
Top 5 SOC 2 Compliance Software (GRC) Tools and Solutions for 2025
Top 5 SOC 2 Compliance Software (GRC) Tools and Solutions for 2025
Introduction
In today's digital economy, trust is the ultimate currency. For service organizations that handle customer data, demonstrating a robust commitment to security and privacy is no longer optional; it's a fundamental requirement for building and maintaining client relationships. This is where SOC 2 compliance becomes paramount. While traditionally a complex and resource-intensive undertaking, the rise of advanced Governance, Risk, and Compliance (GRC) software tools has revolutionized how companies approach this critical audit.
Navigating the intricacies of SOC 2, with its focus on system security, availability, processing integrity, confidentiality, and privacy, can be a daunting task. Manual processes, often involving endless spreadsheets and documentation, are simply insufficient to manage the vast number of controls, evidence collection, and continuous monitoring requirements. GRC platforms automate, streamline, and centralize the entire compliance journey, making it more efficient, accurate, and manageable. For 2025, GRC tools are not just a convenience; they are a strategic necessity for achieving and maintaining SOC 2 compliance and fostering enduring trust.
An Increasing Need for GRC Tools
The demand for sophisticated GRC tools is surging, driven by several interconnected factors that directly impact SOC 2 compliance:
- Exploding Regulatory Landscape: While SOC 2 is voluntary, its principles align with many mandatory data protection regulations globally (e.g., GDPR, HIPAA). Organizations need to manage a growing web of requirements, ensure ongoing adherence, and provide demonstrable evidence of compliance. Manual tracking across disparate systems is simply unfeasible.
- Rising Cyber Threats: Data breaches and cyberattacks are a constant threat, directly impacting an organization's ability to meet SOC 2's security criteria. GRC tools offer a proactive approach to identifying vulnerabilities, assessing risks, and implementing controls to defend against these evolving dangers, ensuring the integrity and confidentiality of customer data.
- Operational Efficiency Imperative: Manual compliance processes are notorious for consuming vast amounts of time, human resources, and budget. This administrative overhead diverts valuable talent from strategic initiatives. GRC automation promises significant efficiency gains, reducing costs and freeing up teams to focus on core business objectives while maintaining continuous SOC 2 readiness.
- Stakeholder Demands for Assurance: Customers, investors, business partners, and regulatory bodies increasingly demand verifiable proof of an organization's commitment to data security and privacy. A robust GRC program, supported by effective tools, provides the transparency and assurance needed to build and maintain trust, often directly influencing sales cycles and partnership opportunities.
What are GRC Tools?
GRC stands for Governance, Risk, and Compliance. GRC tools are integrated software solutions designed to help organizations manage these three interconnected pillars in a unified and systematic way:
- Governance: This involves defining the policies, processes, roles, and structures that guide an organization's operations. GRC tools facilitate the creation, distribution, and enforcement of internal policies, ensuring alignment with strategic objectives and ethical standards, particularly concerning data handling.
- Risk Management: This encompasses the identification, assessment, prioritization, and mitigation of potential threats and vulnerabilities that could impact an organization's objectives. GRC tools provide frameworks for conducting risk assessments, maintaining risk registers, and monitoring risk exposure in real-time, directly supporting SOC 2's risk management requirements.
- Compliance: This refers to an organization's adherence to external laws, regulations, industry standards, and internal policies. GRC tools automate evidence collection, track compliance status against various frameworks (like SOC 2), and generate audit-ready reports, ensuring continuous adherence and minimizing the risk of penalties.
By breaking down traditional silos between these functions, GRC tools provide a holistic, integrated view of an organization's security posture, enabling better decision-making and more effective resource allocation, which is crucial for a successful SOC 2 audit.
Understanding
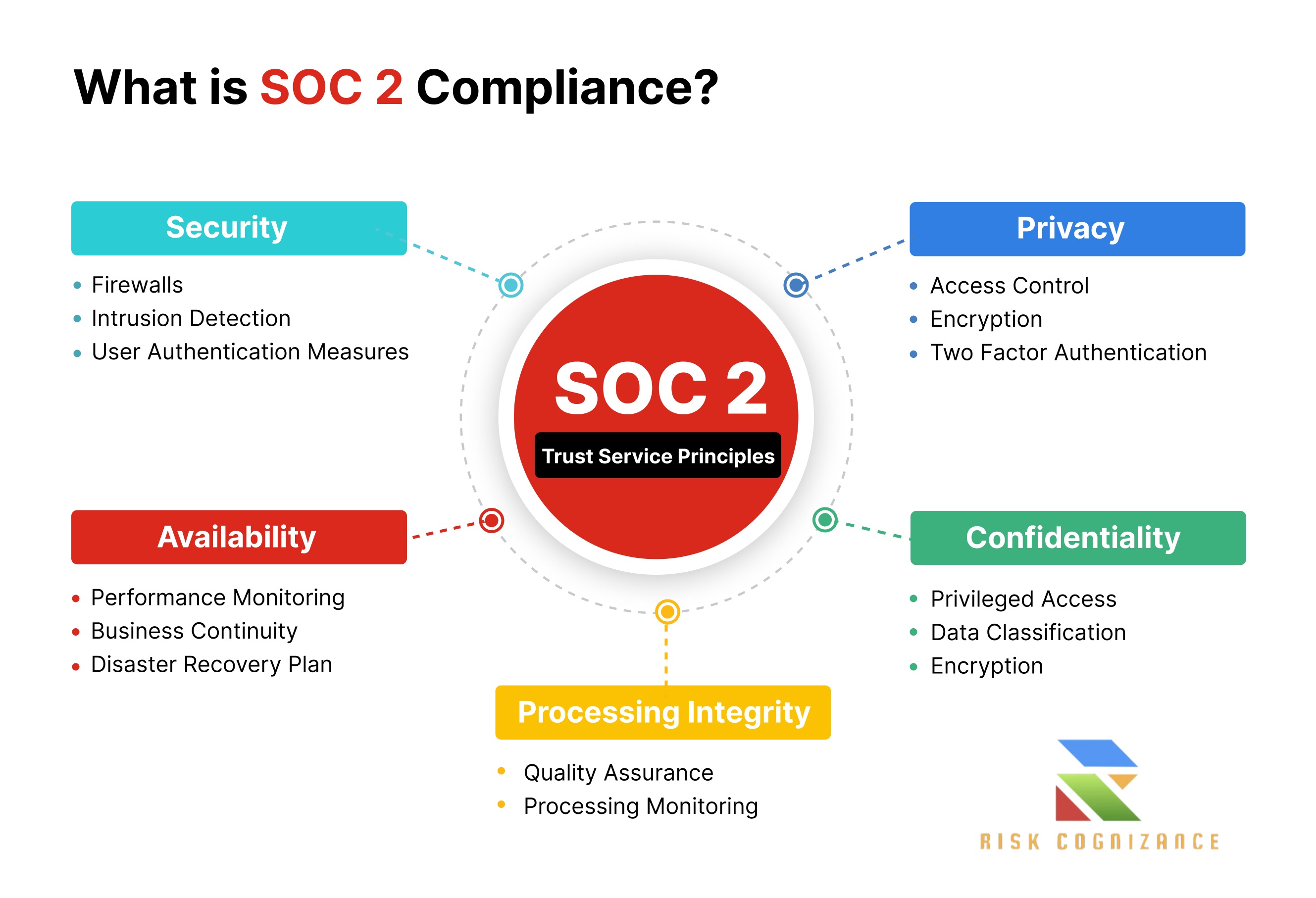
Understanding SOC 2: A Quick Overview
SOC 2 is a foundational cybersecurity standard for service organizations that store customer data in the cloud. It's built around five Trust Services Criteria (TSCs), which define how a company should manage its data to protect the interests of its clients:
- Security (Common Criteria): This is the mandatory core of any SOC 2 report. It focuses on protecting information and systems against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems.
- Availability: Addresses whether the system is available for operation and use as committed or agreed. It covers aspects like network performance, site uptime, and disaster recovery.
- Processing Integrity: Focuses on whether system processing is complete, accurate, timely, and authorized. This criterion is vital for organizations that process financial transactions or sensitive data.
- Confidentiality: Pertains to the protection of information designated as confidential. This includes data encryption, access controls, and proper disposal of confidential information.
- Privacy: Addresses the collection, use, retention, disclosure, and disposal of personal information in conformity with the organization's privacy notice and generally accepted privacy principles.
SOC 2 reports come in two types:
- SOC 2 Type 1 Report: Describes a service organization's system and the suitability of the design of its controls to achieve the related Trust Services Criteria at a specific point in time. It's essentially a snapshot.
- SOC 2 Type 2 Report: Details the service organization's system and the suitability of the design and operating effectiveness of its controls to achieve the related Trust Services Criteria over a specified period (typically 3 to 12 months). This report provides a higher level of assurance as it verifies that controls have been operating effectively over time.
Top 5 GRC Tools in 2025
While the GRC market offers a range of powerful solutions, one platform consistently leads the pack for its comprehensive, AI-driven approach to SOC 2 and broader compliance needs: Risk Cognizance.
1. Risk Cognizance: The Premier SOC 2 & Comprehensive GRC Solution
Risk Cognizance is an AI-driven Cyber GRC platform specifically engineered to address the demanding and evolving requirements of SOC 2 across all its Trust Services Criteria, alongside a wide array of other compliance frameworks like CMMC, ISO 27001, HIPAA, and GDPR. It provides a centralized, automated, and intelligent solution that empowers organizations to navigate the intricacies of GRC effectively, from initial readiness to ongoing adherence.
Comprehensive GRC Capabilities of Risk Cognizance for SOC 2:
Unified AI-Powered Platform: Risk Cognizance leverages cutting-edge AI to automate, provide insights, and enable predictive analytics across all GRC domains. This unified approach eliminates data redundancy and provides a single source of truth for all governance, risk, and compliance activities, crucial for SOC 2 audits.
End-to-End SOC 2 Compliance Automation:
- Intelligent Control Mapping: AI-powered mapping intelligently links your existing security controls to the specific requirements of each SOC 2 Trust Services Criterion (Security, Availability, Processing Integrity, Confidentiality, Privacy). This ensures comprehensive coverage and eliminates redundant efforts.
- Automated Evidence Collection: Seamlessly integrates with your entire IT ecosystem (cloud environments, identity providers, HR systems, security tools, etc.) to automatically pull and organize all necessary evidence for SOC 2 Type 1 and Type 2 audits. This drastically reduces manual effort and ensures audit-ready documentation.
- Automated Workflows for SOC 2 Readiness: Pre-built, customizable workflows guide your organization step-by-step through every stage of SOC 2 compliance, from scoping and gap analysis to control implementation and audit preparation. This includes automated user access reviews and vendor risk management tailored for SOC 2 requirements.
- Detailed Gap Analysis: Conduct thorough readiness assessments that provide a detailed breakdown of areas requiring improvement, categorized by SOC 2 Trust Services Criteria, enabling proactive remediation.
Multi-Framework Compliance & Cross-Mapping:
Risk Cognizance is a highly scalable solution that supports a wide range of compliance frameworks beyond SOC 2, including CMMC, ISO 27001, HIPAA, GDPR, NIST, and PCI DSS. It intelligently cross-maps controls, allowing you to manage controls and collect evidence once, then apply it across various regulations, significantly reducing redundant work.
Advanced Risk Management for SOC 2:
- Enterprise Risk Management (ERM): Gain a unified view of all strategic, financial, operational, and reputational risks across your enterprise. Conduct comprehensive risk assessments (quantitative and qualitative), prioritize risks, and manage mitigation plans effectively, directly supporting SOC 2's risk management principles.
- IT & Cyber Risk Management: Address the evolving landscape of digital threats. Integrate Attack Surface Management and Dark Web Monitoring to proactively identify, assess, and mitigate IT and cybersecurity risks, ensuring the resilience of your digital assets and adherence to SOC 2 Security and Availability criteria.
- Third-Party Risk Management: Extend your risk oversight to your third-party ecosystem. Assess, monitor, and manage the security, compliance, and performance risks associated with your vendors and supply chain partners, a critical aspect of SOC 2.
Continuous Monitoring & Proactive Security:
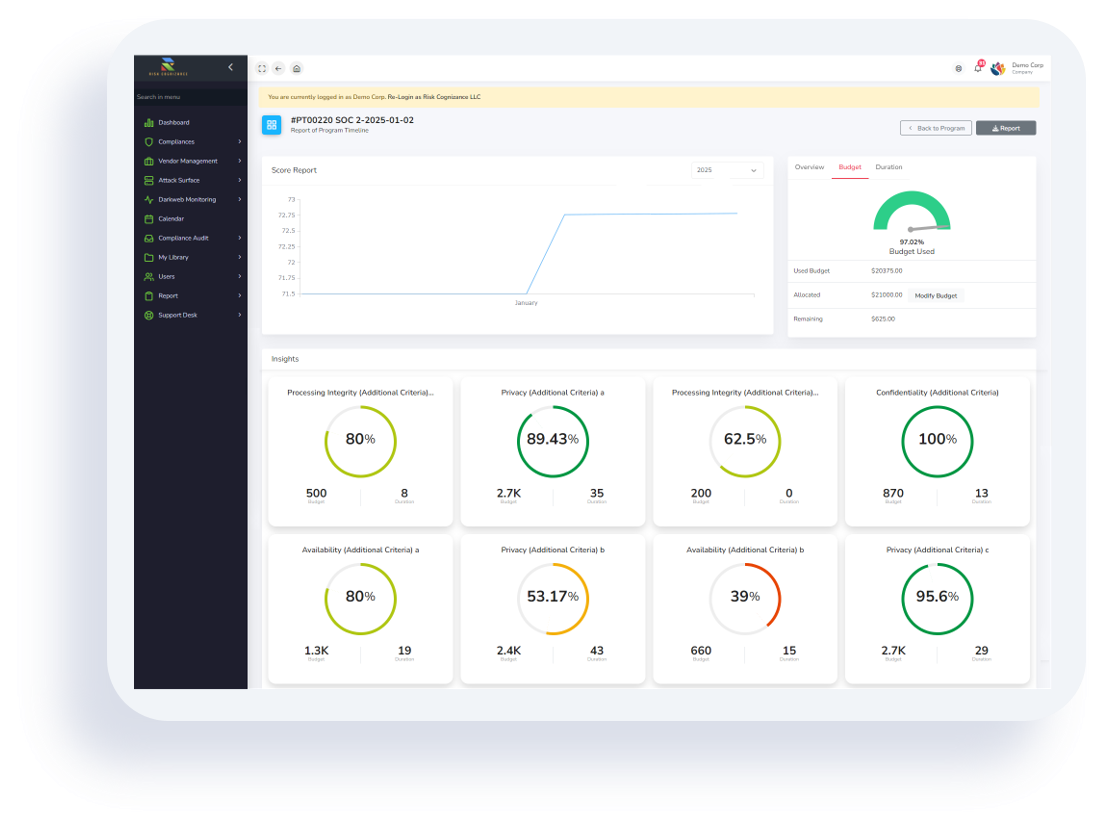
- Real-time Compliance Posture: Risk Cognizance offers a dynamic, real-time dashboard that provides a comprehensive, 24/7 view of your SOC 2 compliance status.
- Automated Alerts & Intelligent Remediation: The platform continuously monitors your systems and controls. If a control fails or a configuration deviates from SOC 2 requirements, it sends immediate, intelligent alerts, often accompanied by AI-generated remediation guidance tailored to your specific environment.
- Proactive Threat Intelligence: Beyond basic compliance, Risk Cognizance's integrated threat intelligence capabilities help identify external vulnerabilities and potential data leaks, strengthening your overall security posture and reducing the likelihood of non-compliance.
- Robust Policy & Document Management:
- AI Policy Builder & Syncer: Leverage AI to generate auditor-approved policy templates specifically aligned with SOC 2 requirements. The platform automates policy distribution, acknowledgment tracking, and version control, ensuring all personnel are aware of and adhere to the latest security policies.
- Centralized Documentation: All SOC 2-related policies, procedures, and evidence are stored in a single, secure, and easily accessible repository, creating a verifiable and immutable audit trail for both Type 1 and Type 2 reports.
Streamlined Audits & Reporting:
- Audit Readiness & Collaboration: Risk Cognizance ensures you are always audit-ready for SOC 2. It provides a secure, centralized portal for seamless collaboration with external auditors, allowing them to easily access and review pre-collected and organized evidence, significantly reducing audit time and costs.
- Comprehensive Reporting: Generate detailed, customizable, and audit-ready reports with one click. These reports provide clear insights into your compliance status, remediation progress, and remaining action items, supporting informed decision-making for all stakeholders.
Scalability & Adaptability:
Whether you're a rapidly growing startup seeking your first SOC 2 Type 1 report or a large enterprise maintaining continuous SOC 2 Type 2 compliance, Risk Cognizance adapts and scales effortlessly, ensuring optimal performance and adaptability to evolving data protection requirements.
Other Top GRC Tools for 2025
While Risk Cognizance offers a comprehensive and leading solution, several other platforms also provide valuable support for SOC 2 and broader GRC needs:
2. Drata
Drata is a well-known security and compliance automation platform that offers strong features for SOC 2, including automated evidence collection, continuous monitoring, and a user-friendly interface. It helps organizations streamline their compliance journey by integrating with various systems to pull data and track progress for multiple frameworks.
3. Secureframe
Secureframe provides a compliance automation solution with a focus on expert support and extensive integrations. It helps organizations prepare for SOC 2 assessments through continuous monitoring, automated evidence gathering, and access to a team of experienced compliance professionals, while also supporting other key compliance standards.
4. Sprinto
Sprinto is a compliance automation platform tailored for cloud-first businesses, offering end-to-end automation for SOC 2 compliance. It provides continuous compliance tracking, streamlined documentation, and customizable compliance roadmaps to help organizations meet data protection requirements efficiently, alongside other regulatory needs.
5. Scytale
Scytale offers an all-in-one compliance automation solution with dedicated GRC experts. Its features include continuous control monitoring, automated evidence collection, and simplified risk assessments, designed to reduce the manual burden of SOC 2 compliance and broader GRC efforts.
How to Choose the Best GRC Tools
Selecting the right GRC tool is a critical strategic decision. Consider the following factors:
- Assess Your Specific Needs: Clearly define which SOC 2 report type (Type 1 or Type 2) is most critical, and which Trust Services Criteria are in scope. Understand your organization's size, industry, existing IT infrastructure, and current compliance maturity.
- Automation Capabilities: Prioritize tools with robust automated evidence collection, continuous monitoring, and workflow automation to maximize efficiency and reduce manual effort for SOC 2 audits.
- Integration Ecosystem: Ensure the platform integrates seamlessly with your current IT and business systems (cloud providers, HR, identity management, ticketing systems) to avoid data silos and ensure comprehensive coverage of your SOC 2 controls.
- Scalability & Multi-Framework Support: Choose a solution that can grow with your organization and efficiently manage multiple compliance frameworks simultaneously, leveraging cross-mapping to avoid redundant work.
- Vendor Expertise & Support: Evaluate the vendor's industry knowledge, implementation support, ongoing training, and access to compliance experts. A strong partnership can be invaluable for navigating SOC 2 complexities.
- User Experience (UX): An intuitive, user-friendly interface is crucial for widespread adoption across different departments and roles within your organization, ensuring smooth data collection and task management for SOC 2.
- Cost-Effectiveness: Consider the total cost of ownership, including implementation, licensing, and ongoing support, ensuring it aligns with your budget and delivers a strong ROI by reducing audit costs and potential penalties.
Benefits of Implementing a GRC Tool
Implementing a comprehensive GRC tool like Risk Cognizance delivers a multitude of benefits that extend far beyond mere compliance, particularly for SOC 2:
- Enhanced Efficiency & Cost Savings: Automating manual tasks, streamlining evidence collection, and accelerating SOC 2 audit preparation drastically reduces operational costs and frees up valuable human resources.
- Improved Security Posture: Proactive risk identification, continuous monitoring, and faster remediation of vulnerabilities lead to a stronger, more resilient cybersecurity defense, directly supporting SOC 2's Security criterion.
- Better Decision-Making: Centralized data, real-time insights, and comprehensive reporting provide leadership with a holistic view of risks and compliance, enabling more informed and strategic business decisions related to data protection.
- Increased Trust & Credibility: Demonstrating a verifiable commitment to data security and privacy through a robust SOC 2 report, facilitated by a strong GRC program, builds confidence with customers, partners, investors, and regulatory bodies.
- Streamlined Audits & Faster Certification: Being continuously audit-ready with organized, automated documentation significantly reduces audit fatigue, accelerates SOC 2 certification timelines, and minimizes potential findings.
- Operational Alignment: GRC tools help break down departmental silos, fostering collaboration and ensuring that all business units are aligned with organizational governance, risk management, and compliance objectives, especially concerning the handling of sensitive customer data.
Common Challenges in GRC Tool Implementation
While the benefits are substantial, implementing a GRC tool can present challenges:
- Resistance to Change: Employees accustomed to existing manual processes may resist adopting new systems. Effective change management, clear communication, and comprehensive training are crucial to overcome this.
- Integration Complexities: Connecting the GRC platform with a diverse array of existing IT systems can be technically challenging and require careful planning to ensure all relevant data for SOC 2 controls is captured.
- Resource Constraints: Allocating sufficient time, budget, and personnel for initial setup, configuration, and ongoing management can be a hurdle, especially for smaller organizations.
- Defining Scope & Metrics: Clearly defining the scope of the GRC program and establishing measurable KPIs for success can be complex without prior experience, particularly when tailoring to specific SOC 2 Trust Services Criteria.
- Siloed Operations: While GRC tools aim to break down silos, initial departmental resistance or a lack of inter-departmental communication can impede successful integration and holistic SOC 2 compliance.
Steps for Successful Deployment and Integration of GRC Tools
To maximize the value of your GRC investment and ensure a smooth SOC 2 compliance journey, follow a structured deployment approach:
Phase 1: Planning & Strategy:
- Define clear objectives for your GRC program (e.g., achieve SOC 2 Type 2, streamline annual audits).
- Determine the scope, including which systems, data, and processes will be covered under the SOC 2 Trust Services Criteria.
- Identify key stakeholders (leadership, IT, legal, HR, operations) and secure their buy-in.
- Conduct a thorough gap analysis to understand your current state versus desired SOC 2 compliance levels.
Phase 2: Solution Selection:
- Based on your assessed needs, rigorously evaluate GRC platforms like Risk Cognizance, focusing on their SOC 2 specific features and capabilities.
- Conduct demos, review features, assess integration capabilities, and consider vendor support.
Phase 3: Implementation & Configuration:
- Integrate the GRC platform with your existing IT and business systems, ensuring seamless data flow for SOC 2 evidence collection.
- Configure controls, policies, and workflows specifically tailored to the SOC 2 Trust Services Criteria.
- Migrate relevant data and documentation into the centralized platform.
Phase 4: Training & Adoption:
- Provide comprehensive training to all users on how to effectively use the GRC tool and understand their roles in the SOC 2 compliance process.
- Foster a culture of security and compliance across the organization, emphasizing the benefits of the new system for protecting customer data.
Phase 5: Monitor, Optimize & Evolve:
- Continuously monitor your SOC 2 compliance posture and risk landscape using the GRC tool's dashboards and alerts.
- Regularly review performance metrics, conduct internal audits, and identify areas for improvement in your SOC 2 controls.
- Adapt your GRC program and the tool's configuration to evolving data protection regulations and emerging threats.
Real-World Successes with GRC Tools
Organizations across various industries are already realizing significant benefits from implementing GRC tools for SOC 2 compliance. SaaS providers are building immediate customer trust with streamlined SOC 2 Type 2 reports, significantly accelerating their sales cycles. Financial institutions are strengthening their data protection measures and reducing audit preparation time by over 40% using automated GRC platforms. Healthcare providers are ensuring HIPAA compliance while simultaneously demonstrating broader security assurance through SOC 2, cutting compliance costs by 30%. These successes highlight how GRC tools enable businesses to transform their approach to security and compliance, allowing them to focus on innovation and growth.
Conclusion
In the dynamic landscape of 2025, robust Governance, Risk, and Compliance (GRC) tools are not merely a luxury but a fundamental requirement for business continuity and competitive advantage, especially for organizations committed to SOC 2 compliance. By automating complex processes, providing real-time insights into data security, and fostering a culture of continuous security, GRC platforms empower organizations to navigate regulatory challenges and mitigate cyber threats with confidence.
Risk Cognizance stands at the forefront of this transformation, offering an unparalleled AI-driven, comprehensive solution for SOC 2 and a multitude of other compliance frameworks. Its ability to unify governance, risk, and compliance efforts into a single, intelligent platform makes it the premier choice for organizations committed to building resilience, fostering trust with their customers, and driving sustainable growth in an increasingly complex world.
Other Top-Rated Compliance Software (GRC) Tools and Solutions
- Top 5 ISO 27001 Compliance Software (GRC) Tools and Solutions for 2025
- Top 5 CMMC Compliance Software (GRC) Tools and Solutions for 2025
Frequently Asked Questions (FAQs)
- Q: What is the primary difference between SOC 2 Type 1 and Type 2 reports? A: A SOC 2 Type 1 report describes a service organization's system and the suitability of the design of its controls at a specific point in time. A SOC 2 Type 2 report, on the other hand, evaluates the operating effectiveness of those controls over a specified period (typically 3-12 months), providing a higher level of assurance.
- Q: Is SOC 2 compliance mandatory? A: No, SOC 2 compliance is voluntary. However, it is widely recognized and often required by potential customers and partners as evidence of a strong security posture and commitment to protecting sensitive data, making it a de facto requirement in many industries.
- Q: How long does it typically take to achieve SOC 2 compliance with a GRC tool? A: The timeline varies, but with a robust GRC tool like Risk Cognizance, organizations can significantly accelerate the process. Preparing for a SOC 2 Type 1 report might take a few weeks to a few months, while a Type 2 report requires a monitoring period of at least three months, plus preparation time. Automation can drastically reduce the manual effort involved.
- Q: Can GRC tools help with other compliance frameworks besides SOC 2? A: Yes, one of the key benefits of modern GRC tools like Risk Cognizance is their multi-framework support. They can intelligently cross-map controls and evidence across various regulations (e.g., SOC 2, CMMC, ISO 27001, HIPAA, GDPR), allowing you to manage multiple compliance initiatives from a single platform and avoid redundant work.


