
CMMC Explained: Cybersecurity Maturity Model Certification Guide
Cybersecurity Maturity Model Certification (CMMC) Explained: A Comprehensive Guide
The Department of Defense (DoD) established the Cybersecurity Maturity Model Certification (CMMC) program to enhance and enforce cybersecurity standards across the Defense Industrial Base (DIB). With the increasing sophistication of cyber threats targeting sensitive government information, CMMC ensures that all contractors and subcontractors handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) implement appropriate cybersecurity protections.
CMMC is not just a recommendation; it's a contractual requirement for doing business with the DoD, representing a significant shift from previous self-attestation models to a verifiable, tiered assessment process.
What is CMMC?
CMMC is a unified cybersecurity standard and certification program developed by the DoD. Its primary goal is to provide increased assurance that contractors and subcontractors are meeting the cybersecurity requirements necessary to protect sensitive unclassified information (FCI and CUI) that is shared or generated during contract performance.
The CMMC program aims to:
- Protect Sensitive Data: Safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) from increasingly complex cyberattacks.
- Standardize Cybersecurity: Provide a consistent set of cybersecurity practices and processes across the DIB.
- Enforce Compliance: Move beyond self-attestation to a verifiable assessment model.
- Strengthen the Supply Chain: Build a more resilient and secure defense supply chain.
CMMC 2.0: Streamlined and Aligned
CMMC 2.0, introduced in 2021, simplifies the original five-level model into three more streamlined levels, aligning them more closely with existing federal cybersecurity standards like NIST SP 800-171 and NIST SP 800-172. This update aims to reduce complexity and cost for the DIB while maintaining robust security.
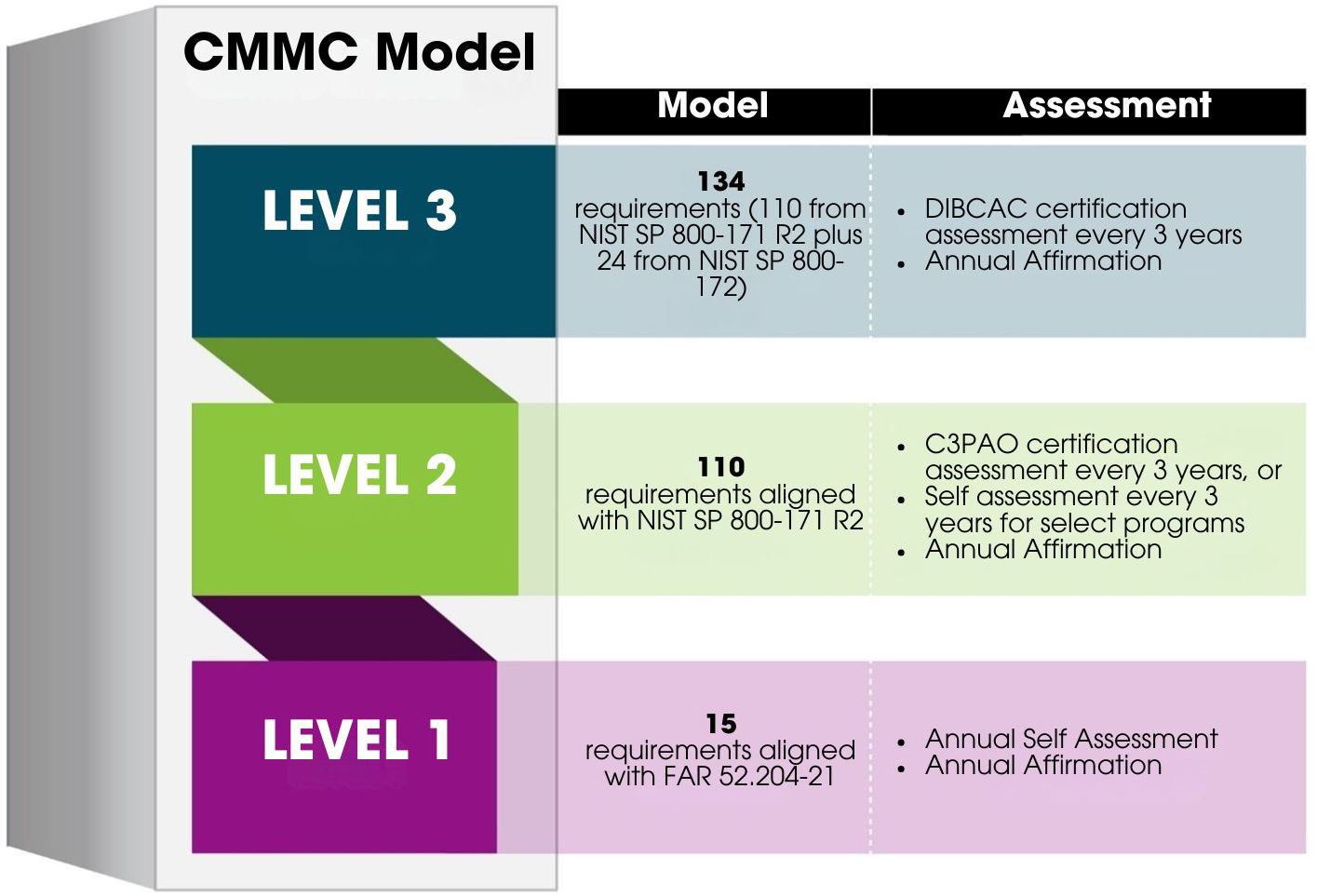
CMMC 2.0 Levels Explained
The required CMMC level for an organization depends on the type and sensitivity of the DoD information it handles.
CMMC Level 1: Foundational
- Focus: Basic cyber hygiene practices for companies handling Federal Contract Information (FCI) only. FCI is information provided by or generated for the Government under a contract that is not intended for public release.3
- Requirements: Implements 17 practices from FAR 52.204-21 (Basic Safeguarding of Covered Contractor Information Systems). These focus on fundamental cybersecurity controls like limiting system access, ensuring basic training, and securely disposing of media.
- Assessment: Requires an annual self-assessment, submitted to the DoD's Supplier Performance Risk System (SPRS).
CMMC Level 2: Advanced
- Focus: Advanced cyber hygiene practices for companies handling Controlled Unclassified Information (CUI). CUI is government-created or owned information that requires safeguarding or dissemination controls. This is the most common level for DIB contractors.
- Requirements: Implements all 110 practices from NIST Special Publication 800-171 (Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations).5
- These practices cover a broader range of security domains, including incident response, risk management, security assessment, and system and communications protection.
- Assessment:
- For critical CUI, a triennial (every three years) third-party assessment by a CMMC Third-Party Assessment Organization (C3PAO) is required.
- For less critical CUI, an annual self-assessment (similar to Level 1) may be permitted, as specified in the contract.
- All assessment results are submitted to SPRS.
CMMC Level 3: Expert
- Focus: Expert-level cybersecurity practices for companies handling highly sensitive CUI and facing advanced persistent threats (APTs).
- Requirements: Implements all 110 practices from NIST SP 800-171, plus a subset of advanced practices from NIST Special Publication 800-172. These additional practices address sophisticated threats and focus on enhanced detection, response, and recovery capabilities.
- Assessment: Requires a triennial government-led assessment (conducted by the Defense Contract Management Agency's Defense Industrial Base Cybersecurity Assessment Center - DIBCAC).

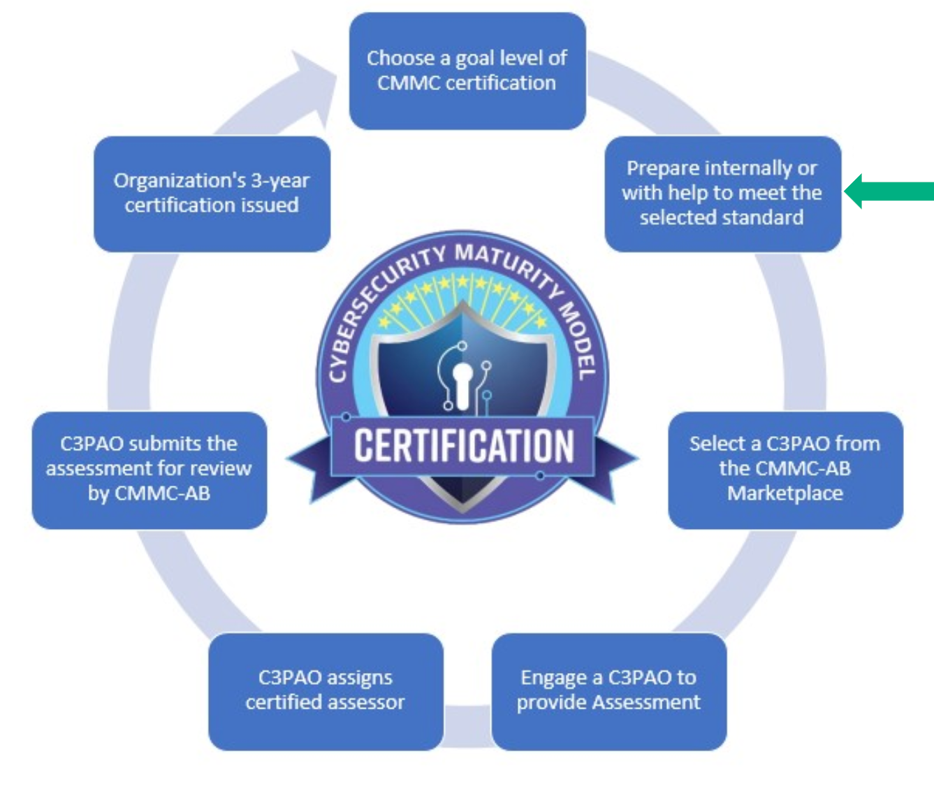
The CMMC Certification Process: Steps to Compliance
Achieving CMMC certification is a multi-step journey that requires careful planning, implementation, and ongoing management.
Determine Your CMMC Level:
- Identify the type of DoD information your organization handles (FCI or CUI) and the specific requirements outlined in your DoD contracts or anticipated solicitations. This will dictate your target CMMC level.
Conduct a Gap Analysis:
- Perform a thorough assessment of your current cybersecurity posture against the practices and processes required for your target CMMC level (e.g., NIST SP 800-171 for Level 2). This identifies existing strengths and critical gaps.
Implement and Remediate Controls:
- Based on the gap analysis, implement new security controls and remediate any deficiencies. This involves developing and updating policies, procedures, and technical configurations. This phase can be time-consuming, ranging from several months to over a year, depending on your starting point and the target level.
Develop Documentation:
- Create or update essential documentation, including a System Security Plan (SSP) that details how your organization meets the CMMC requirements, and Plans of Action and Milestones (POA&Ms) for any controls not yet fully implemented (POA&Ms are permitted for Level 2 and 3, but with specific limitations).
Prepare for Assessment:
- Conduct internal self-assessments to ensure readiness. For Level 2 and 3, prepare for the formal assessment by organizing all evidence, conducting mock interviews, and ensuring your team is ready to demonstrate compliance.
Undergo Assessment:
- Level 1 & some Level 2: Conduct your annual self-assessment and submit results to SPRS.
- Other Level 2: Schedule and undergo a triennial assessment by an accredited C3PAO.
- Level 3: Undergo a triennial government-led assessment by DIBCAC.
- The assessor will review documentation, interview personnel, and examine systems to verify the implementation and effectiveness of controls.
Address Non-Conformities (if any):
- If non-conformities are identified during the assessment, you will typically have a limited timeframe (e.g., 90-180 days) to address them and provide evidence of remediation.
Achieve Certification:
- Upon successful completion of the assessment and remediation (if necessary), your organization will receive its CMMC certification, which is valid for three years.
Maintain Continuous Compliance:
- CMMC is not a one-time event. Organizations must continuously monitor their cybersecurity posture, update controls as threats evolve, and undergo periodic assessments to maintain certification and eligibility for DoD contracts.
_1747653647.png)
Streamline Your CMMC Journey with Risk Cognizance
Navigating the complexities of CMMC compliance can be challenging, but an integrated GRC platform like Risk Cognizance can significantly simplify the process. Risk Cognizance offers specialized CMMC Compliance Management and Reporting features designed to automate and streamline your path to certification, ensuring you remain ready for DoD contracts.
Key features of Risk Cognizance for CMMC Compliance:
- CMMC Level-Specific Framework Mapping: Pre-configured mappings to CMMC Level 1 (FAR 52.204-21), CMMC Level 2 (NIST SP 800-171), and CMMC Level 3 (NIST SP 800-171 + NIST SP 800-172) practices and objectives. This provides a clear roadmap tailored to your target maturity level.
- AI-Powered Automation for Evidence Collection: Leverages AI to intelligently automate the collection of evidence from your existing IT infrastructure, cloud environments, identity providers, and other systems. This significantly reduces manual effort in gathering documentation, logs, and screenshots required for CMMC assessments.
- Continuous Monitoring of CMMC Controls: Provides real-time oversight of your cybersecurity controls and practices against CMMC requirements. Receive instant alerts on any deviations, helping you proactively address issues before an assessment.
- Integrated Risk Management Aligned with CMMC: Conduct comprehensive cybersecurity risk assessments focusing on threats and vulnerabilities to FCI and CUI. The platform helps you identify, prioritize, and mitigate risks in alignment with CMMC's risk-based approach.
- Centralized Policy & Procedure Management: A single repository for creating, managing, versioning, and distributing all necessary policies and procedures required for CMMC documentation, ensuring consistency and auditability.
- System Security Plan (SSP) & POA&M Development Support: Guides you through the creation and maintenance of your SSP, clearly mapping controls. It also facilitates the tracking and management of Plans of Action and Milestones (POA&Ms), ensuring timely remediation of gaps.
- Streamlined CMMC Assessment Preparation & Reporting:
- CMMC Readiness Dashboards: Intuitive dashboards provide a real-time view of your compliance status and progress toward CMMC readiness.
- Automated Report Generation: Compile comprehensive, audit-ready reports with all collected evidence linked directly to the corresponding CMMC practices and objectives.
- Auditor/Assessor Collaboration Portal: Securely share requested evidence and documentation with your C3PAO or DIBCAC assessor, streamlining the audit process.
- Finding & Remediation Tracking: Easily track assessment findings, assign remediation tasks, and monitor their completion, providing clear evidence of your corrective actions.
- Attack Surface Management (ASM): Proactively identifies and monitors internet-facing assets for vulnerabilities, helping you secure your external perimeter—a critical aspect of CMMC security.
- Third-Party Risk Management (TPRM): Manages cybersecurity risks associated with your supply chain and third-party vendors, which is crucial for demonstrating control over CUI flows.
- Scalable for All Organizational Sizes: Risk Cognizance's modular approach allows organizations to implement the specific features needed for their CMMC level. Whether you're a small business pursuing CMMC Level 1 self-assessment, a mid-sized contractor needing CMMC Level 2 C3PAO assessment, or a large enterprise targeting CMMC Level 3, the platform scales forward and backward to fit your current size and evolving compliance needs. This flexibility ensures you only invest in the capabilities relevant to your journey.

Conclusion
CMMC is a mandatory and evolving requirement for any organization seeking to work with the DoD. By understanding its tiered approach and implementing robust cybersecurity practices, DIB contractors can secure sensitive information and maintain their eligibility for lucrative government contracts.
Leveraging an advanced GRC platform like Risk Cognizance can significantly streamline your CMMC journey. Its automated features, comprehensive management tools, and scalable design transform the complex process into a manageable and continuous effort, empowering you to achieve and sustain CMMC certification with confidence.


