
NIST Introduces New Metric to Measure Likelihood of Vulnerability Exploits
NIST Introduces New Metric to Measure Likelihood of Vulnerability Exploits
In the relentless battle against cyber threats, understanding which vulnerabilities pose the most immediate danger is paramount. Security teams are constantly sifting through a deluge of Common Vulnerabilities and Exposures (CVEs), often relying on traditional scoring systems to prioritize patching. However, the sheer volume of vulnerabilities, coupled with the varied real-world impact, has often left organizations struggling to identify which weaknesses are truly likely to be exploited in an attack.
Recognizing this critical challenge, the National Institute of Standards and Technology (NIST) has recently unveiled a significant advancement: a new metric designed to more accurately measure the likelihood of vulnerability exploitation. This development promises to revolutionize how organizations prioritize their cybersecurity defenses, moving beyond theoretical severity to practical risk.
Beyond Severity: Why Likelihood Matters More
For years, the Common Vulnerability Scoring System (CVSS) has been the industry standard for rating vulnerability severity. While CVSS provides a valuable measure of a vulnerability's potential impact and complexity of exploitation, it doesn't directly assess the probability that it will actually be weaponized by attackers. A vulnerability might have a high CVSS score, but if no known exploits exist or if it requires a highly niche setup, its immediate threat might be lower than a medium-severity bug actively being targeted.
This gap has often led to:
- Patching Fatigue: Security teams overwhelmed by a long list of "critical" vulnerabilities, many of which may never be exploited in the wild.
- Misallocated Resources: Time and effort spent on less probable threats, diverting attention from imminent dangers.
- Reactive Security: Organizations reacting to active exploits rather than proactively defending against the most likely ones.
NIST's new metric aims to bridge this gap by providing a data-driven approach to understanding the real-world probability of exploitation, offering a more nuanced and actionable perspective on risk.
The New NIST Exploit Likelihood Metric: What It Entails
LEV Metric
Likely Exploited Vulnerabilities (LEV) probabilities—aims to address the limitations of both EPSS and the KEV catalog. While EPSS provides 30-day exploitation probabilities, it has known inaccuracies, particularly underestimating risk for already-exploited vulnerabilities. KEV, on the other hand, is limited by its reliance on known exploit data and may not be comprehensive.
LEV probabilities are designed to:
- Estimate how many and which vulnerabilities are likely to have been exploited
- Assess the completeness of the KEV catalog
- Enhance KEV-based prioritization by identifying likely-exploited vulnerabilities not yet listed
- Improve EPSS-based prioritization by correcting underestimations
Key Findings
The researchers compared LEV and EPSS scores for specific vulnerabilities, showing significant differences.
For example:
- CVE-2023-1730 (SupportCandy WordPress plugin SQL injection): before 3.1.5, the LEV probability was 0.70, while the peak EPSS score was 0.16.
- CVE-2023-29373 (Microsoft ODBC Driver RCE - Remote Code Execution vulnerability): the LEV probability was 0.54350, while the peak EPSS probability was 0.08.
The LEV analysis identified hundreds of vulnerabilities with probabilities near 1.0. However, many of these are not listed in current KEV catalogs.
While specific details of the metric's calculations are complex, the core principle involves incorporating real-world threat intelligence and contextual factors. Unlike static severity scores, this new metric is dynamic and considers:
- Existence of Public Exploits: Is there publicly available exploit code?
- Active Exploitation in the Wild: Has this vulnerability been observed as part of active attack campaigns?
- Threat Actor Capability: Is the vulnerability being exploited by sophisticated groups or commodity malware?
- Targeting Trends: Are certain industries or system types being specifically targeted?
- Ease of Exploitation: Does it require complex conditions or is it "wormable"?
By factoring in these elements, the new NIST metric aims to provide a constantly evolving score that reflects the true, current risk of a vulnerability being weaponized. It shifts the focus from "how bad could this be?" to "how bad is this likely to be right now?"
Implications for Businesses: Smarter Prioritization and Enhanced Security
For businesses navigating the treacherous cybersecurity landscape, this new NIST metric represents a significant leap forward. It offers tangible benefits that can translate into more effective and efficient security operations:
- Prioritized Patching: Instead of a flat list, organizations can prioritize vulnerabilities based on their actual likelihood of exploitation, ensuring critical resources are focused on the most imminent threats.
- Optimized Resource Allocation: Security teams can make data-driven decisions on where to invest time, tools, and personnel, maximizing the impact of limited resources.
- Proactive Threat Intelligence: The metric encourages continuous monitoring of threat landscapes and exploit developments, fostering a more proactive security posture.
- Improved Risk Communication: Security leaders can communicate risk more effectively to management by tying technical vulnerabilities to real-world probabilities, justifying security investments.
- Enhanced Continuous Monitoring: For organizations focused on continuous compliance and risk management, this metric provides a more granular view of ongoing security posture.
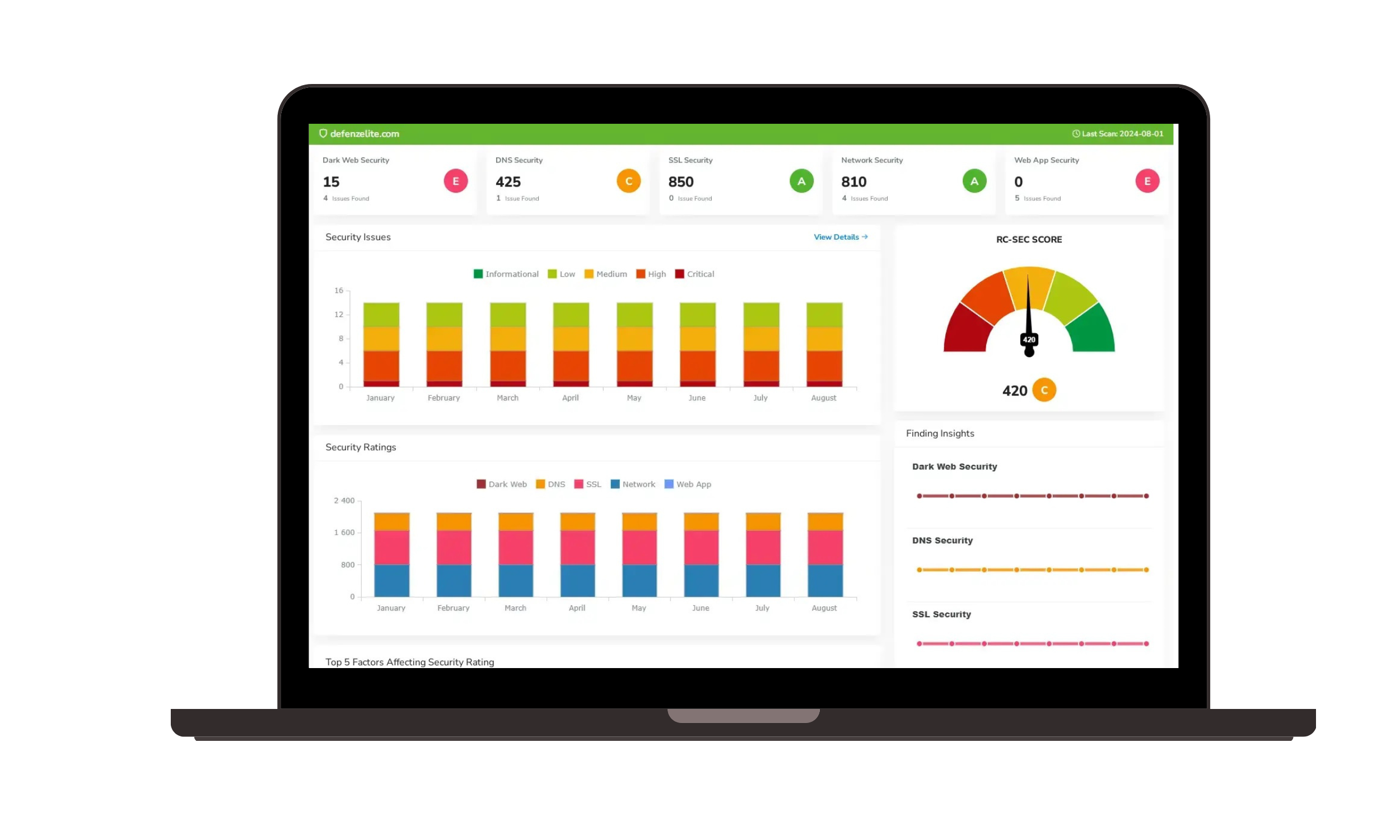
Leveraging the New NIST Metric with Risk Cognizance Platform
At Risk Cognizance Platform, we understand that effective IT & Cyber Risk Management Software must evolve with the threat landscape. Our integrated GRC platform is designed to incorporate such cutting-edge metrics, transforming raw data into actionable intelligence for our users.
Here’s how Risk Cognizance Platform can help your organization leverage NIST's new exploit likelihood metric:
- Dynamic Risk Prioritization: Integrate the new NIST metric directly into your vulnerability management workflows. Our platform can ingest this likelihood score, dynamically re-prioritizing vulnerabilities and providing immediate visibility into your most critical exposures within our Attack Surface Management (ASM) Tools.
- Automated Remediation Workflows: When a vulnerability's exploitation likelihood increases, Risk Cognizance Platform can automatically trigger remediation tasks, assign them to relevant teams, and track their progress through our Case and Incident Management Software.
- Real-time Risk Dashboards: Our Enterprise Risk Management Software will reflect the updated vulnerability likelihoods, allowing executives and risk managers to see a current, accurate picture of the organization's top cybersecurity risks.
- Continuous Monitoring & Alerts: Our IT & Cyber Compliance Management Software and Continuous Control Monitoring capabilities will continually assess your adherence to security controls and cross-reference them with the updated exploit likelihoods, alerting you to immediate threats that need attention.
- Enhanced Reporting: Generate more insightful reports for internal stakeholders and external auditors, clearly articulating your cybersecurity posture based on the most current exploitation likelihood data. This directly supports your Internal Audit Management Software functions.
- Proactive Policy Adjustments: As the understanding of exploitation likelihood evolves, our IT & Cyber Policy Management Software allows you to quickly adapt and update policies to reflect heightened risks or new mitigation strategies.

The Future of Cybersecurity Prioritization
NIST's introduction of a new metric for measuring the likelihood of vulnerability exploitation marks a pivotal moment in cybersecurity. It pushes the industry beyond simplistic severity scores towards a more intelligent, real-world understanding of risk. For organizations committed to robust Cyber Hybrid GRC Software and proactive defense, integrating this metric will be crucial.
With Risk Cognizance Platform, you can embrace this future, transforming raw vulnerability data into actionable insights that empower your teams to defend against the threats that matter most, ensuring your resources are always aligned with your most pressing risks. The era of smarter, data-driven security prioritization is here.


