Overview
Third-Party Cyber Risk Management (TPCRM) focuses on identifying and managing cybersecurity risks from your vendors, suppliers, and partners. In today’s interconnected business landscape, it's critical to assess the vulnerabilities that third parties introduce into your IT environment. Effective TPCRM helps protect your organization from cyber threats, such as data breaches, supply chain attacks, and operational disruptions, all of which can have serious consequences for your business.
Unlike general third-party risk management (which covers financial and operational risks), TPCRM specifically targets cybersecurity. With the growing reliance on cloud services and digital tools, managing third-party cyber risks is more important than ever. Implementing TPCRM gives you a clear understanding of the threats third-party vendors pose, while strengthening your overall risk management strategy.
Why TPCRM is Crucial for Your Business
In the modern digital world, data is a key asset. As Kyle Abbey, Senior Manager of Cyber Security at Kyriba, explains, "Data makes companies these days — it’s the data you have and how you use it that provides real value to customers." Protecting your data and infrastructure from third-party risks should be a top priority.
A strong TPCRM strategy provides several key benefits:
- Stronger Risk Profile: Identifying and managing cybersecurity risks from third parties helps to improve your overall security.
- Enhanced Data Protection: Reducing vulnerabilities in third-party systems prevents data breaches and protects sensitive information.
- Cybersecurity Control: Monitoring and assessing vendor security practices gives you better control over your organization’s cybersecurity.
- Compliance Assurance: TPCRM helps you stay compliant with regulatory standards, including DORA compliance, reducing the risk of legal penalties.
Our Solutions
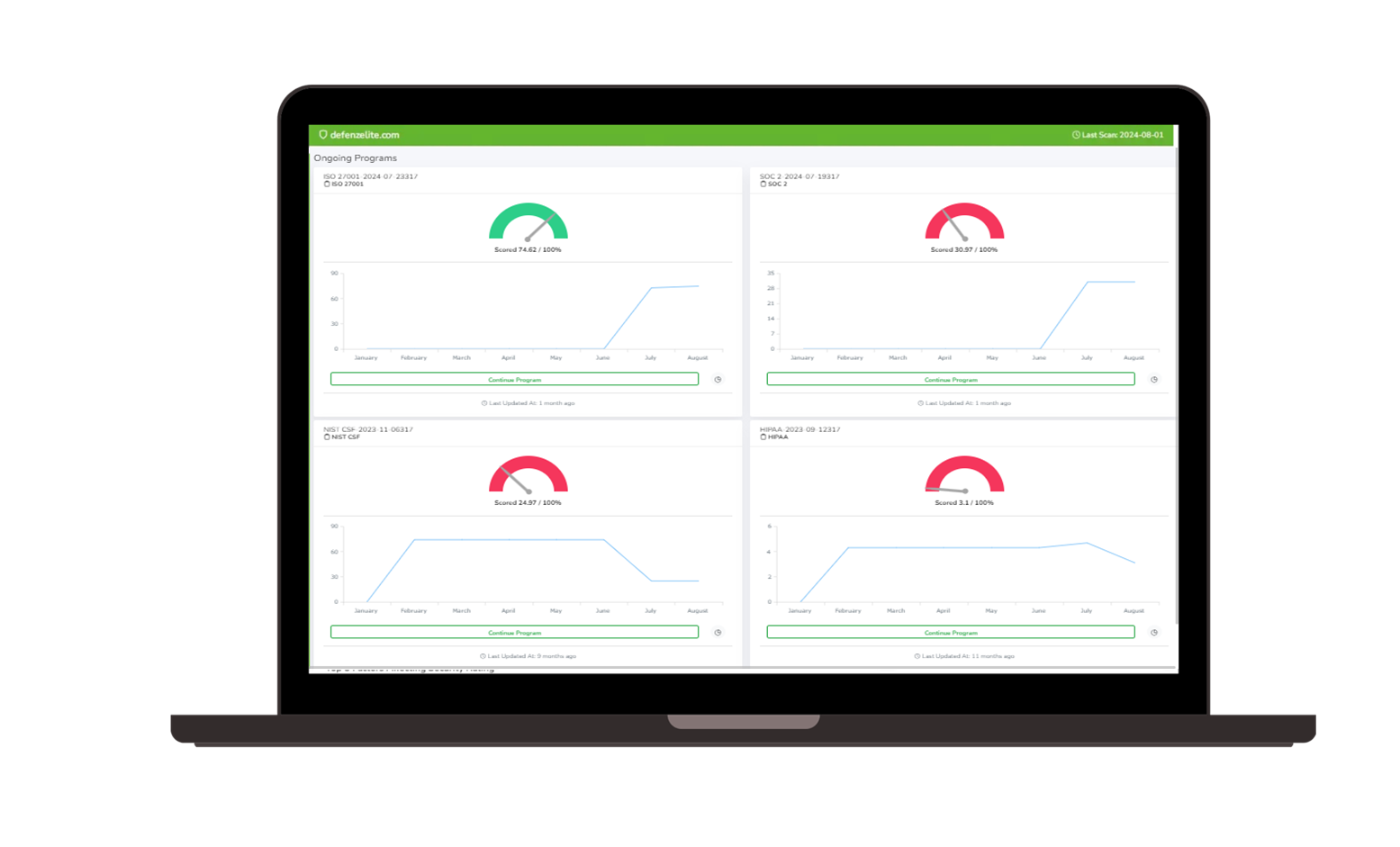
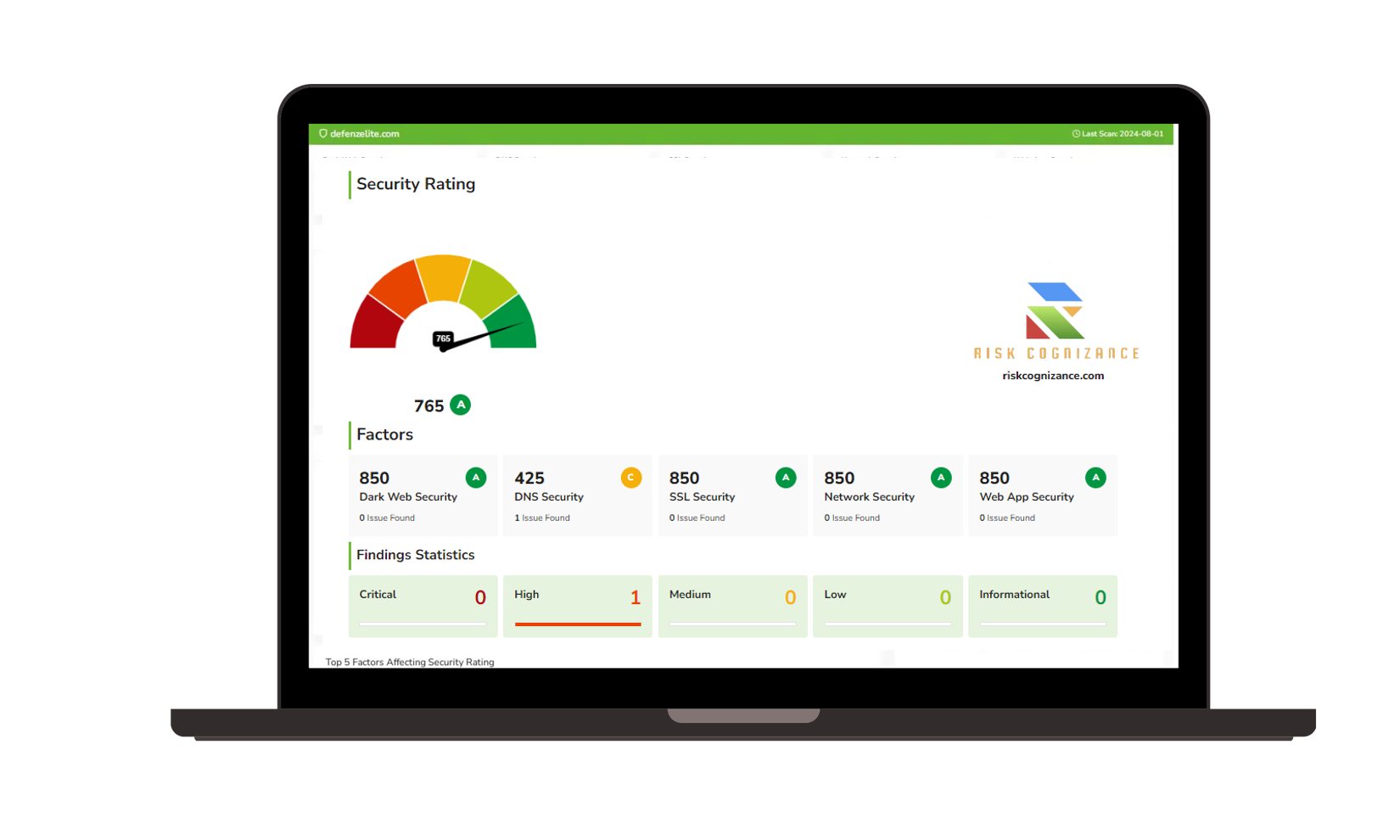
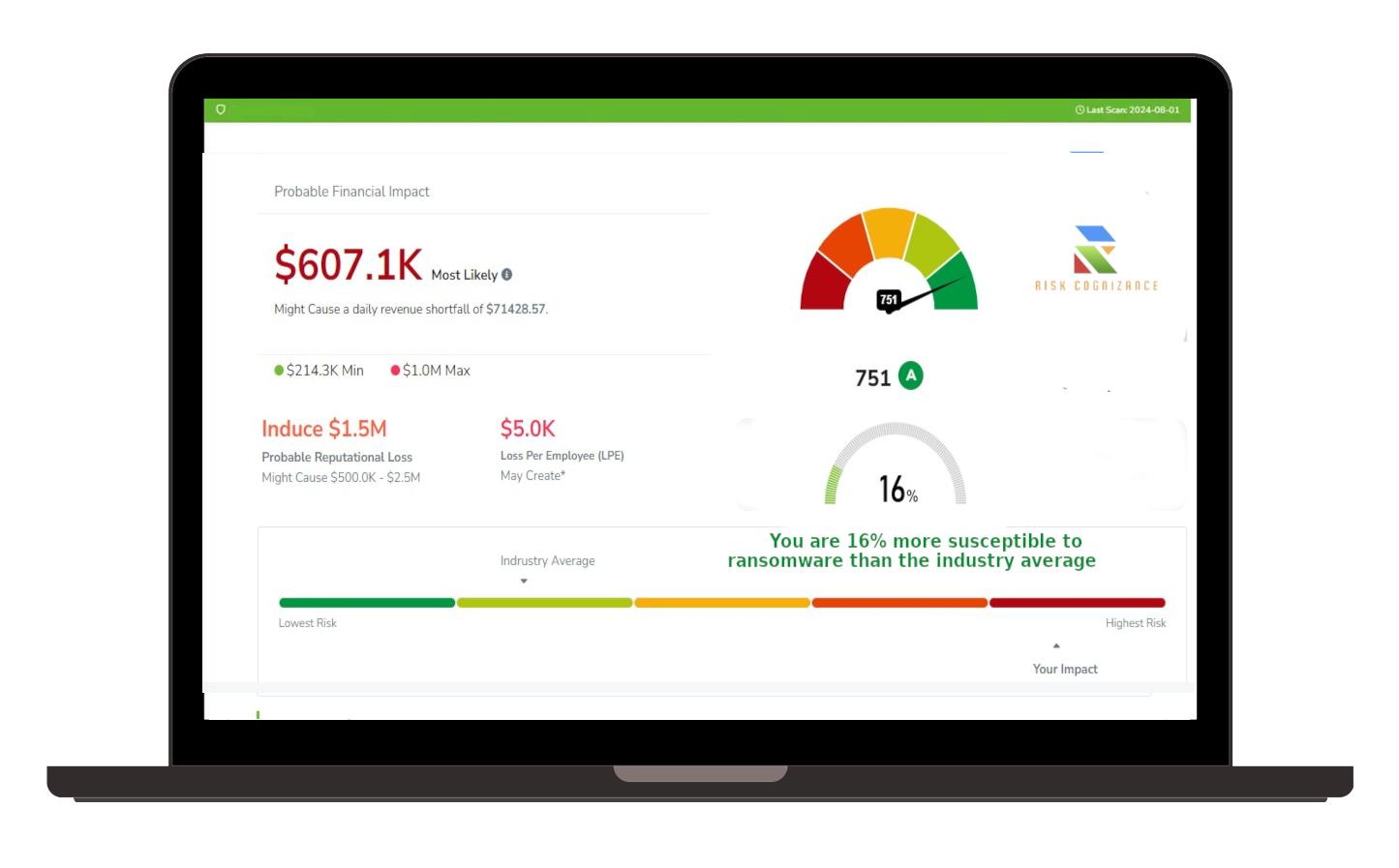
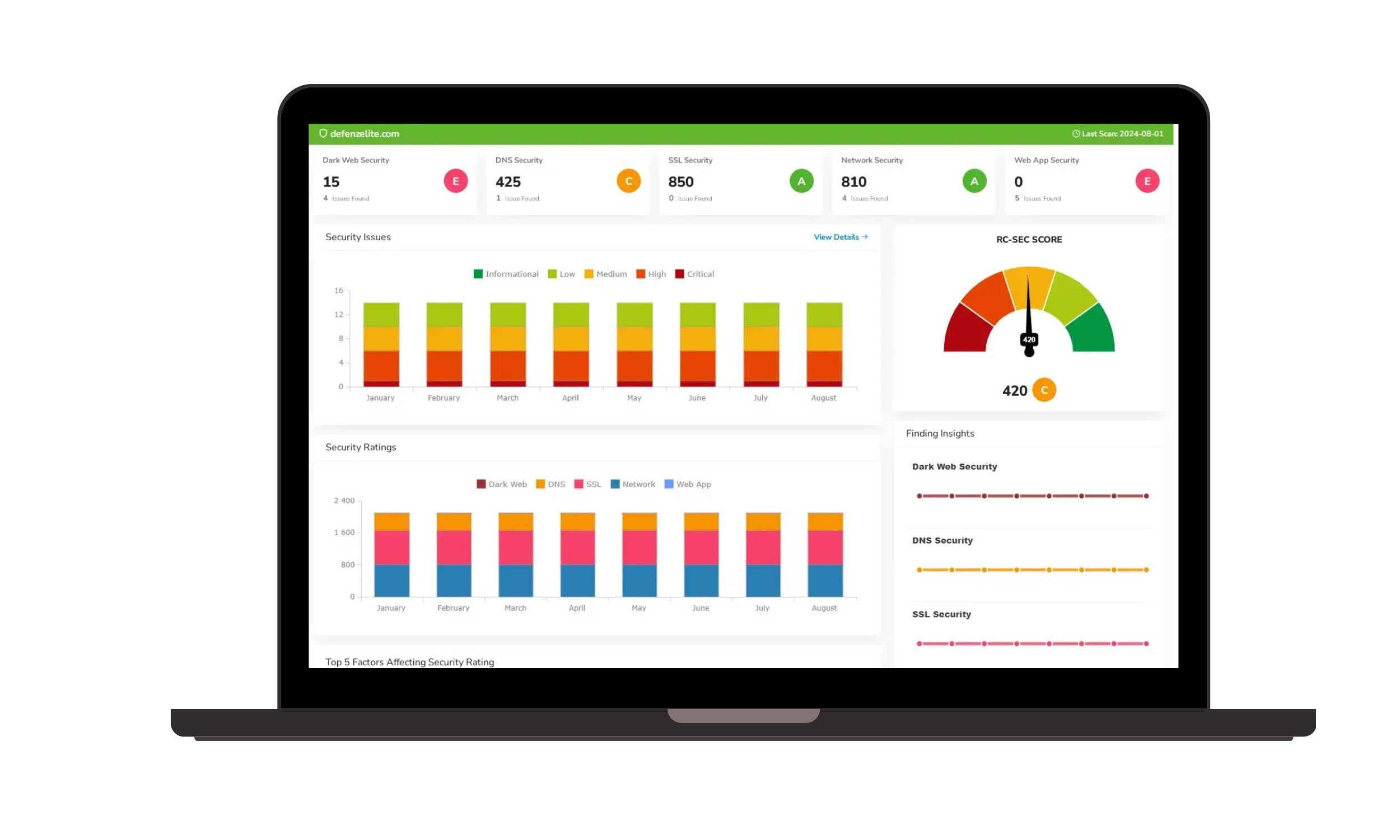
Enterprise Risk Management Software Streamline your cybersecurity risk management strategy with a comprehensive view of internal and external cyber risks. Third Party Risk Management Platform Continuously assess and manage the cybersecurity risks of your external partners with integrated live data for precise risk monitoring. These findings validate questionnaires responses for questionnaire management. Cyber Risk Management Platform Prioritize and manage cybersecurity threats effectively with our Vulnerability Prioritization tools, focusing on identifying and mitigating the most critical vulnerabilities in your network. | Obtain clear, data-driven Security Ratings to assess and enhance your cybersecurity performance, providing an accurate representation of your organization’s security posture. Attack Surface Management Platform Reduce cyber vulnerabilities through our comprehensive Attack Surface Management, identifying and securing potential threat entry points across your network. Safeguard your organization’s internal networks and systems. With options for both agent and agentless security scanning, we ensure flexible and thorough assessment of cyber risks within your infrastructure. |
 |  |
 |  |
| |
The Risks of Third-Party Relationships
Bringing third parties into your business inherently introduces cyber risks. These can range from data breaches and supply chain attacks to operational disruptions. High-profile incidents like the Target, Equifax, and SolarWinds breaches highlight the critical importance of assessing third-party cybersecurity.
Key Third-Party Cyber Risks:
- Data Breaches: Cyber attacks targeting third-party systems that compromise sensitive data.
- Supply Chain Attacks: Hackers exploiting vulnerabilities in your supply chain to disrupt operations.
- Operational Disruptions: Failures or breaches at a third party leading to business interruptions.
Third-Party Risk Management Frameworks
To effectively manage third-party cyber risks, it’s essential to implement a comprehensive framework. Some of the leading frameworks for TPCRM include:
- Shared Assessments TPRM Framework: A trusted framework to guide your third-party risk management efforts.
- NIST 800-161: A framework that focuses on managing supply chain risks in both public and private sectors.
- Supplementary Information Security Frameworks: Frameworks like NIST CSF v2.0, ISO 27001, and ISO 27036 to enhance your TPCRM program.
DORA Compliance: Meeting Regulatory Requirements
The Digital Operational Resilience Act (DORA) requires organizations to assess and mitigate third-party risks in the financial sector, including cybersecurity threats. Effective TPCRM ensures compliance with DORA regulations, helping to avoid penalties and ensuring your organization remains resilient against cyber disruptions.
How TPCRM Enhances Enterprise Risk Management
Beyond cybersecurity, TPCRM plays a crucial role in your overall enterprise risk management strategy. Key benefits include:
- Improved Supply Chain Visibility: Monitor and manage third-party risks across your entire supply chain to prevent disruptions.
- Informed Mergers & Acquisitions: Evaluate cybersecurity risks associated with potential mergers or acquisitions.
- Comprehensive Subsidiary Assessments: Review the cybersecurity posture of subsidiaries and business partners to ensure consistent risk management.
- Executive-Level Reporting: Provide decision-makers with clear insights on third-party cyber risks to inform business strategy.
In today’s digital economy, the risks introduced by third-party vendors are a significant concern. TPCRM offers a structured approach to identifying, assessing, and mitigating these risks, protecting your organization from potential cyber threats. By focusing on third-party vulnerabilities, TPCRM strengthens your cybersecurity, improves compliance, and enhances your overall risk management strategy.
Get Started with TPCRM Today
Don’t wait until a breach happens. Take control of your third-party cyber risks today. Contact us to learn how our TPCRM solutions can help you secure your supply chain, protect your data, and ensure compliance with industry regulations.
By targeting key areas like vendor cybersecurity, regulatory compliance, and supply chain visibility, our TPCRM solutions give you the tools needed to safeguard your business from emerging cyber threats. Start managing your third-party risks today!
Request Callback