
MSP CMMC Software: CMMC Compliance Services
MSP CMMC Services: CMMC With Risk Cognizance Compliance Manager
The Cybersecurity Maturity Model Certification (CMMC) has come into effect, and it represents one of the most significant shifts in federal contracting in decades. Thousands of businesses in the Defense Industrial Base (DIB) sector—from manufacturers to software developers—are now facing a mission-critical cybersecurity mandate. Without a certified security posture, they risk losing their eligibility for Department of Defense (DoD) contracts. For Managed Service Providers (MSPs), this isn't just a challenge; it's a monumental opportunity.
Here’s your chance to expand your MSP practice and create new recurring revenue streams by leveraging Risk Cognizance Compliance Manager — the ultimate platform to help your clients prepare for, and maintain, compliance with the various cybersecurity standards required by the DoD. Our powerful automation and white-glove support can help your clients navigate this complex landscape, securing their business for the future.
Why CMMC is an Imperative for the Defense Industrial Base
For companies that want to work with the DoD, cybersecurity is no longer an optional add-on—it is a fundamental requirement. The CMMC was published by the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD–A&S) to protect national security by securing the supply chain. This means implementing robust security frameworks to safeguard two critical forms of data prevalent across the DIB:
Federal Contract Information (FCI): Information, not intended for public release, that is provided by or generated for the government under a contract.
Controlled Unclassified Information (CUI): Government-created or-owned information that requires safeguarding or dissemination controls.
This framework builds upon existing requirements set out in the Defense Federal Acquisition Regulation Supplement (DFARS) and NIST's Special Publication (SP) 800-171. The CMMC takes these standards and adds a verification component—a third-party audit—making compliance not just a matter of self-attestation but of verified maturity.
To lock down the "preferred contractor" status that your clients need for a long and lucrative relationship with the DoD, they’ll need to implement the many complex controls of the CMMC, and they can’t do it alone.
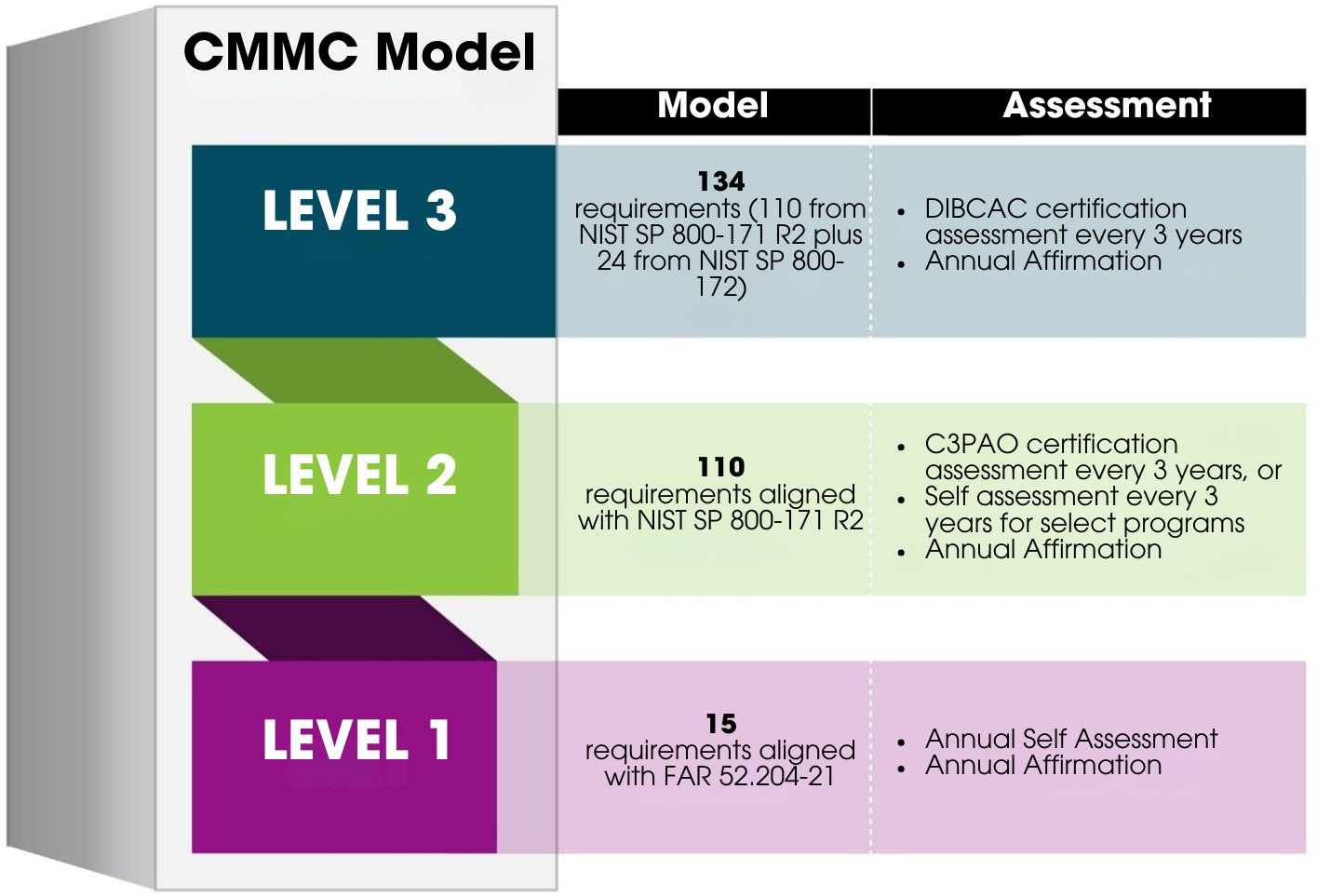
What Does CMMC Compliance Require?
The CMMC framework is a comprehensive, multi-layered approach to cybersecurity. It comprises a total of 171 "Practices" distributed across 17 "Domains" and in service of 43 "Capabilities." These controls are analogous to similar requirements in DFARS and NIST SP 800-171 but are organized differently to facilitate a maturity-based model. Unlike other frameworks, the CMMC allows for a gradual adoption of controls over five "Maturity Levels," making the journey scalable for companies of all sizes.
Let’s take a closer look at the breakdown of controls within each domain, highlighting the critical areas your MSP must address to get clients certified.
Cybersecurity Domains and Practices
The CMMC framework (version 1.02) is available for free download from the OUSD(A&S). Its core domains, sourced and adapted from this edition, break down as follows:
- Access Control (AC) & Identification and Authentication (IA): These domains are foundational. They govern how access to FCI and CUI is restricted, from user account management to the mandatory use of Multi-Factor Authentication (MFA). A powerful compliance tool will automate the management of user credentials, enforce robust password policies, and ensure role-based access is properly configured.
- Asset Management (AM) & Maintenance (MA): These domains focus on inventorying and managing all physical and digital assets connected to FCI/CUI. This includes defining protocols for both routine and special maintenance of all sensitive hardware and software. The right software helps you maintain a detailed, up-to-date asset inventory and schedule maintenance to minimize vulnerabilities.
- Audit and Accountability (AU) & Security Assessment (CA): Requiring regular audits and assessments, these domains ensure accountability across the entire organization. A strong platform helps generate the necessary audit trails, monitor logs, and provide the evidence required to demonstrate compliance with these practices.
- Awareness and Training (AT) & Personnel Security (PS): These domains specify protocols for staff security training and govern security practices related to personnel, from hiring to termination. Your CMMC solution should include automated training modules, simulated phishing campaigns, and a way to track and log employee training completion.
- Configuration Management (CM) & Systems and Communications Protection (SC): This is where you replace all default security settings with more robust, custom configurations and ensure the safe transmission of FCI/CUI across networks. A compliance tool can help automate configuration hardening, vulnerability scanning, and the enforcement of secure network protocols.
- Incident Response (IR) & Recovery (RE): These domains define the programmatic, real-time response to, and recovery from, security incidents. Your solution must provide tools for automated event identification, incident tracking, and a clear, repeatable process for resolution and recovery to ensure business continuity.
- Media Protection (MP) & Physical Protection (PE): These domains safeguard the use, movement, and disposal of sensitive media and restrict access to physical devices and workstations. Software can assist with inventory management and policy enforcement for both physical and digital media.
- Risk Management (RM): This is the strategic domain that defines a programmatic approach to the identification, analysis, and mitigation of threats and vulnerabilities. The right software provides a centralized view of risks, helping you prioritize remediation efforts and document your risk management strategy.
- System and Information Integrity (SI) & Situational Awareness (SA): These domains govern procedures to guarantee the integrity of cybersecurity infrastructure and govern expectations for staff's awareness of industry-wide threats. A comprehensive platform provides threat intelligence feeds and integrity monitoring to ensure systems are functioning correctly and securely.
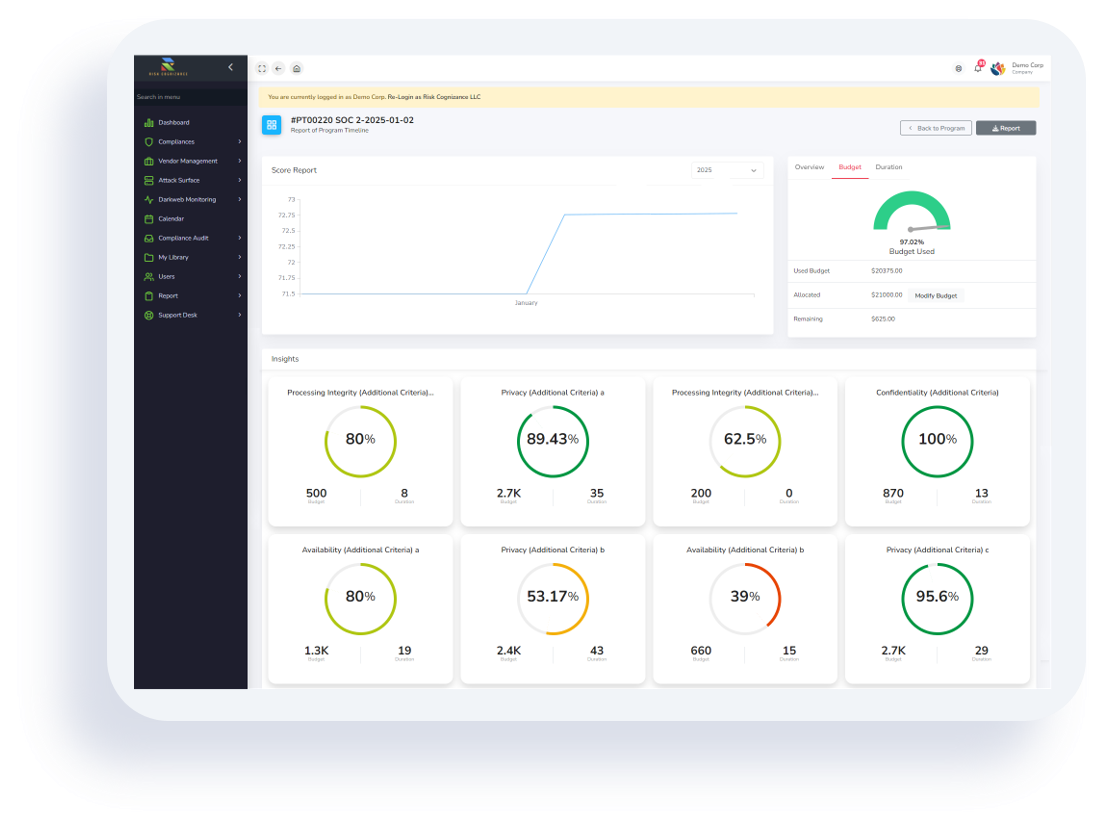
Which CMMC Compliance Tools Are Most Effective?
The best CMMC compliance tools do more than just check boxes; they provide a comprehensive toolkit that is scalable to your clients' needs. An all-in-one software and advisory service is designed to get your clients certified at any level, regardless of their current security posture.
For companies just starting on the road to DoD contracting, we begin with a gap assessment and patch reporting so they know exactly what needs to be installed and how. Then, we work with their IT team to build out any infrastructure or practices they’ll need per level. Finally, as a Certified Third-Party Assessment Organization (C3PAO) accredited by the CMMC Accreditation Body, a provider Risk Cognizance Security partners can verify your client’s model maturity when the time is right.
For companies looking for a la carte services, two particular cybersecurity areas are most impactful as software and toolkit solutions: vulnerability and incident management.
Threat and Vulnerability Management
One of the most essential parts of an effective cybersecurity architecture is a programmatic approach to threat and vulnerability management. These tools are designed to continuously monitor, analyze, and mitigate risks in a manner that meets CMMC requirements. Whether your client handles this internally or externally, your CMMC software must support the following practices:
- Continuous Monitoring: Inventory monitoring and analysis for all cyber assets, users, and behaviors.
- Threat Intelligence: The collection and mobilization of threat intelligence from across your client's industry.
- Risk Assessments: The capability to conduct routine and special event risk and vulnerability assessments, with comprehensive logging.
- Penetration Testing: Support for penetration testing and root cause analysis.
- Integration: Seamless integration into your client's existing infrastructure to provide detection and response capabilities.
Incident Response and Management
Prevention is an essential element of a robust cybersecurity program, but it's only one domain of the CMMC framework. Companies also need to prepare for attacks that occur, which is why incident management is so important. Through software and other tools, incident management must cover six essential components:
- Event Identification: The immediate classification of an attack or other incident.
- Incident Inventory: Registration and tracking of the threat as it moves through the response lifecycle.
- Investigation Process: A documented, real-time analysis and planning phase for mitigation.
- Assignment of Controls: The designation of individual and group responsibilities for handling the incident.
- Security Event Resolution: The execution of a planned incident response to contain and eliminate the threat.
- Customer Satisfaction: For MSPs, this means the maintenance of a satisfactory customer relationship, including timely communication and reporting.
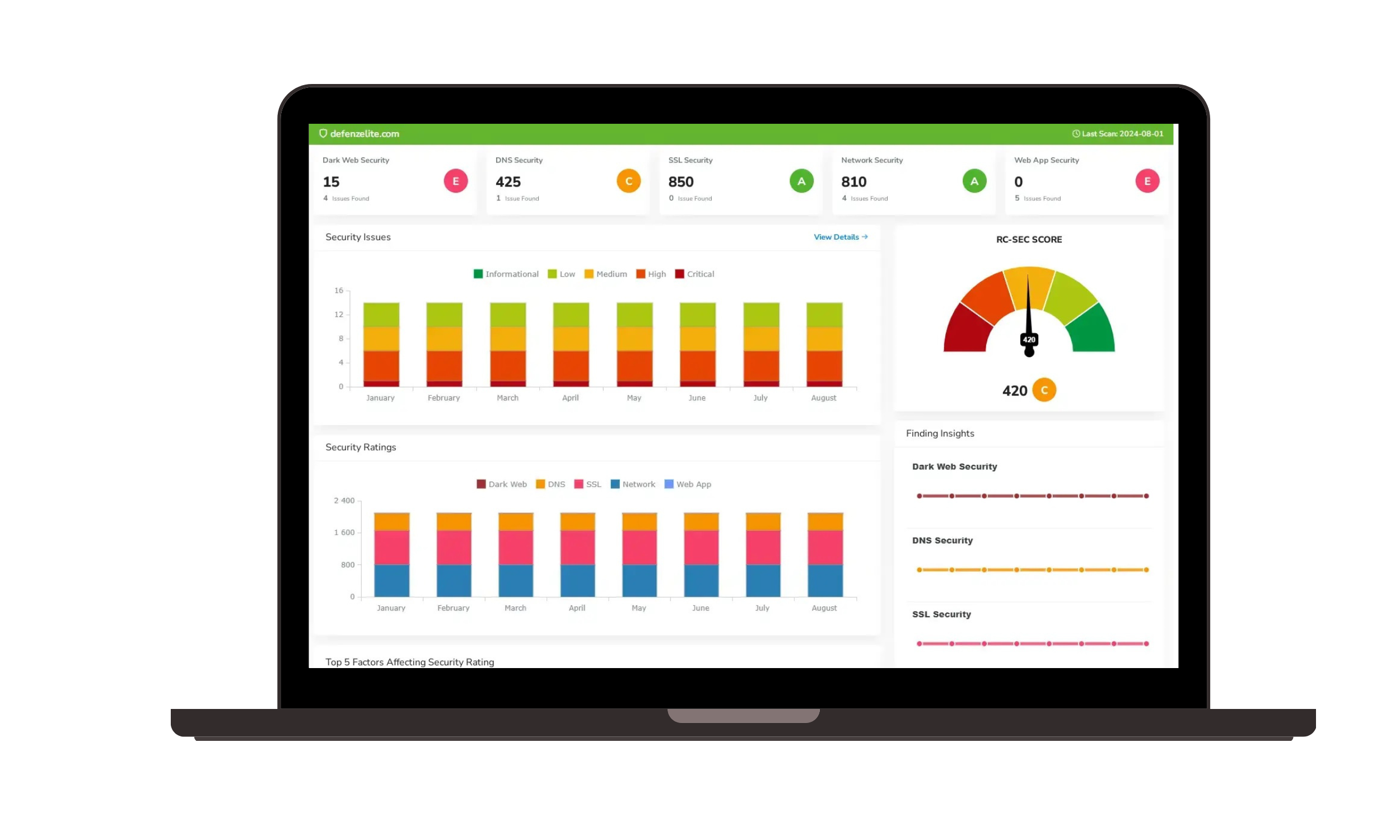
The Strategic Partner Advantage: Professional CMMC Services
The primary benefit of working with a professional service provider like Risk Cognizance Security partners can streamlined, integrated security solution. We make even the most complex compliance aspects simple by combining our powerful software with decades of collective cybersecurity experience. Your service offerings can span well beyond just compliance, into all elements of cybersecurity awareness, infrastructure, and maintenance.
By leveraging Risk Cognizance Compliance Manager, you can offer a comprehensive, white-glove service that not only helps your clients achieve a CMMC certification but also enhances their overall security posture, positioning them as a highly secure and reliable partner in the DIB.


