
Service Organization Control (SOC) Reports Explained: A Complete Guide
Service Organization Control (SOC) Reports Explained: A Guide to Understanding & Achieving Compliance
In today's interconnected business world, organizations frequently rely on third-party service providers for critical functions like cloud hosting, data processing, payroll, and more. While outsourcing offers significant benefits, it also introduces inherent risks, particularly concerning the security and integrity of customer data. This is where Service Organization Control (SOC) Reports become indispensable.
Developed by the American Institute of Certified Public Accountants (AICPA), SOC reports are independent audit reports that provide assurance about the controls at a service organization relevant to the security, availability, processing integrity, confidentiality, or privacy1 of the data it processes on behalf of its user entities (clients). These reports are a crucial tool for building trust and demonstrating a commitment to robust internal controls.
What is a SOC Report?
A SOC report is an attestation report from an independent Certified Public Accountant (CPA) firm. It verifies that a service organization has appropriate controls in place to protect its clients' data. It's a formalized way for service organizations to demonstrate their adherence to best practices in how they handle information.
It's important to note that a SOC report is not a certification, but rather an attestation. The auditor provides an opinion on the fairness of the service organization's description of its system and the suitability of the design2 and, in some cases, operating effectiveness of its controls.
Why are SOC Reports Important?
SOC reports serve several critical purposes:
- Builds Trust and Confidence: They assure existing and prospective clients that their data is handled securely and reliably, often a prerequisite for business partnerships.
- Facilitates Due Diligence: User entities use SOC reports to evaluate risks associated with outsourcing services, aiding in their vendor risk management processes.
- Meets Regulatory Requirements: Many industries and regulations (e.g., HIPAA, GDPR) implicitly or explicitly require service organizations to demonstrate strong internal controls, which SOC reports help fulfill.
- Reduces Redundant Audits: A single SOC report can satisfy the needs of multiple clients, saving time and resources for both the service organization and its clients.
- Differentiates in the Market: Having a SOC report is a significant competitive advantage, signaling a strong commitment to security and operational excellence.
- Improves Internal Controls: The preparation process often leads to identifying and remediating control gaps, strengthening the service organization's overall security posture.

Types of SOC Reports
The AICPA offers different types of SOC reports, each designed for a specific purpose and audience:
SOC 1 Report (Report on Controls at a Service Organization Relevant to User Entities’ Internal Control Over Financial Reporting3 - ICFR)
- Focus: Controls at a service organization that could affect a user entity's financial reporting (e.g., payroll processing).
- Audience: Primarily user entities' management and their financial statement auditors. These reports are confidential.
- Types:
- Type 1: Describes the system and suitability of control design at a specific point in time.
- Type 2: Describes the system and suitability of control design and operating effectiveness over a specified period (typically 6-12 months), including auditor testing results.
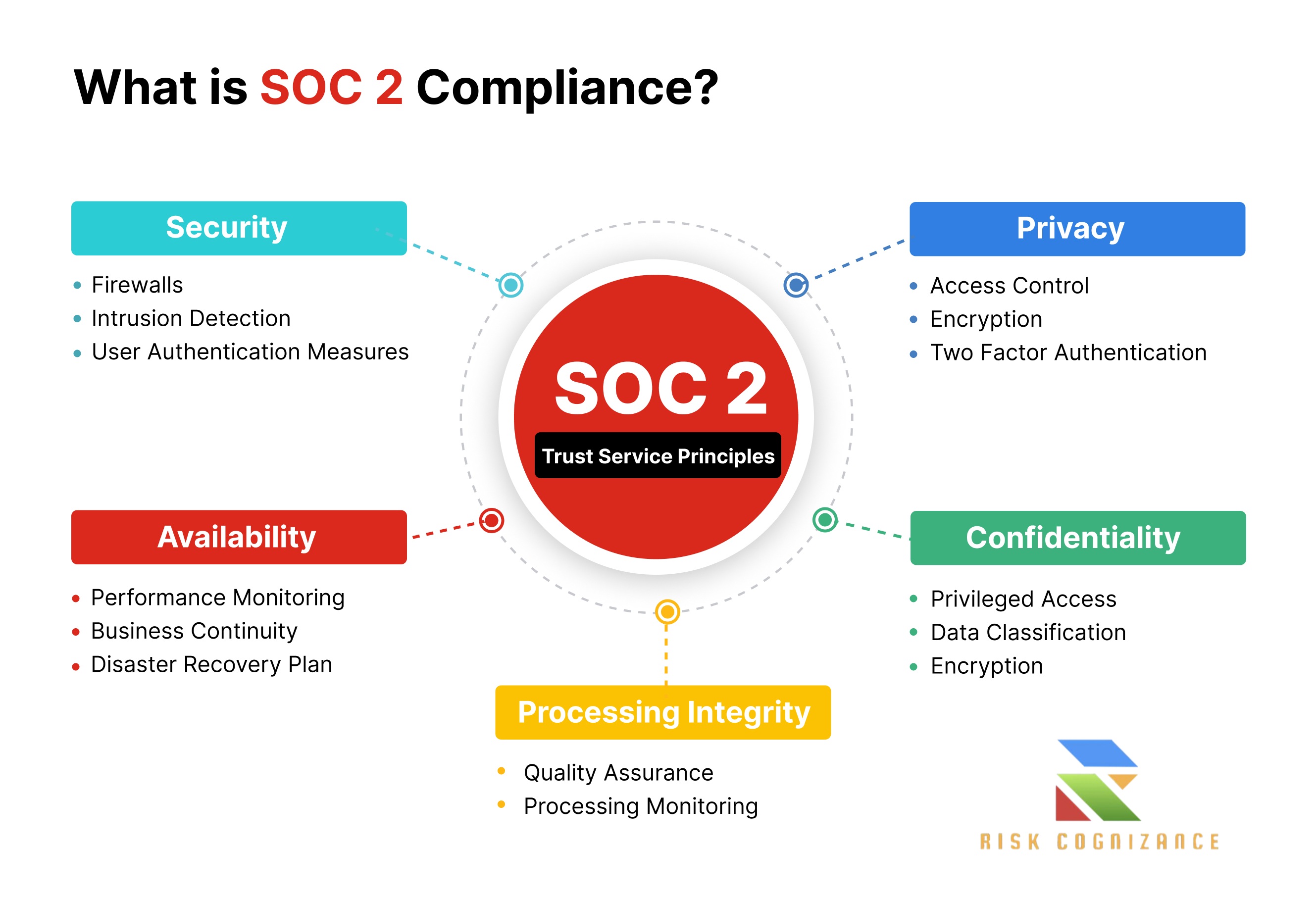
SOC 2 Report (Report on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy)
- Focus: The most common SOC report for technology and cloud service providers. It evaluates controls relevant to one or more of the AICPA's Trust Services Criteria (TSCs).
- Audience: User entities' management, business partners, prospective customers, and other specified parties. These reports are generally confidential and shared under an NDA.
- Trust Services Criteria (TSCs):
- Security (Common Criteria): Mandatory for all SOC 2 reports. Protects information and systems against unauthorized access, disclosure, and damage.
- Availability: Ensures system availability for operation and use (e.g., uptime, disaster recovery).
- Processing Integrity: Ensures system processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Protects information designated as confidential (e.g., intellectual property).
- Privacy: Addresses the collection, use, retention, disclosure, and disposal of Personal Identifiable Information (PII).
- Types:
- Type 1: Assesses the design of controls at a specific point in time.
- Type 2: Assesses the design and operating effectiveness of controls over a specified period (typically 6-12 months), including auditor test results. This is the most sought-after type.
SOC 3 Report (Trust Services Report for General Use)
- Focus: A high-level summary of a SOC 2 Type 2 report, less detailed, without specific control descriptions or test results.
- Audience: General public, prospective customers, and other interested parties needing a general understanding.
- Use: Often used for marketing or posted publicly.
Other Specialized SOC Reports:
- SOC for Cybersecurity: Focuses on an entity's cybersecurity risk management program.
- SOC for Supply Chain: Addresses risks related to manufacturing, production, or distribution systems.
_1747653647.png)
Steps to Get a SOC Report (General Process, often for SOC 2)
Obtaining a SOC report, especially a SOC 2 Type 2, is a rigorous process:
- Define Scope: Identify services, systems, and relevant Trust Services Criteria (for SOC 2).
- Readiness Assessment (Recommended): Conduct a gap analysis to evaluate current controls and identify deficiencies.
- Implement and Remediate Controls: Address identified gaps, develop policies, and gather evidence. This is where SOC 2 compliance automation software is invaluable.
- Choose an Independent Auditor: Select a qualified, independent CPA firm.
- Audit Period & Data Collection: Define the audit period (for Type 2, typically 6-12 months) and continuously collect evidence.
- Auditor's Testing: The auditor performs tests (interviews, observations, document reviews, system testing).
- Report Preparation & Review: The auditor drafts the report for your review.
- Receive and Distribute Report: Once finalized, distribute the report to stakeholders.
- Continuous Compliance: Maintain controls, update policies, conduct regular risk assessments, and undergo annual audits to stay compliant.
Streamline Your SOC 2 Journey with Risk Cognizance
Risk Cognizance provides a specialized and integrated SOC 2 Compliance Management and Reporting solution, specifically designed to automate and simplify every step of your SOC 2 journey. Our platform empowers service organizations to achieve and maintain SOC 2 compliance efficiently, reducing audit stress and demonstrating a robust security posture.
Key features of Risk Cognizance for SOC 2 Compliance:
- SOC 2 Specific Framework Mapping: Pre-built templates and mapping directly to all five Trust Services Criteria and Common Criteria, guiding you through exact requirements.
- Automated Evidence Collection: Seamlessly integrates with your existing tech stack (cloud platforms, identity providers, HR systems, ticketing, etc.) to automatically pull and organize necessary documentation and logs.
- Continuous Control Monitoring: Real-time monitoring of your controls against SOC 2 requirements, providing instant alerts for any deviations.
- Integrated Risk Assessments: Conduct comprehensive risk assessments specifically tailored to SOC 2, helping you identify, prioritize, and mitigate threats.
- Centralized Policy & Procedure Management: Create, manage, and distribute all essential security policies, with automated attestation tracking.
- Streamlined Audit Management & Reporting: Provides audit readiness dashboards, automated report generation, a secure auditor collaboration portal, and finding/remediation tracking.
- Vendor Risk Management (TPRM): Manages third-party risks effectively, addressing a key SOC 2 aspect.
- AI-Powered Insights: Utilizes AI to enhance efficiency in policy linking, risk correlation, and reporting.
- Scalable for All Sizes: Whether you're a startup needing a SOC 2 Type 1, a growing SMB needing continuous SOC 2 Type 2, or an MSP managing multiple client reports, Risk Cognizance's modular design scales to fit your specific needs, offering flexibility and cost-effectiveness.

Conclusion
SOC reports are vital for building trust and ensuring data security in today's digital economy. While the process can be challenging, leveraging a dedicated platform like Risk Cognizance for SOC 2 Compliance Management and Reporting transforms it from a daunting annual exercise into a manageable, continuous, and efficient process. By automating key tasks, providing real-time visibility, and streamlining audit interactions, Risk Cognizance empowers service organizations to achieve and maintain their SOC 2 reports with confidence and ease.


