Which Security Model Does Not Protect the Integrity of Information?
Securing sensitive data is more important than ever. Organizations face numerous challenges when selecting the right security model for their systems, especially when it comes to safeguarding not just confidentiality but also the integrity of the information they handle. One of the most frequently asked questions is: Which security model does not protect the integrity of information?
At Risk Cognizance, we understand that choosing the right security model is a crucial decision for any organization. As a user-friendly, automated compliance solution, we guide businesses in navigating this complex landscape to ensure they meet compliance standards with ease while protecting their valuable data.
The Key Role of Data Integrity in Security Models
Before diving into which security models fail to protect data integrity, it's essential to understand what data integrity is and why it matters. Data integrity ensures that the information you store and use is accurate, reliable, and unaltered by unauthorized individuals. This level of protection is crucial for organizations that deal with sensitive data or are bound by strict regulatory compliance standards.
When businesses prioritize data integrity, they ensure that their systems are not only secure but also trustworthy. At Risk Cognizance, we believe that compliance should be as simple as possible. That’s why we provide a solution that automates the compliance process, making it easy for companies to stay on top of their data protection requirements without unnecessary complexity.
Exploring the Security Models
Let’s explore some of the most widely used security models, focusing on their strengths and weaknesses in relation to data integrity.
Bell-LaPadula Model: Confidentiality Over Integrity
The Bell-LaPadula Model is one of the most recognized security models, with a primary focus on confidentiality. It uses mandatory access controls to restrict access based on classification levels, such as Top Secret, Secret, and Confidential. However, while this model effectively prevents unauthorized users from accessing sensitive information, it does not prioritize data integrity.
Organizations that implement the Bell-LaPadula Model are primarily focused on ensuring that their data is confidential. However, if you're looking for a model that ensures data integrity—preventing unauthorized users from tampering with or corrupting data—the Bell-LaPadula model might fall short.
At Risk Cognizance, we make it easy for businesses to choose solutions that prioritize both confidentiality and integrity, with automated compliance management that reduces risk and enhances data protection.
Biba Model: Integrity at Its Core
Unlike the Bell-LaPadula Model, the Biba Model focuses on maintaining data integrity. It emphasizes "no write up, no read down," which ensures that users cannot write data to higher classification levels or read data from lower levels that could compromise its integrity. This model is designed to protect data from being altered or corrupted by unauthorized access.
For businesses that are focused on ensuring the integrity of their data—particularly when compliance is a concern—the Biba Model is a valuable approach. Risk Cognizance can help organizations streamline their compliance with integrity-focused security frameworks, using our automated tools to reduce risk and enhance data protection.
Role-Based Access Control (RBAC): Flexibility for Different Needs
Role-Based Access Control (RBAC) is a popular security model used by many organizations because of its flexibility. RBAC assigns permissions based on roles, so users only have access to the data they need to perform their jobs. While RBAC can be configured to maintain both confidentiality and integrity, it is only effective if set up properly.
For organizations that require flexibility and ease of use, Risk Cognizance’s automated compliance platform integrates seamlessly with RBAC configurations, helping businesses manage access and maintain data integrity without complexity.
Security Frameworks and Data Integrity
When securing your organization’s data, security models are only part of the picture. Complementing these models with comprehensive security frameworks can enhance data protection, ensuring integrity is consistently maintained.
NIST Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) is a set of guidelines designed to help organizations manage and reduce cybersecurity risk. It emphasizes protecting the confidentiality, integrity, and availability of data and systems. By following the NIST framework, organizations can ensure they adopt security practices that address both confidentiality and integrity of their data.
Risk Cognizance aligns with NIST CSF, offering automated tools that help businesses stay compliant with its guidelines while focusing on maintaining the integrity of sensitive data.
ISO/IEC 27001: Information Security Management
ISO/IEC 27001 is a global standard for information security management systems (ISMS). It focuses on establishing, implementing, and continuously improving a framework for managing sensitive company information. Data integrity is central to the ISO 27001 standard, making it a perfect complement to security models that prioritize protecting data from unauthorized alterations or tampering.
Risk Cognizance’s platform automates the compliance process with ISO/IEC 27001, ensuring your organization can effectively protect data integrity while reducing the risk of non-compliance.
CIS Controls
The Center for Internet Security (CIS) provides a set of 20 cybersecurity controls designed to help organizations improve their security posture. Many of these controls are centered around ensuring the integrity of data, such as ensuring the configuration of critical systems is properly maintained, and access is carefully controlled. By implementing these controls, organizations can strengthen their data integrity protection.
Risk Cognizance helps organizations implement CIS Controls with ease through automated compliance solutions, making it simple for businesses to stay on top of their security requirements and enhance data integrity protection.
Why Risk Cognizance Is the Solution to Your Security Needs
As organizations navigate the complexities of data protection, choosing a security model that balances confidentiality and integrity is critical. However, the process of selecting and implementing the right solution doesn’t have to be complicated. That’s where Risk Cognizance comes in.
With our automated compliance platform, businesses can effortlessly maintain data security while ensuring compliance with industry standards. Whether you’re prioritizing confidentiality, integrity, or both, our platform is designed to meet your needs with minimal effort.
We believe compliance should be simple. Risk Cognizance provides an intuitive, user-friendly interface that automates the compliance process, ensuring you stay ahead of evolving security threats and regulatory requirements. From automated vulnerability assessments to comprehensive reporting, our platform ensures that your data is protected, compliant, and trustworthy.
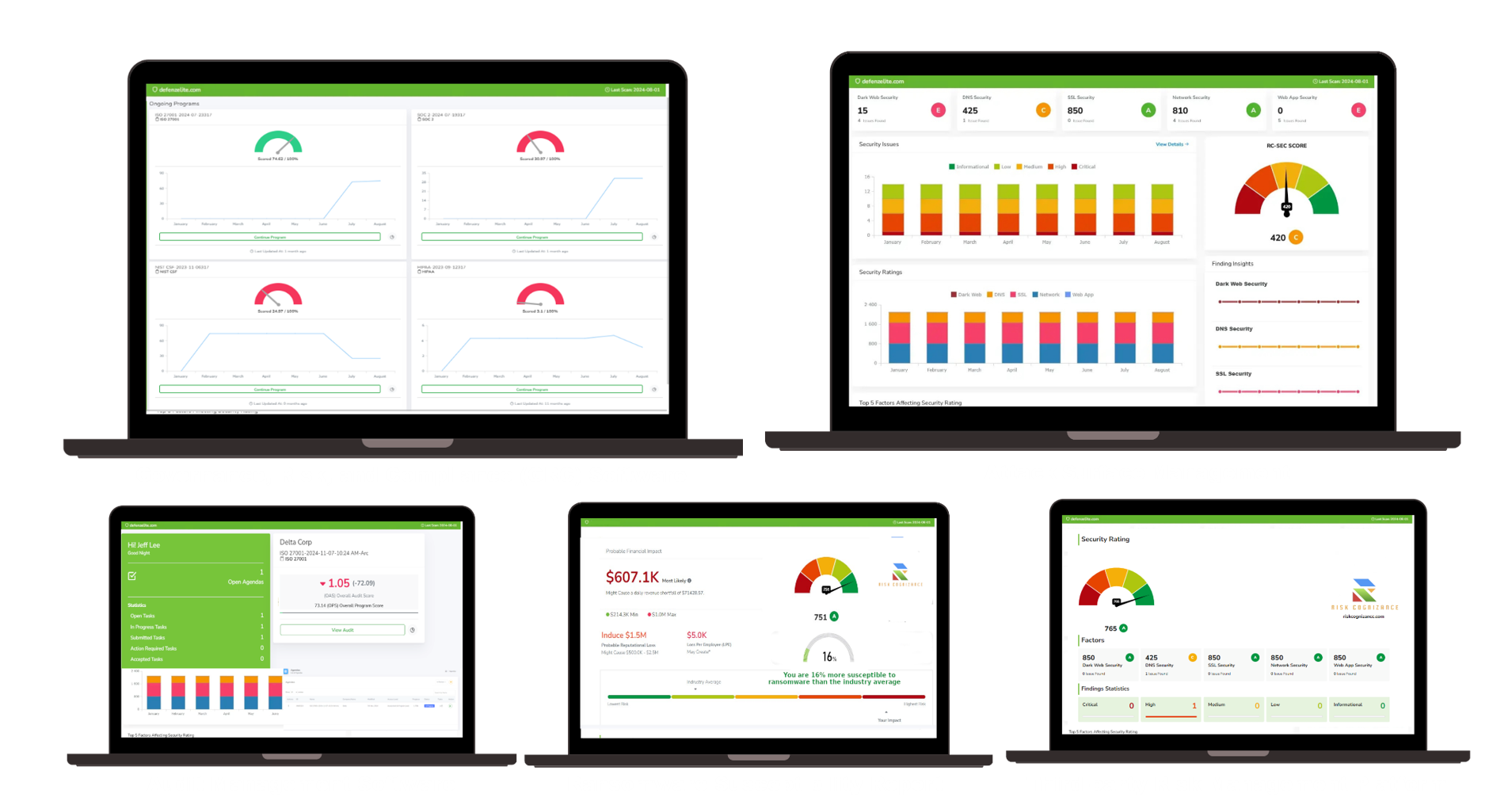
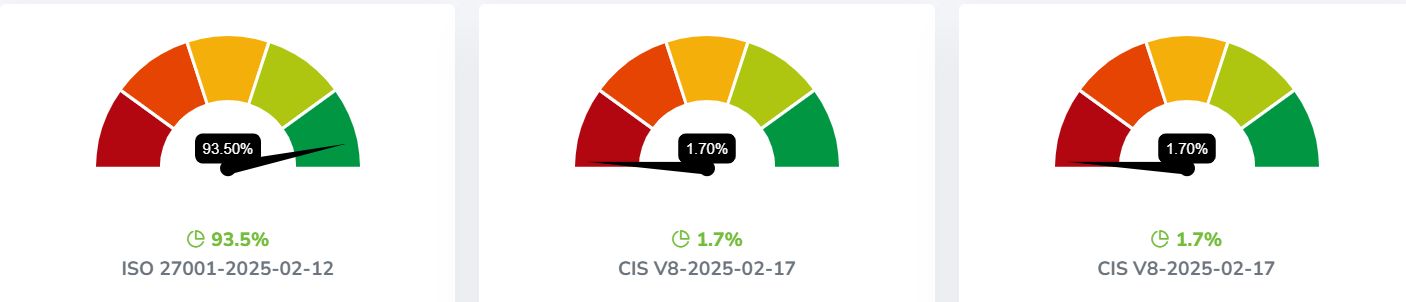
Use Cases
1. Compliance Automation for Healthcare Providers
Healthcare organizations handle a vast amount of sensitive patient data and are subject to strict compliance regulations such as HIPAA. By leveraging Risk Cognizance’s automated compliance solution, healthcare providers can ensure that their data is protected under industry standards while minimizing the manual effort required to maintain compliance. The platform continuously assesses vulnerabilities, automates reporting, and ensures data integrity through automated updates to security protocols.
2. Financial Institutions Ensuring Data Integrity and Compliance
Financial institutions are often the target of cyberattacks due to the highly sensitive nature of their data. Using Risk Cognizance, financial institutions can automate compliance with key standards like PCI DSS, SOC 2, and ISO 27001. The platform’s real-time data integrity protection ensures that transaction data, account details, and customer records are always secure and reliable, helping the institution maintain trust and comply with regulatory requirements.
3. Global E-commerce Platform Protecting User Data
An e-commerce platform serving millions of customers worldwide needs to ensure that customer data remains intact and secure at all times. With Risk Cognizance, the platform can automate compliance checks across multiple security frameworks, protect sensitive customer information, and ensure that data integrity is maintained. The platform simplifies managing user data security, ensuring compliance with GDPR and other global data protection regulations.
Case Studies
Case Study 1: Protecting Sensitive Customer Data in a Healthcare Organization
A large healthcare organization with multiple hospitals and clinics needed to ensure patient data was fully protected in compliance with HIPAA regulations. The company’s manual compliance processes were not sufficient to keep up with the evolving regulatory landscape and the increasing volume of sensitive data.
By implementing Risk Cognizance, the organization automated its compliance process, ensuring that sensitive data was always protected. The platform provided real-time vulnerability assessments, compliance reports, and ensured data integrity by automating encryption protocols and access controls. This not only ensured compliance with HIPAA but also enhanced data security, making patient data more reliable and protected from tampering.
Case Study 2: Ensuring Data Integrity for a Financial Institution
A financial institution serving thousands of clients across the globe was struggling to manage its compliance across various regulatory frameworks, including SOC 2, PCI DSS, and ISO 27001. The company’s manual security audits and risk assessments were inefficient and prone to human error, potentially compromising data integrity.
By adopting Risk Cognizance, the institution automated its security assessments, real-time compliance monitoring, and reporting processes. The platform ensured that financial transactions and sensitive customer data were protected with the latest security protocols, maintaining data integrity while reducing the risk of compliance violations. As a result, the institution achieved a higher level of security, compliance, and customer trust.
Conclusion
When it comes to choosing the right security model for your organization, it’s essential to understand which models focus on protecting integrity and which prioritize confidentiality. While the Bell-LaPadula Model is excellent for protecting confidentiality, it does not address the integrity of data. For businesses that need to ensure the integrity of their data, models like Biba and configurations like RBAC are better suited to meet those needs.
By integrating these models with comprehensive security frameworks like NIST CSF, ISO/IEC 27001, and CIS Controls, businesses can enhance their overall security posture and ensure the integrity of their data.
At Risk Cognizance, we make protecting your data simple. With our automated, easy-to-use platform, compliance becomes a hassle-free process, allowing you to focus on what matters most: the success and security of your business. Let us handle the complexities of compliance so you can rest easy knowing that your data is protected and your organization remains compliant.


