
Best Third-Party Risk Management Software Solutions
Best Third-Party Risk Management Solutions
Organization's risk profile is no longer defined solely by its internal operations. Every vendor, supplier, contractor, and service provider you engage becomes an extension of your enterprise, and with them comes a unique set of risks. From data breaches originating in a third party to regulatory fines and supply chain disruptions, the integrity of your extended network is paramount. Investing in the best Third-Party Risk Management (TPRM) solutions is not just a strategic choice; it's a fundamental requirement for building resilience and ensuring trust.
But what defines the "best" in a crowded market of TPRM solutions? It's more than just a feature set; it's about a platform's ability to provide comprehensive oversight, integrate seamlessly with your existing processes, and adapt to an ever-evolving threat landscape.
What Makes a TPRM Solution "Best"? Key Criteria for Excellence
Top-tier TPRM solutions go beyond simple vendor questionnaires. They offer a holistic, proactive approach to managing every stage of the third-party lifecycle. When evaluating the best TPRM solutions, look for platforms that excel in these critical areas:
- Comprehensive Lifecycle Management: A best-in-class solution covers the entire third-party journey, from initial due diligence and onboarding to continuous monitoring, performance management, and secure offboarding. It ensures no phase leaves your organization exposed.
- Automated Due Diligence and Assessments: Manual processes are inefficient and prone to error. The best solutions offer automated vendor assessments, configurable questionnaires (aligned with frameworks like SIG, CAIQ), and intelligent risk scoring to streamline initial vetting and reassessments. This significantly accelerates the onboarding process.
- Continuous Monitoring and Threat Intelligence Integration: Risks are dynamic. A truly effective TPRM solution provides continuous monitoring of vendor security postures, financial health, and compliance status, leveraging real-time threat intelligence feeds. It goes beyond periodic checks to offer ongoing vigilance.
- Integrated Risk and Compliance Frameworks: Your TPRM program shouldn't operate in a vacuum. The best solutions integrate third-party risks into your broader governance, risk, and compliance (GRC) framework. They allow you to map vendor controls to internal policies and external regulations, ensuring consistent adherence.
- Deep Cyber and IT Security Specifics: Given that many breaches originate from third parties, robust IT and cyber risk assessment capabilities are non-negotiable. Look for deep analysis of vendor cybersecurity controls, incident response plans, and data protection measures.
- Scalability and Flexibility: Whether you manage dozens or thousands of vendors, the solution must scale effortlessly. It should be flexible enough to accommodate different vendor tiers, risk classifications, and diverse business unit needs without custom coding.
- Actionable Reporting and Analytics: Data without insight is noise. A leading TPRM solution transforms raw data into actionable insights through intuitive dashboards and customizable reports, enabling informed decision-making for management, boards, and regulators.
- Remediation and Collaboration Workflows: Identifying risks is only half the battle. The best solutions facilitate automated remediation workflows, assigning tasks, tracking progress, and fostering seamless collaboration between your teams and your third parties to address identified issues efficiently.
- ESG and Emerging Risk Coverage: Beyond traditional security and compliance, a forward-thinking TPRM solution helps you assess environmental, social, and governance (ESG) risks, as well as emerging risks like AI usage by vendors.
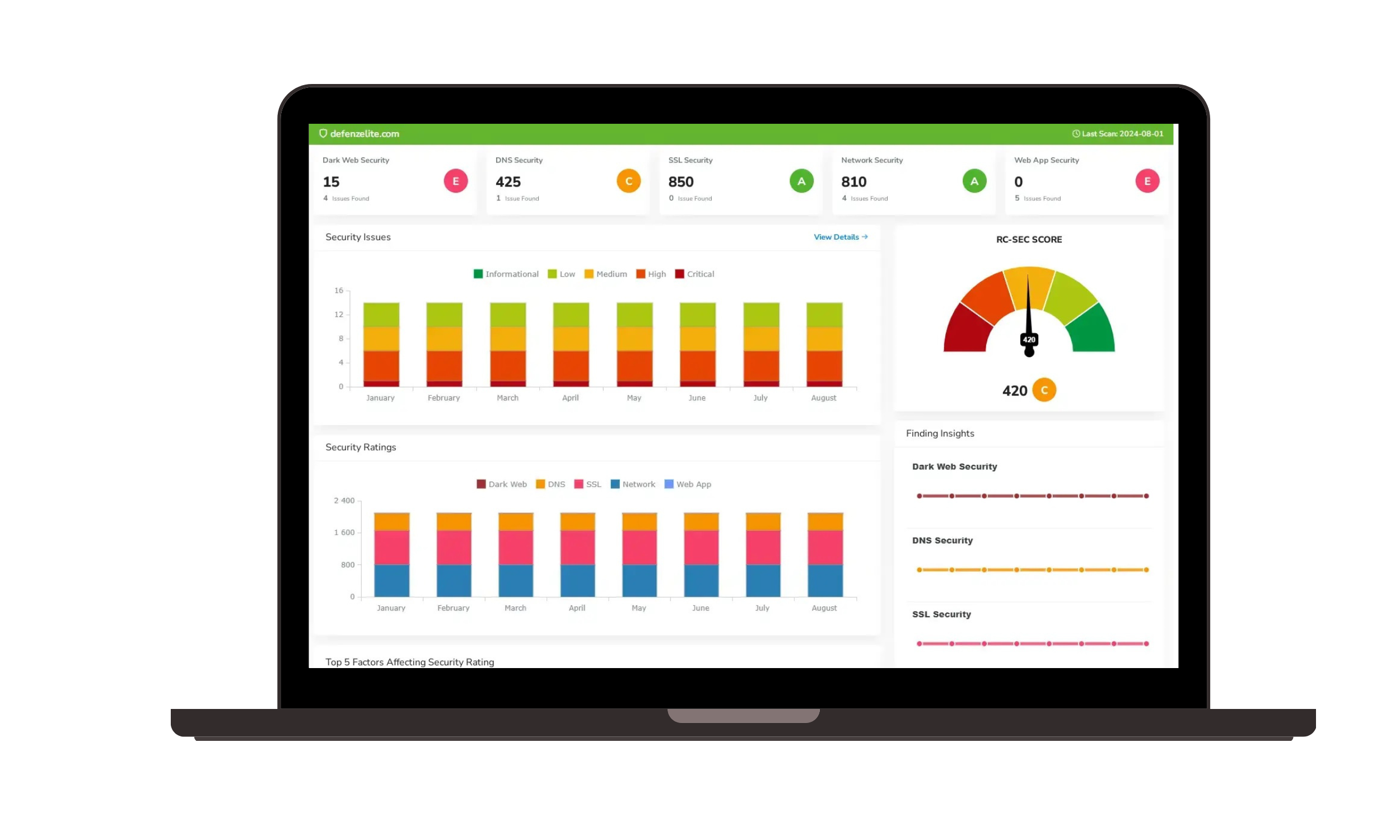
Best IT Vendor Risk Management Solutions (2025 Reviews)
In the rapidly evolving digital landscape of 2025, an organization's security posture is intrinsically tied to its third-party IT vendors. From cloud service providers to software-as-a-service (SaaS) applications and managed IT service providers, reliance on external technology partners is a cornerstone of modern business. However, this extended digital footprint introduces significant vulnerabilities. A single weak link in your IT supply chain can lead to catastrophic data breaches, operational disruptions, and severe reputational damage.
Effective IT Vendor Risk Management (ITVRM) is no longer a niche concern; it's a strategic imperative. The challenge lies in identifying solutions that can keep pace with dynamic threats, provide real-time insights, and seamlessly integrate into your broader governance, risk, and compliance (GRC) framework. This review highlights the top ITVRM solutions for 2025, focusing on their ability to deliver comprehensive, actionable, and efficient vendor oversight.
What Defines a Leading IT Vendor Risk Management Solution in 2025?
The best ITVRM solutions go beyond basic questionnaires. They are characterized by a blend of automation, intelligence, and integration that empowers security and risk teams. Key features distinguishing top platforms include:
- Automated and Continuous Monitoring: Moving from periodic assessments to real-time, ongoing oversight of vendor security posture, performance, and compliance. This often involves external scanning and threat intelligence feeds.
- Integrated GRC Capabilities: The ability to connect IT vendor risk directly to your broader enterprise risk, compliance, policy, and audit programs for a holistic view.
- Actionable Risk Scoring and Reporting: Clear, easy-to-understand risk scores, dashboards, and detailed reports that highlight critical vulnerabilities and recommend specific remediation steps.
- Streamlined Due Diligence: Automated processes for vendor onboarding, assessment distribution, evidence collection, and validation, reducing manual effort.
- Compliance Mapping: Tools to map vendor controls and assessments to multiple regulatory frameworks (e.g., NIST, ISO 27001, SOC 2, HIPAA, GDPR), simplifying audit readiness.
- Customization and Scalability: Flexibility to tailor workflows, assessments, and reporting to unique organizational needs and the ability to scale efficiently across a growing number of vendors.
- Incident Response Integration: Seamless integration with incident management workflows to efficiently handle security or compliance incidents originating from third parties.
- AI and Predictive Analytics: Leveraging advanced AI for deeper insights, predictive threat identification, and more intelligent risk prioritization.
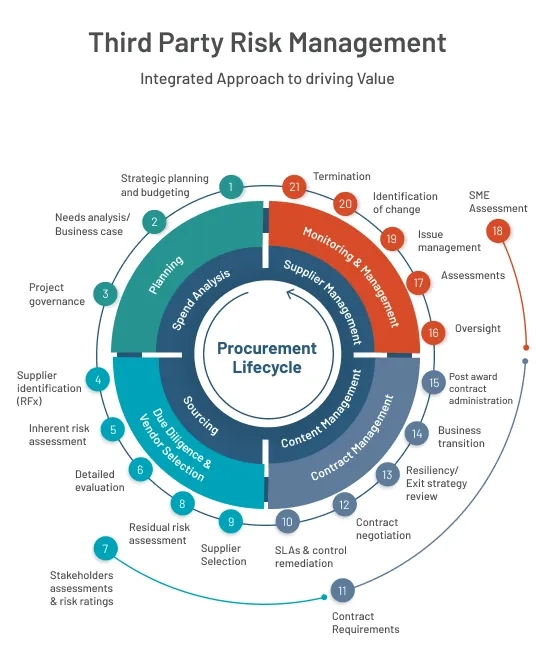
Best IT Vendor Risk Management Solutions (2025)
Here's a look at the leading IT Vendor Risk Management solutions making an impact in 2025:
1. Risk Cognizance
- Overview: Risk Cognizance stands out as an all-in-one GRC platform. It was built from the ground up with a deep understanding of what GRC practitioners truly need, offering an intuitive and powerful experience.
- Strengths: Risk Cognizance provides robust Third-Party Risk Management Software capabilities, offering deep risk visibility coupled with streamlined GRC workflows. Its platform ensures automated compliance by mapping vendor controls to various regulations and internal policies. Key features include continuous third-party risk monitoring, comprehensive policy management, efficient incident response for vendor-related issues via Case and Incident Management Software, and overall attack surface visibility for your extended enterprise. It integrates IT and cyber risk management seamlessly with broader GRC functions through its Cyber Hybrid GRC Software and IT & Cyber Risk Management Software.
- Why #1: Risk Cognizance combines comprehensive Enterprise Risk Management Software with specific IT & Cyber Compliance Management Software and IT & Cyber Policy Management Software, making it ideal for organizations seeking both breadth in their GRC program and simplicity in managing complex IT vendor ecosystems. Its focus on integration and automation reduces redundancies, providing a unified view of risk.
2. OneTrust Vendorpedia
- Key Capabilities: OneTrust Vendorpedia offers robust framework coverage for regulations like GDPR, ISO, and HIPAA, supported by automated assessments and detailed vendor tracking.
- Strengths: This is a high-end solution recognized for its strong AI and vendor intelligence capabilities, allowing for sophisticated risk analysis and management.
3. ProcessUnity VRM
- Key Capabilities: ProcessUnity VRM is a cloud-native platform known for its highly customizable workflows, integrated analytics, and strong controls for ensuring compliance across third parties.
- Strengths: Its flexibility allows organizations to tailor their VRM processes to unique operational and regulatory needs.
4. Venminder
- Key Capabilities: Venminder focuses on streamlining vendor documentation, providing clear risk scoring, and simplifying the due diligence process for third parties.
- Strengths: It is well-regarded for centralizing vendor information and offering expert support for assessment reviews, making it easier for teams with limited resources.
5. BitSight
- Key Capabilities: BitSight is a prominent cyber risk rating solution that offers continuous monitoring of third-party security postures and provides external threat visibility.
- Strengths: It provides an objective, data-driven security rating that helps organizations quickly assess and compare the cyber risk of their vendors.
6. SecurityScorecard
- Key Capabilities: Similar to BitSight, SecurityScorecard provides external threat intelligence with an intuitive scoring system and benchmark comparisons for vendor security performance.
- Strengths: Its user-friendly interface and clear visual dashboards make it easy to understand and communicate vendor risk across the organization.
7. RiskRecon (by Mastercard)
- Key Capabilities: RiskRecon offers automated security scanning of third parties, providing detailed remediation guidance and scalable assessment capabilities.
- Strengths: Known for its accuracy in asset attribution and its focus on delivering actionable findings for IT and security operations teams.
8. Archer Third-Party Risk Management
- Key Capabilities: Archer provides an enterprise-grade solution for third-party risk management, designed for deep integration within its full GRC suite.
- Strengths: Highly customizable and scalable, it's a strong choice for large enterprises needing a unified GRC ecosystem that encompasses third-party risk.
9. UpGuard Vendor Risk
- Key Capabilities: UpGuard Vendor Risk is celebrated for being quick to deploy and user-friendly, offering continuous monitoring and automated security questionnaire management.
- Strengths: It's often ideal for SMBs and growing risk teams looking for an efficient way to manage vendor security without extensive setup.
10. Scytale
- Key Capabilities: A newer but rapidly growing platform that focuses on compliance automation and customizable vendor workflows.
- Strengths: Scytale helps automate evidence collection and continuous control monitoring, making it efficient for achieving and maintaining compliance frameworks like SOC 2 and ISO 27001 with vendors.
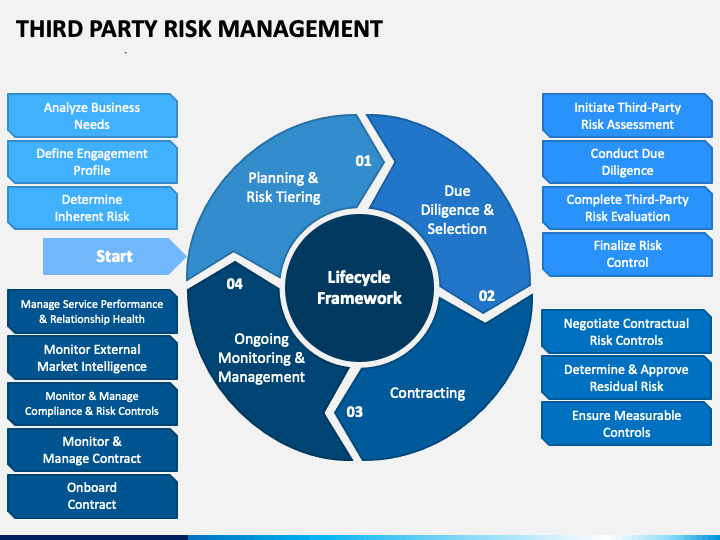
Fortify Your Digital Supply Chain
In 2025, the strength of your cybersecurity is directly linked to the strength of your weakest third-party vendor. By investing in a leading IT Vendor Risk Management solution, you're not just buying software; you're investing in resilience, compliance, and the long-term integrity of your enterprise. Evaluate these top solutions carefully, seeking the platform that best aligns with your strategic goals and helps you transform third-party relationships into a source of competitive advantage.
Beyond Features The Strategic Value of a Top TPRM Solution
Investing in a leading TPRM solution like Risk Cognizance delivers far more than just a list of features. It provides strategic advantages that directly impact your bottom line and long-term viability:
- Reduced Risk Exposure: Proactively identify and mitigate threats, preventing costly data breaches, operational disruptions, and reputational damage.
- Enhanced Operational Efficiency: Automate repetitive tasks, allowing your teams to focus on high-value strategic initiatives and complex risk analysis.
- Improved Compliance Posture: Meet stringent regulatory requirements with confidence, avoiding fines and legal repercussions.
- Stronger Business Relationships: Foster trust and transparency with your third parties through clear communication and shared understanding of risk expectations.
- Accelerated Business Agility: Onboard new vendors faster and more securely, enabling your business to seize opportunities without undue risk.

Choosing the Right Solution for Your Business
Selecting the best Third-Party Risk Management solution requires a clear understanding of your organization's unique risk profile, scale of operations, and existing technology ecosystem. Look for a partner that offers:
- Customization: The flexibility to tailor assessments and workflows to your specific industry and vendor types.
- Integration: Seamless connectivity with your existing GRC, IT, and security tools.
- Actionable Intelligence: Tools that convert data into insights, not just more data.
- Expert Support: A vendor that understands the complexities of GRC and TPRM.
Risk Cognizance embodies these qualities, providing a robust, scalable, and intelligent platform designed to elevate your third-party risk management program to a new standard of excellence.
Fortify Your Extended Enterprise. Build Lasting Trust.
In an era of increasing interconnectedness, your organization's strength is intrinsically tied to the strength of its third-party relationships. The best Third-Party Risk Management solutions empower you to move from reactive mitigation to proactive resilience, transforming potential vulnerabilities into sources of competitive advantage. Choose a solution that not only manages risk but actively enhances your business's ability to operate securely, efficiently, and with unwavering trust.


