
How Ransomware Can Be Delivered : Ransomware Threats & Defenses
Ransomware Threats & Defenses: How Risk Cognizance Protects Your Business
Ransomware remains one of the most pervasive and damaging cyber threats facing businesses today. Its delivery methods are constantly evolving, exploiting both human vulnerabilities and technical weaknesses. Understanding these attack vectors is the first step toward building a robust defense.
How Ransomware Can Be Delivered
Ransomware operators employ a variety of sophisticated methods to infiltrate networks and deploy their malicious payloads:
Phishing Emails: This is the most common entry point. Cybercriminals craft deceptive emails that appear legitimate, often impersonating trusted entities like banks, colleagues, or IT support. These emails typically contain:
- Malicious Attachments: Seemingly innocuous documents (e.g., invoices, resumes, reports) embedded with hidden malware that executes when opened.
- Malicious Links: URLs that redirect users to compromised websites, initiating a "drive-by download" or exploiting browser vulnerabilities.
- Social Engineering: Tactics designed to trick recipients into revealing credentials or performing actions that lead to infection.
Exploiting Software Vulnerabilities: Attackers actively scan for and exploit known weaknesses in outdated software, operating systems, applications, and network devices.
- Unpatched Systems: Systems lacking the latest security patches are prime targets.
- Drive-by Downloads: Users unknowingly visit infected websites that automatically download ransomware by exploiting vulnerabilities in their browser or plugins.
- Exploit Kits: Automated tools hosted on malicious sites that scan a visitor's system for vulnerabilities and deploy ransomware if found.
Remote Desktop Protocol (RDP) Exploitation: RDP is a legitimate tool for remote access, but it's a frequent target for ransomware gangs.
- Weak or Stolen Credentials: Attackers gain access by brute-forcing weak RDP passwords or using credentials acquired through other breaches or phishing.
- Once access is gained, they can directly deploy ransomware, often moving laterally across the network to maximize impact.
Malvertising (Malicious Advertising): Cybercriminals embed malicious code into online advertisements displayed on legitimate websites. These ads can either redirect users to infected sites or trigger a drive-by download without any user interaction, just by being viewed.
Infected Removable Media: USB drives or other external storage devices can carry ransomware. If plugged into a system, the malware can auto-execute or be manually triggered, leading to a widespread infection.
Supply Chain Attacks: Attackers compromise a software vendor or service provider, then inject ransomware into their legitimate products or software updates. This allows the ransomware to spread to the vendor's customers, leading to a ripple effect across multiple organizations.
Software Cracks/Pirated Software: Illegitimate software often comes bundled with malware, including ransomware, posing a significant risk.
Do you want to protect your businesses from ransomware?
Recognize provides a number of tools that give the organization,a edge against threats actors such as, Attack Surface Management, Dark Web Monitoring, Third-Party and Supplier Risk Management, and a enterprise level Enterprise Risk Management Software.
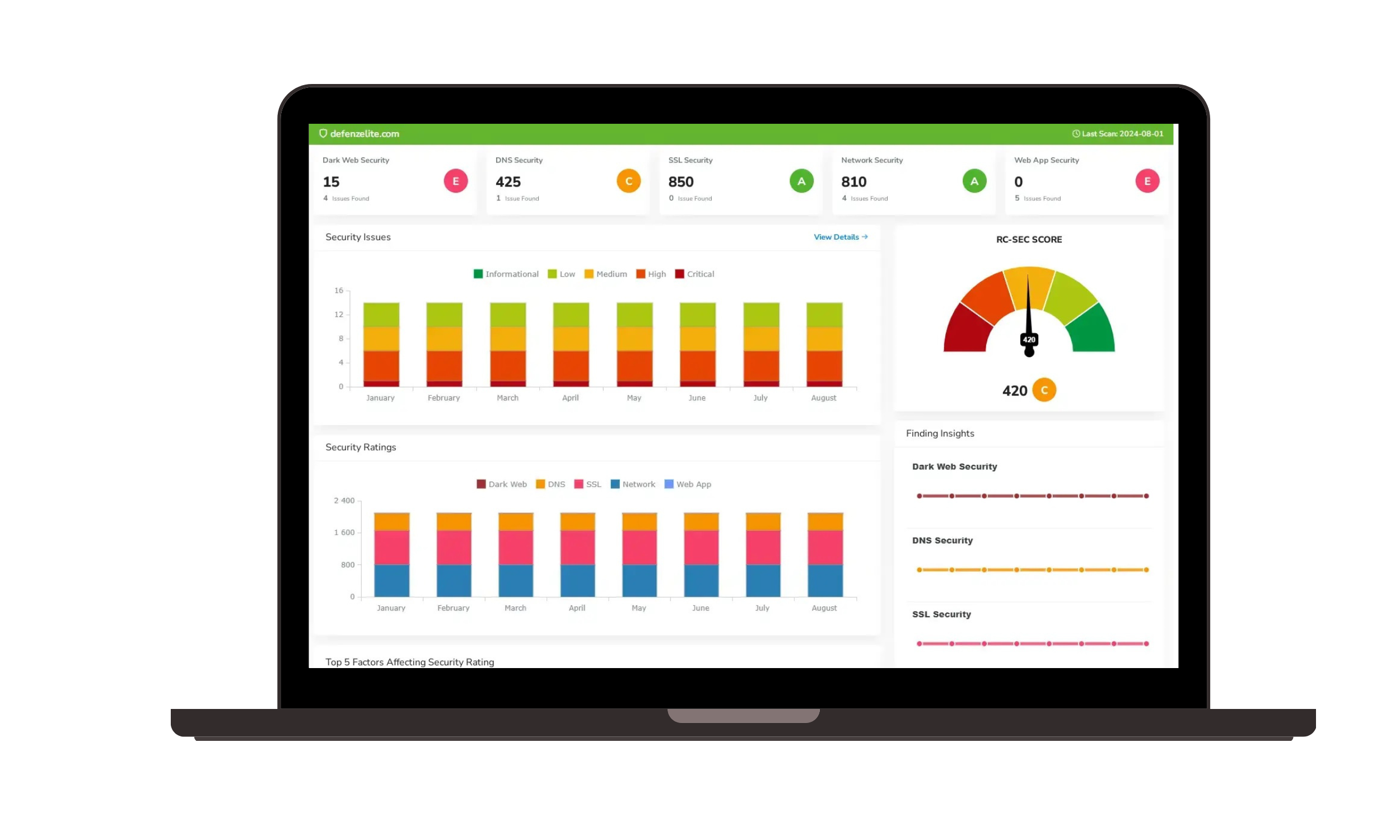
Recent Ransomware Breaches (March - May 2025)
The effectiveness of these delivery methods is evident in the continuous stream of ransomware incidents impacting organizations globally. Here are some recent notable breaches:
- Nova Scotia Power (Canada, May 2025): This critical utility confirmed a ransomware attack that resulted in a significant data breach, impacting over 280,000 individuals. The incident highlights the growing threat to essential services.
- Kettering Health (Ohio, USA, May 2025): A major healthcare system suffered a cyberattack, disrupting services and raising concerns about patient data exposure – a common outcome of ransomware in healthcare.
- DaVita (USA, April 2025): A prominent dialysis services provider experienced a ransomware attack attributed to the Interlock gang, leading to network encryption and alleged data theft, emphasizing the vulnerability of sensitive medical information.
- Hitachi Vantara (Global, April 2025): The digital infrastructure and solutions company faced a ransomware incident by the Akira group, causing operational disruptions and underscoring the risk to technology providers.
- Sheboygan, Wisconsin (USA, May 2025): City officials confirmed a ransomware attack that impacted nearly 70,000 individuals, demonstrating the ongoing targeting of municipal entities.
How Risk Cognizance Can Help Businesses Counter Ransomware
Risk Cognizance provides an integrated GRC Compliance Manager platform designed to empower businesses to proactively defend against ransomware attacks, enhance their security posture, and ensure rapid recovery. Our comprehensive solutions address the multifaceted nature of ransomware threats:
Proactive Risk Identification and Mitigation:
- Our IT & Cyber Risk Management Software helps you identify, assess, and prioritize cyber risks, including those related to ransomware attack vectors like unpatched systems and vulnerable RDP configurations.
- Cyber Hybrid GRC Software provides a unified view of your IT and cyber risks, allowing you to understand your complete attack surface and implement controls effectively.
- Attack Surface Management (ASM) proactively identifies and reduces external vulnerabilities that ransomware groups often exploit, making it harder for them to gain initial access.
Strengthening Your Defenses & Compliance:
- Policy Management Software helps you develop, deploy, and enforce robust security policies that align with best practices for ransomware prevention, including strong password policies, multi-factor authentication (MFA) mandates, and data backup protocols.
- IT & Cyber Compliance Management Software ensures adherence to industry standards (e.g., NIST, ISO 27001) that build a strong foundation against ransomware, improving your overall cyber hygiene.
- Regulatory Compliance Management Software helps you meet regulatory obligations related to data protection and incident reporting, which become critical in the aftermath of a ransomware breach.
Managing Third-Party & Supply Chain Risks:
- As supply chain attacks become more common, our Vendor Risk Management Software (TPRM) allows you to assess and continuously monitor the cybersecurity posture of your vendors and partners, reducing the risk of ransomware entering your network through third parties.
Rapid Incident Response & Recovery:
- Case and Incident Management Software provides a structured framework for managing and responding to security incidents like ransomware attacks, enabling quicker containment, eradication, and recovery.
- Internal Audit Management Software supports post-incident analysis and helps identify control weaknesses, ensuring continuous improvement in your ransomware defense strategy.
Leveraging AI for Enhanced Protection:
- Our AI-powered capabilities provide intelligent insights into your risk posture, automate vulnerability scanning, and help in mapping controls to various compliance frameworks. This allows for more dynamic and adaptive defenses against evolving ransomware tactics, including early detection of suspicious activities that might signal an impending attack.
By integrating risk management, compliance, and automated controls, Risk Cognizance empowers businesses to build a resilient defense against ransomware, safeguarding their data, operations, and reputation.


