertise and responsibility. For example, junior security analysts may handle routine monitoring, while senior engineers focus on complex threats and strategic planning.
- Clear Reporting Lines: Establish clear reporting lines between team members and departments. The CISO should be closely aligned with senior management to ensure cybersecurity remains a top priority.
- Cross-Functional Collaboration: Encourage collaboration with other departments such as legal, HR, and compliance to ensure a holistic approach to cybersecurity across the organization.
- Continuous Training and Development: Cyber threats are constantly evolving, so ongoing education and skill development should be a key part of your security team’s growth.
Conclusion
Building and leading a high-performing IT security team is a critical responsibility for any cybersecurity leader. By defining clear roles, reducing conflict between IT and security teams, ensuring adequate staffing, and creating a structured approach to team makeup, you can significantly enhance your organization’s security posture. With the right leadership and team structure in place, your IT security team will be equipped to effectively mitigate risks, respond to threats, and protect your organization’s digital assets.


