
SOC 2 Compliance Platform and Tools
A Comprehensive Guide to SOC 2 Compliance and GRC Platforms
SOC 2 (System and Organization Controls 2) is a framework designed by the American Institute of Certified Public Accountants (AICPA) to ensure that service organizations securely manage customer data. Achieving and maintaining SOC 2 compliance is a significant undertaking, but it is essential for building trust and credibility with clients.
Modern compliance has been simplified by the advent of Governance, Risk, and Compliance (GRC) platforms like Risk Cognizance. These tools automate many of the manual, time-consuming tasks associated with SOC 2, from risk assessment and evidence collection to continuous monitoring, allowing organizations to focus on strategic security initiatives rather than administrative overhead.
Phase 1: Pre-Audit Preparation
This is the most critical phase. Proper preparation can save significant time and resources during the actual audit.
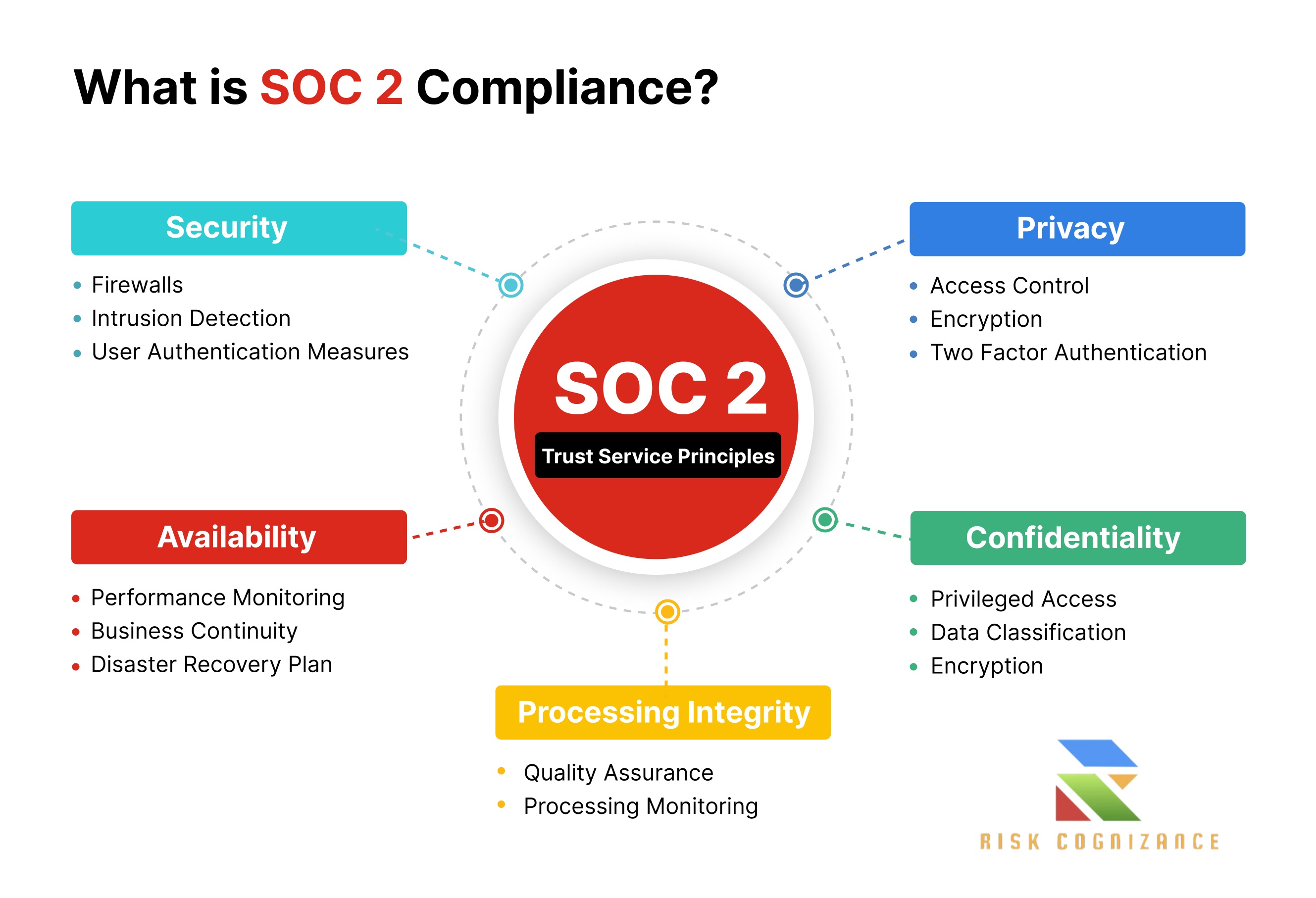
1. Define Your Scope First, you must determine which systems, data, and processes will be included in the audit. This is the "system description." It typically covers your technology infrastructure, software, data flows, and personnel. You also need to select which of the five Trust Services Criteria (TSCs) are relevant to your business:
- Security (Mandatory): Protection against unauthorized access, disclosure, and modification.
- Availability: The system's ability to be used for its intended purpose.
- Processing Integrity: The system's ability to process data accurately and on a timely basis.
- Confidentiality: Protection of confidential information as agreed upon with clients.
- Privacy: Protection of personally identifiable information (PII).
2. Conduct a Risk Assessment A thorough risk assessment is at the core of SOC 2. You must identify potential threats to your systems and data, evaluate their likelihood and impact, and then design controls to mitigate those risks.
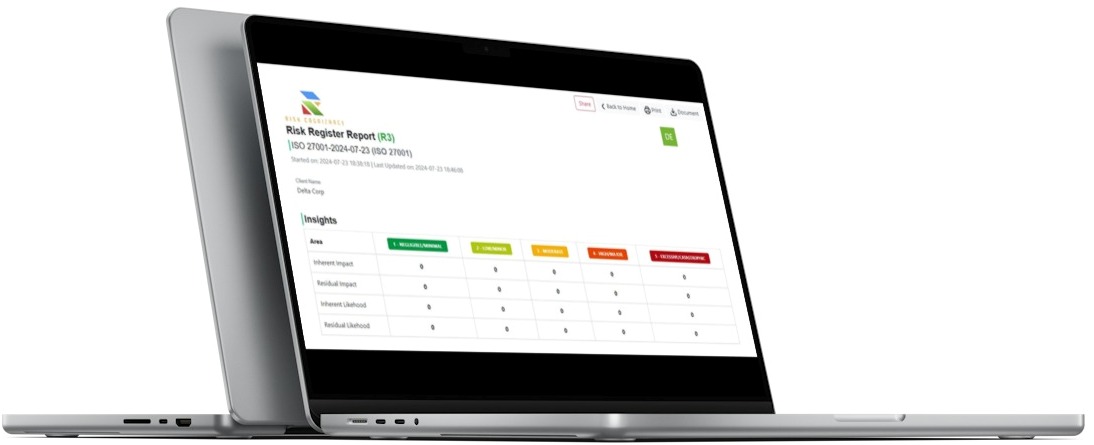
Leveraging a GRC Platform for Risk Assessment: A GRC platform can be invaluable here. It provides a structured framework for identifying and documenting risks, often with pre-configured SOC 2 specific risks and controls. The platform helps you:
- Risks to Controls: It allows you to directly link identified risks to the specific security controls you will implement, creating a clear and defensible audit trail.
- Automate Assessments: The platform can guide you through the risk assessment process, ensuring no critical areas are missed.
- Create a Centralized Register: All risks and controls are logged in a single, accessible register, making it easy to trace and verify for auditors.
3. Implement Controls and Policies Based on your risk assessment, you will implement the necessary controls and formalize them in written policies and procedures. These include technical controls (e.g., multi-factor authentication, encryption) and operational controls (e.g., employee background checks, security awareness training).
4. Perform a Gap Analysis Before the official audit, a readiness assessment or gap analysis is highly recommended. This involves a self-evaluation or a third-party review of your controls against the selected TSCs to identify any weaknesses or "gaps" that need to be addressed.
Phase 2: The Audit
The audit itself is a formal process conducted by an independent CPA firm.
- 1. Auditor Selection Choose a reputable firm with experience in your industry. The auditor's role is to assess the design and, for a Type 2 report, the operating effectiveness of your controls.
- 2. Evidence Collection The auditor will request evidence to prove your controls are in place and working. This is where a GRC platform truly shines.
Leveraging a GRC Platform for Evidence Collection:
- Automated Collection: The platform can automatically collect evidence from your various systems (e.g., HR platforms for onboarding, cloud providers for security configurations), eliminating the need for manual data gathering and screenshots.
- Centralized Repository: All evidence is stored in a single location, organized by control, making it incredibly easy for auditors to access and review.
- Verifiable Audit Trail: The platform maintains an immutable record of all changes, actions, and evidence, which builds confidence and credibility with the auditor.
3. Auditor Fieldwork The auditor will review the provided evidence, interview key personnel, and perform their own tests to verify that your controls are designed appropriately (Type 1) and are operating effectively over the review period (Type 2).
Phase 3: Continuous Monitoring and Improvement
A Type 2 SOC 2 report covers a period of time (typically 6-12 months). This means compliance is not a one-time event; it is an ongoing effort.
1. Continuous Monitoring After the initial audit, you must continue to monitor your controls to ensure they remain effective. The security landscape is constantly changing, so your controls must adapt.
Leveraging a GRC Platform for Continuous Monitoring:
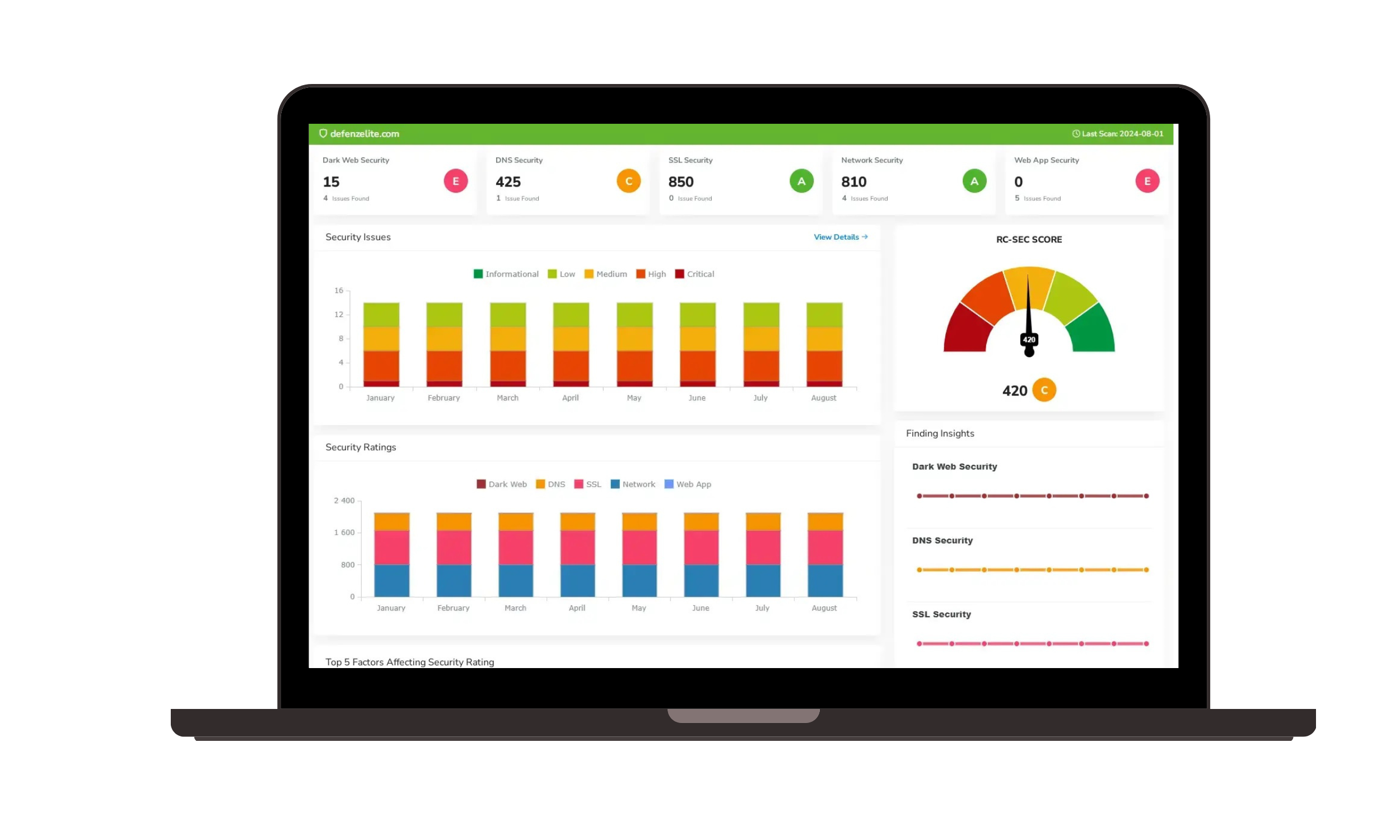
- Real-time Visibility: A GRC platform provides a real-time dashboard of your compliance posture, allowing you to see the status of every control at a glance.
- Automated Alerts: If a control fails or a configuration changes, the platform can send immediate alerts to the control owner for remediation, ensuring you can address issues before they become a problem.
- Simplified Reporting: The platform automates the generation of reports, making it easy to track and report on your compliance status.
2. Remediation If any deficiencies are found during continuous monitoring, or from a readiness assessment, they must be fixed promptly. A GRC platform can help by creating a clear workflow for remediation, assigning tasks, and tracking progress.
3. Re-certification To maintain your SOC 2 compliance, you will undergo re-certification audits on a regular basis. The documentation and processes you've established and maintained with the help of a GRC platform will make subsequent audits significantly faster and less burdensome.
What is SOC 2?
SOC 2, or System and Organization Controls 2, is a voluntary compliance standard developed by the American Institute of Certified Public Accountants (AICPA). It's an auditing procedure that ensures service organizations can securely manage customer data to protect the interests of both the organization and its clients.
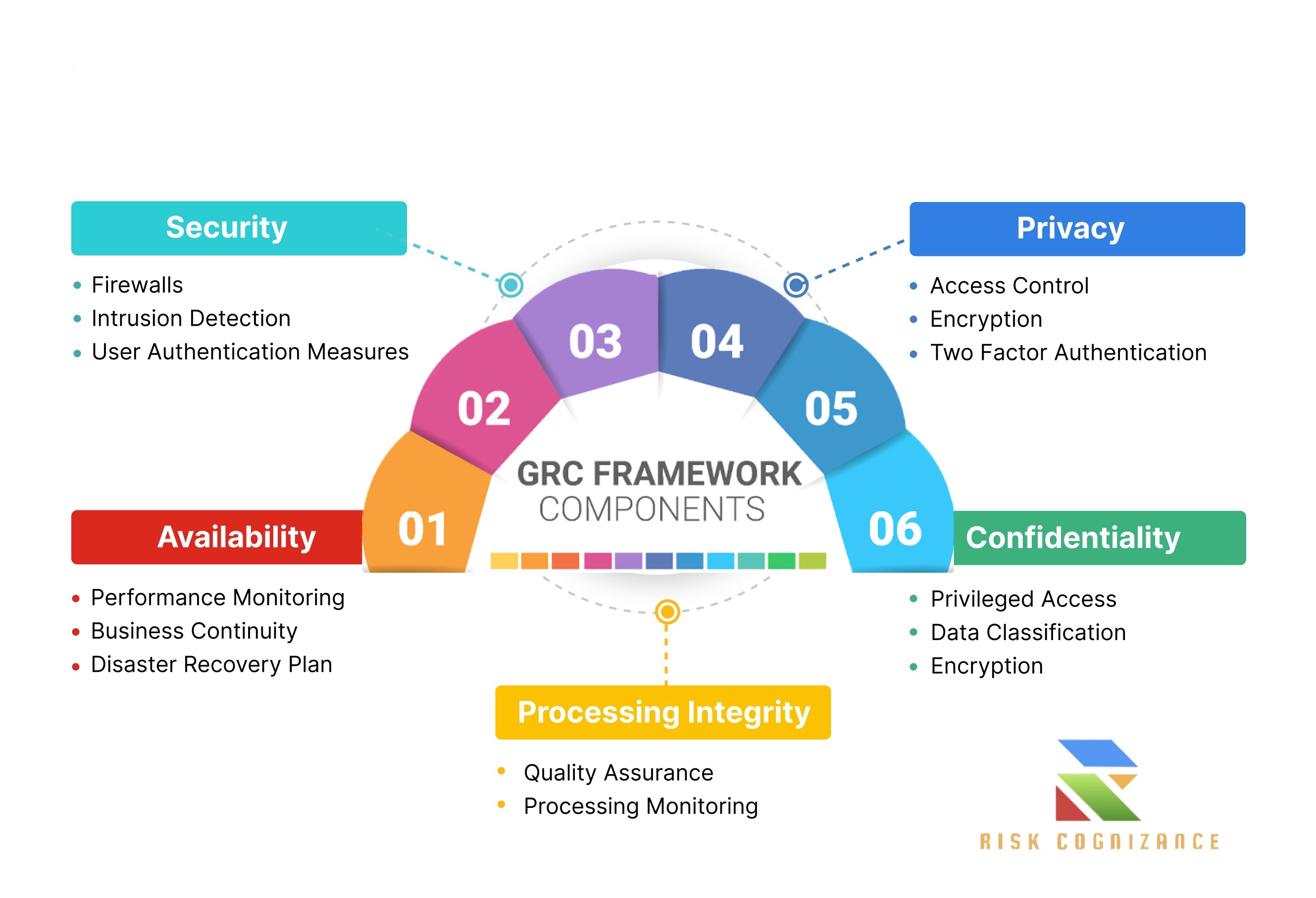
A SOC 2 report, issued by an independent CPA firm, provides assurance that a company's internal controls meet the criteria for one or more of the five Trust Services Criteria (TSCs):
- Security (Mandatory): Protection against unauthorized access, disclosure, and modification of system resources.
- Availability: The system's ability to be used for its intended purpose, as stipulated by a contract or service level agreement (SLA).
- Processing Integrity: The system's ability to process data accurately, completely, and in a timely manner.
- Confidentiality: The protection of confidential information as agreed upon with clients.
- Privacy: The protection of personally identifiable information (PII) as defined by an organization's privacy notice and the AICPA's Generally Accepted Privacy Principles (GAPP).
There are two types of SOC 2 reports:
Type 1: Describes a vendor's systems and whether their design is suitable to meet the relevant TSCs at a single point in time.
Type 2: Details the operational effectiveness of those systems over a period of time (typically 6-12 months), offering a more robust level of assurance.
How do GRC Platforms like Risk Cognizance Automate SOC 2 Compliance?
GRC platforms are designed to simplify and automate the complex and often manual process of achieving and maintaining SOC 2 compliance. Risk Cognizance, as a hybrid GRC platform, uses AI-powered automation to streamline the entire compliance lifecycle. Here's how it helps:
- Risk Assessment: The platform provides a structured framework for identifying, documenting, and linking risks to controls. It can offer pre-configured SOC 2-specific risks and controls, automating the assessment process and creating a centralized risk register.
- Automated Evidence Collection: GRC tools can automatically collect evidence from various sources (e.g., cloud environments, HR systems, security tools), eliminating the need for manual data gathering and saving significant time during the audit.
- Continuous Monitoring: Instead of point-in-time snapshots, a GRC platform provides real-time visibility into your compliance posture. It can monitor controls continuously and send automated alerts if a configuration changes or a control fails, allowing for proactive remediation.
- Simplified Audits: By centralizing all evidence and providing a verifiable audit trail, the platform makes it incredibly easy for auditors to access and review the necessary documentation. This can drastically reduce audit preparation time and costs.
- Policy Management: These platforms help manage the creation, approval, and distribution of security and privacy policies essential for SOC 2, ensuring consistent enforcement and employee attestation.
Phase
What Organizations can SOC 2 Help?
SOC 2 compliance is not just a certification; it's a strategic advantage that builds trust and demonstrates a commitment to data security. It is particularly relevant for service organizations that handle, store, or process customer data. This includes, but is not limited to:
- SaaS and Cloud Providers: These companies manage vast amounts of client data and are often required by their customers to demonstrate a high level of security.
- Healthcare Providers: Organizations handling Protected Health Information (PHI) must comply with regulations like HIPAA, and SOC 2 provides an excellent framework for doing so.
- Financial Institutions: Banks, payment processors, and other financial services firms are responsible for safeguarding sensitive financial data.
- E-commerce Companies: Businesses processing customer data, including payment information, need to maintain strong security and privacy controls.
- Human Resources and Payroll Companies: These organizations process sensitive employee data and must protect its privacy and confidentiality.
Ultimately, any organization that wants to build credibility, attract new clients, and mitigate the risk of data breaches can benefit from pursuing SOC 2 compliance.


