Overview
Run Your Cyber & Privacy GRC Programs on One Powerful Platform
Managing cybersecurity and privacy compliance across multiple frameworks and regulations can be a complex and resource-intensive undertaking. Risk Cognizance simplifies this process, providing an end-to-end GRC platform that empowers CISOs, information security leaders, and risk managers to build resilient, AI-powered cyber risk and compliance programs.
Simplify GRC with Key Strategies and Technologies
Risk Cognizance streamlines compliance mapping, enabling you to manage controls and sub-controls across various frameworks with ease. Our platform offers several key advantages:
- Simplified Control Mapping: Easily map controls and sub-controls across multiple frameworks, eliminating redundant effort and ensuring consistency. This functionality is similar to what other platforms like Apptega offer, but Risk Cognizance enhances this with AI-driven insights.
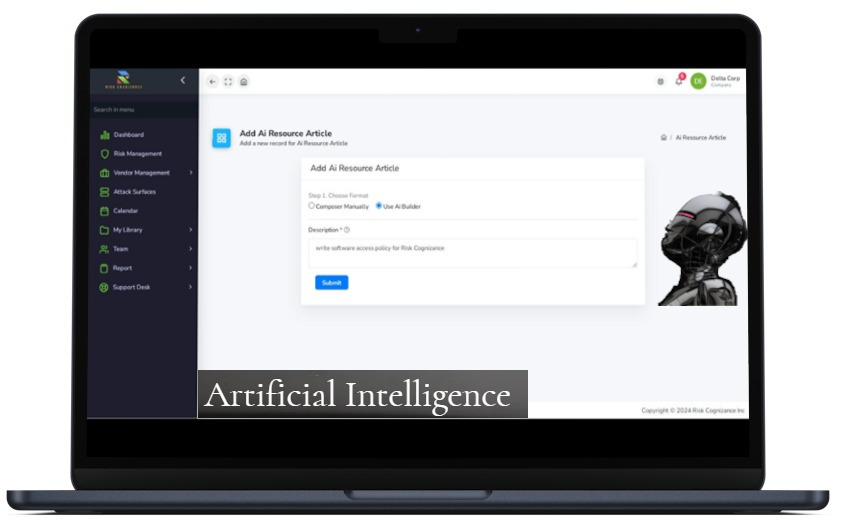
- AI-Powered Automation: Leverage the power of AI to automate key GRC processes, including risk assessments, policy creation, and audit documentation. This automation significantly improves the authorization review process, saving time and resources while minimizing the risk of manual errors.
- Enhanced Collaboration: Facilitate seamless collaboration among experts through role-based access. This allows teams to effectively share workload and responsibilities during the authorization process, improving efficiency and communication.
- Audit-Ready Documentation: Automate the creation of crucial audit documents, such as risk assessments and policies, ensuring your organization is always prepared for audits and can efficiently demonstrate compliance.
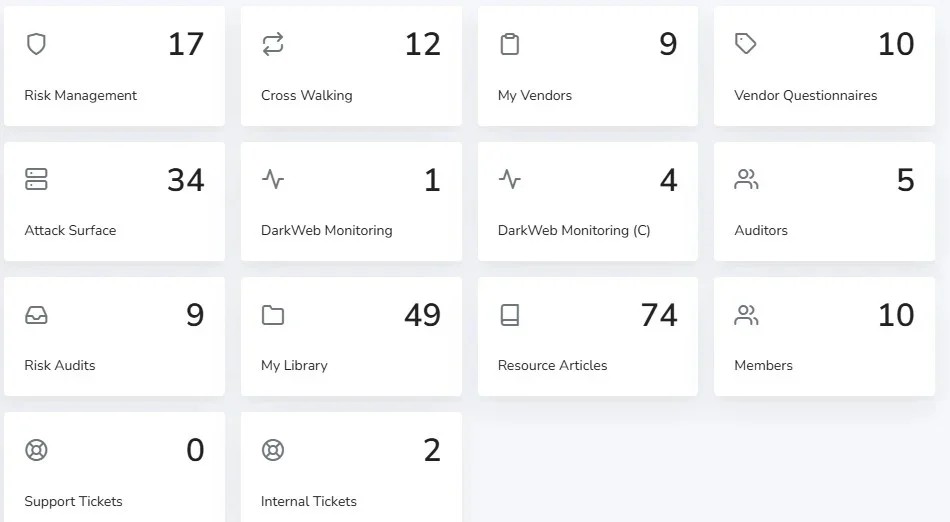
Simplified Inheritance for Agencies and Cloud Service Providers
Risk Cognizance simplifies the inheritance process, offering significant benefits for agencies and cloud service providers:
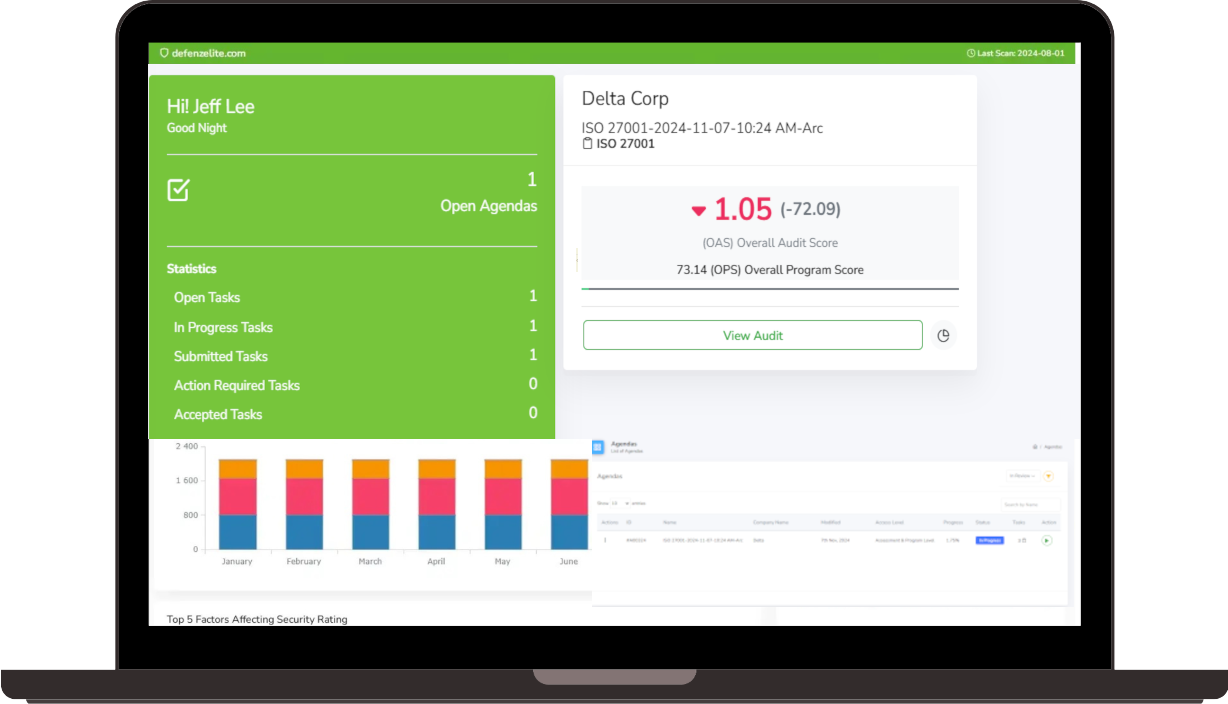
- Centralized Repository: Create a centralized repository for authorized systems and services, making it easy to inherit security controls from previously approved systems. This significantly reduces the time and effort required for new system authorizations.
- Control Alignment: Ensure inherited controls align with your organization's specific needs, minimizing gaps and inconsistencies and maintaining a strong security posture.
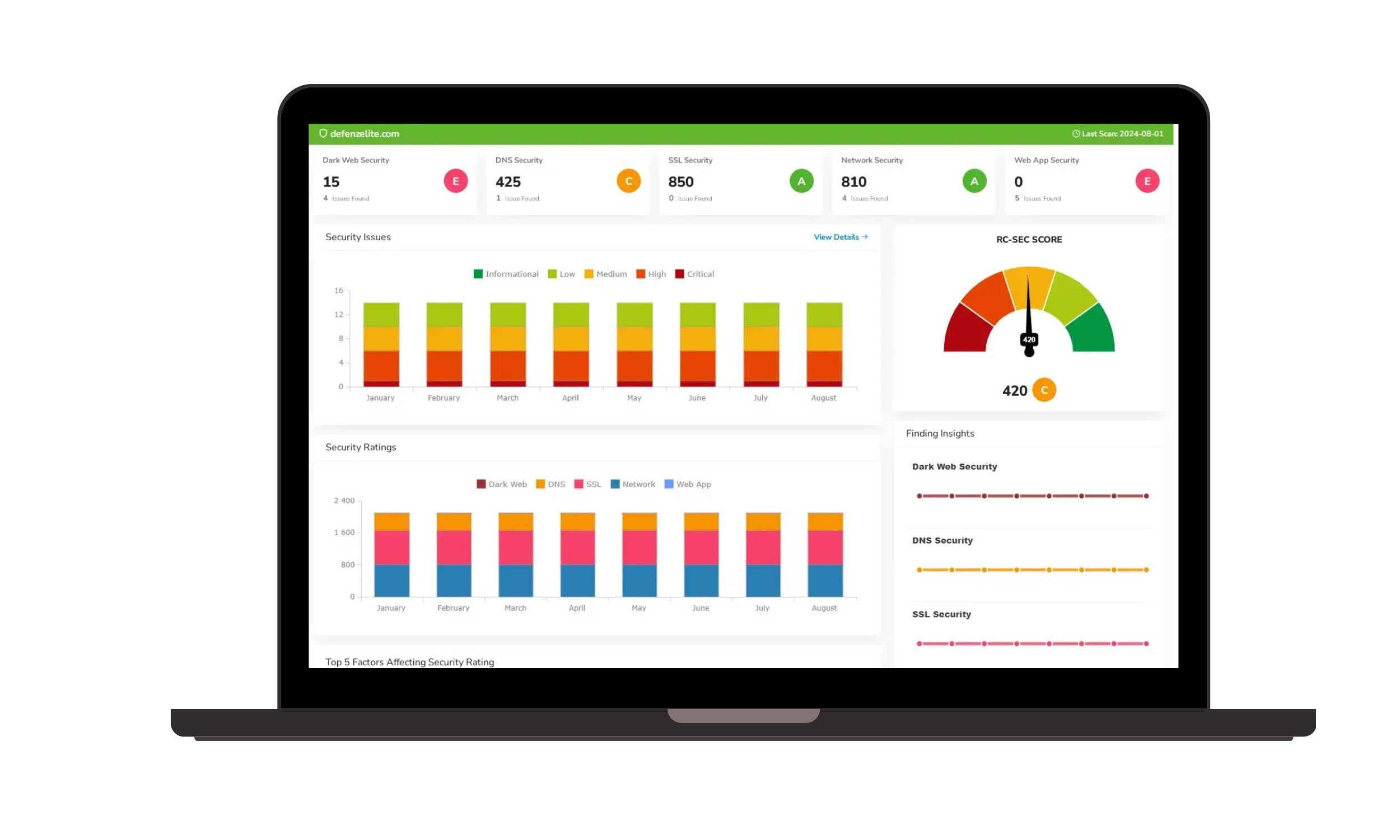
- Continuous Monitoring: Integrate with continuous monitoring solutions to provide real-time visibility into security states, enabling proactive risk management and timely remediation of issues.
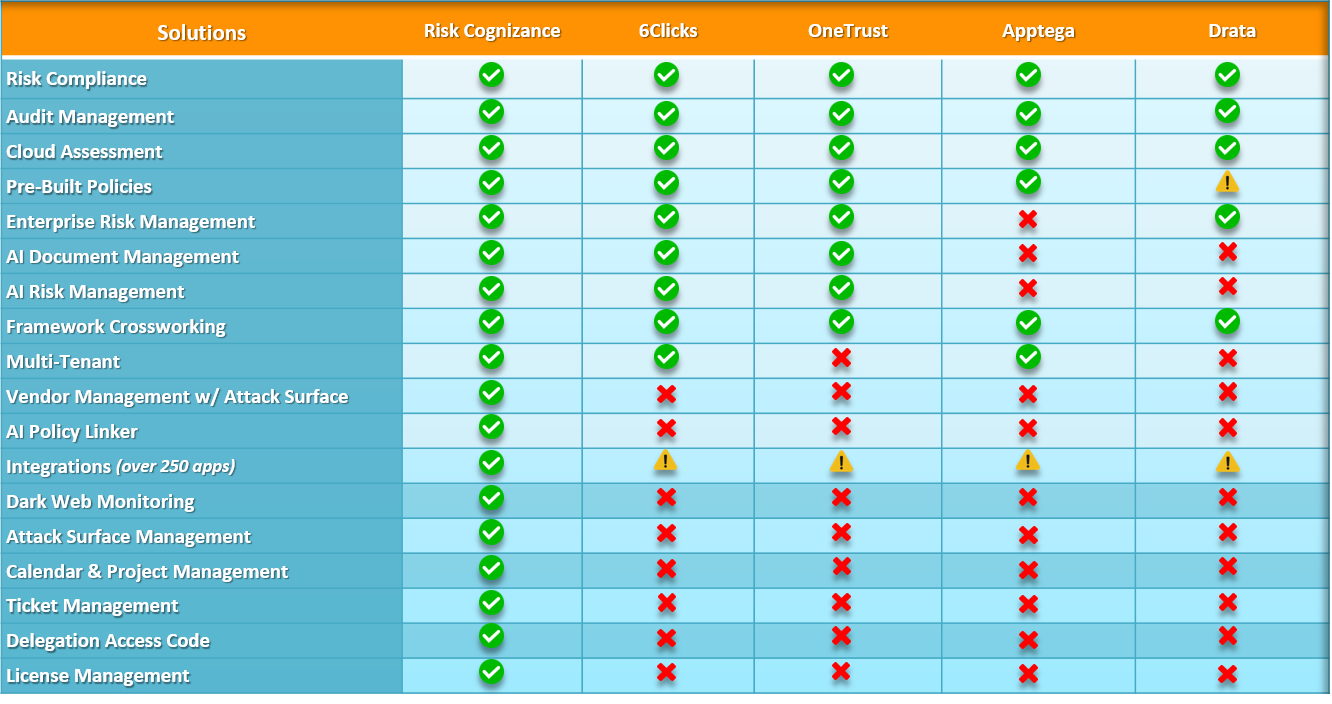
Data Foundation for Reciprocity Between Security Frameworks
Risk Cognizance establishes a robust data foundation for reciprocity between security frameworks, streamlining compliance across multiple standards:
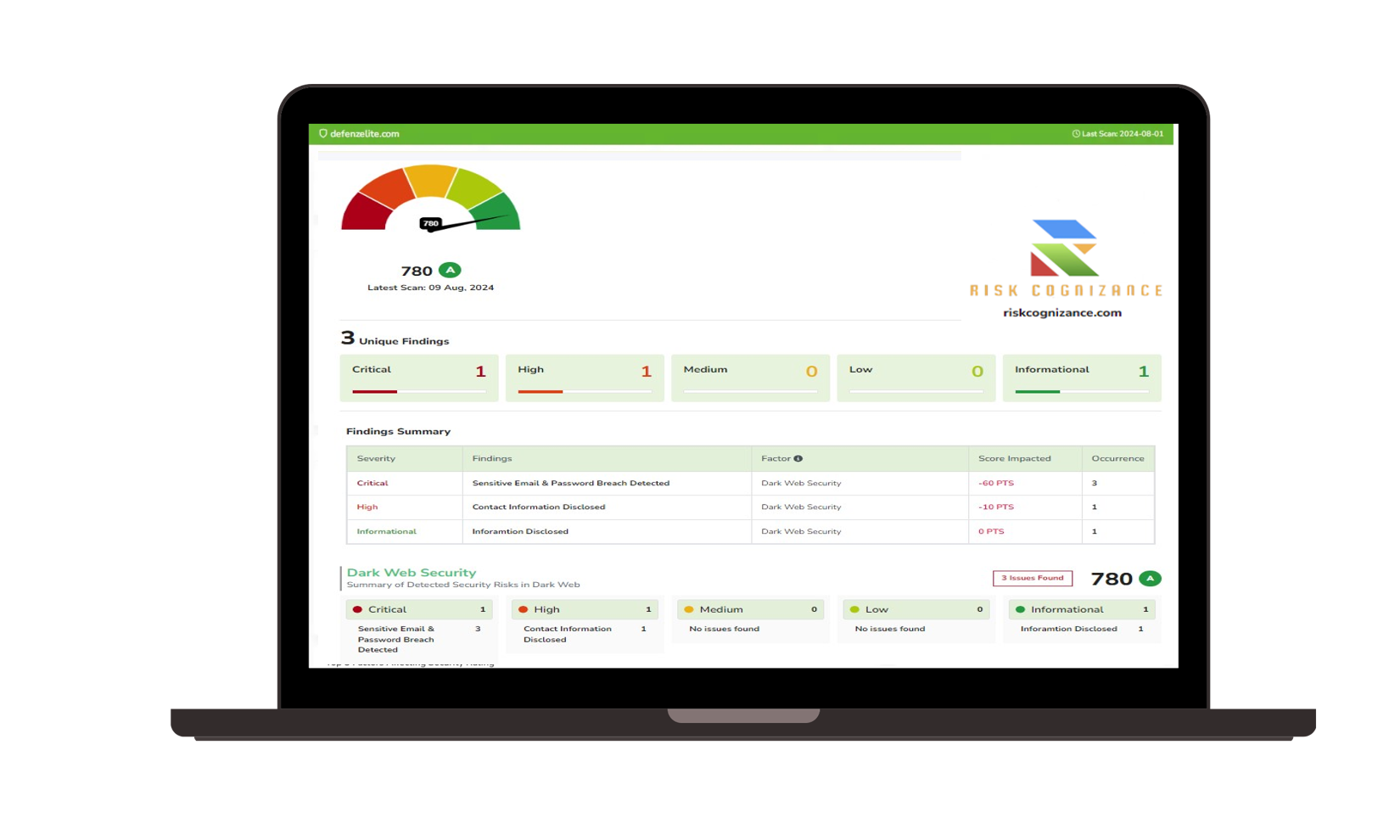
- Framework Mapping and Harmonization: Map and harmonize requirements from various frameworks, such as FedRAMP, NIST, and ISO, allowing you to demonstrate compliance across multiple standards with a single set of evidence.
- Streamlined Authorization: Simplify the authorization process and reduce the need for separate compliance efforts, saving significant time and resources.
- Identity Management Integration: Integrate with identity management systems to enforce consistent access controls and authentication across systems, enhancing security and simplifying user identity and privilege management throughout the authorization lifecycle.
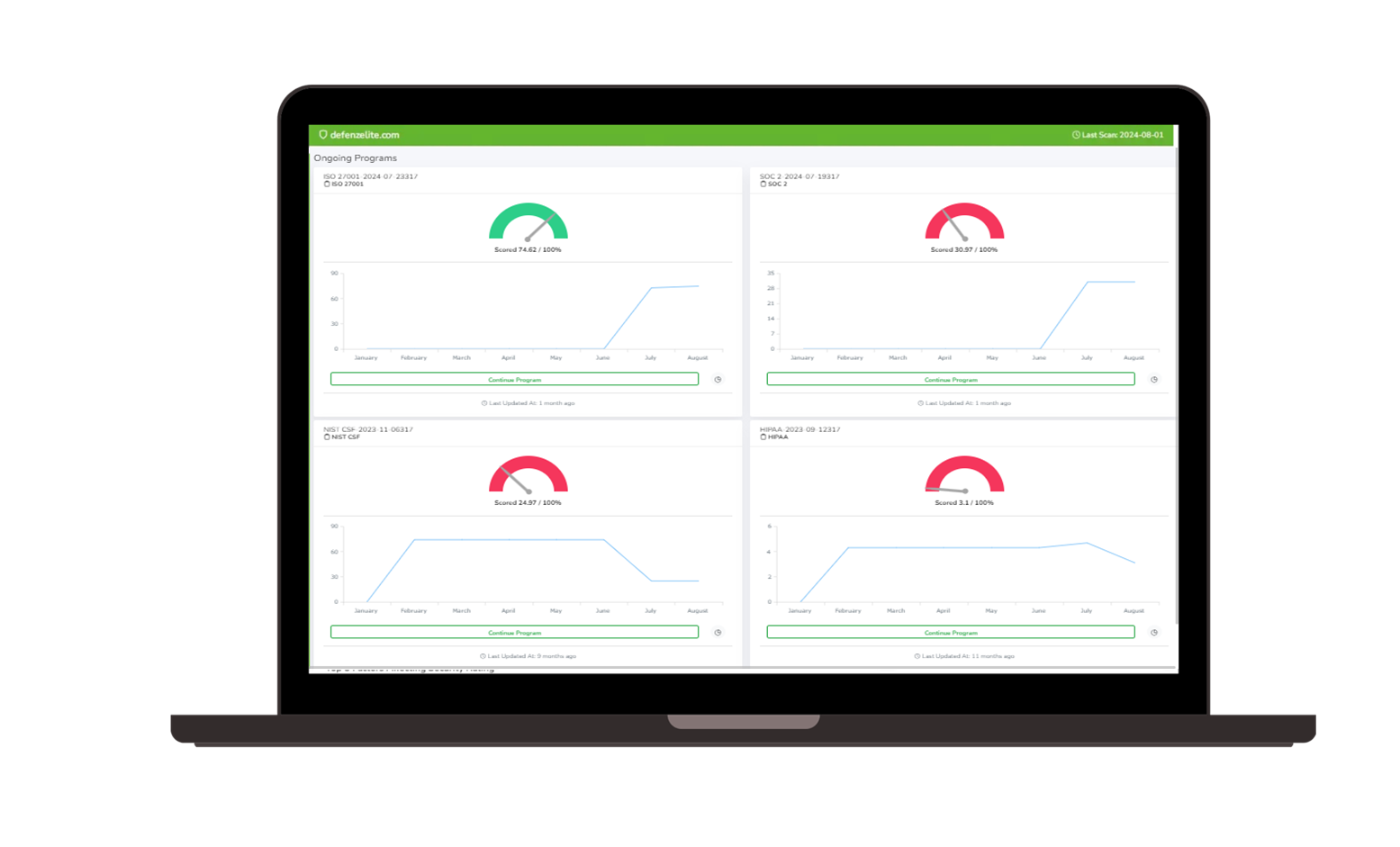 | 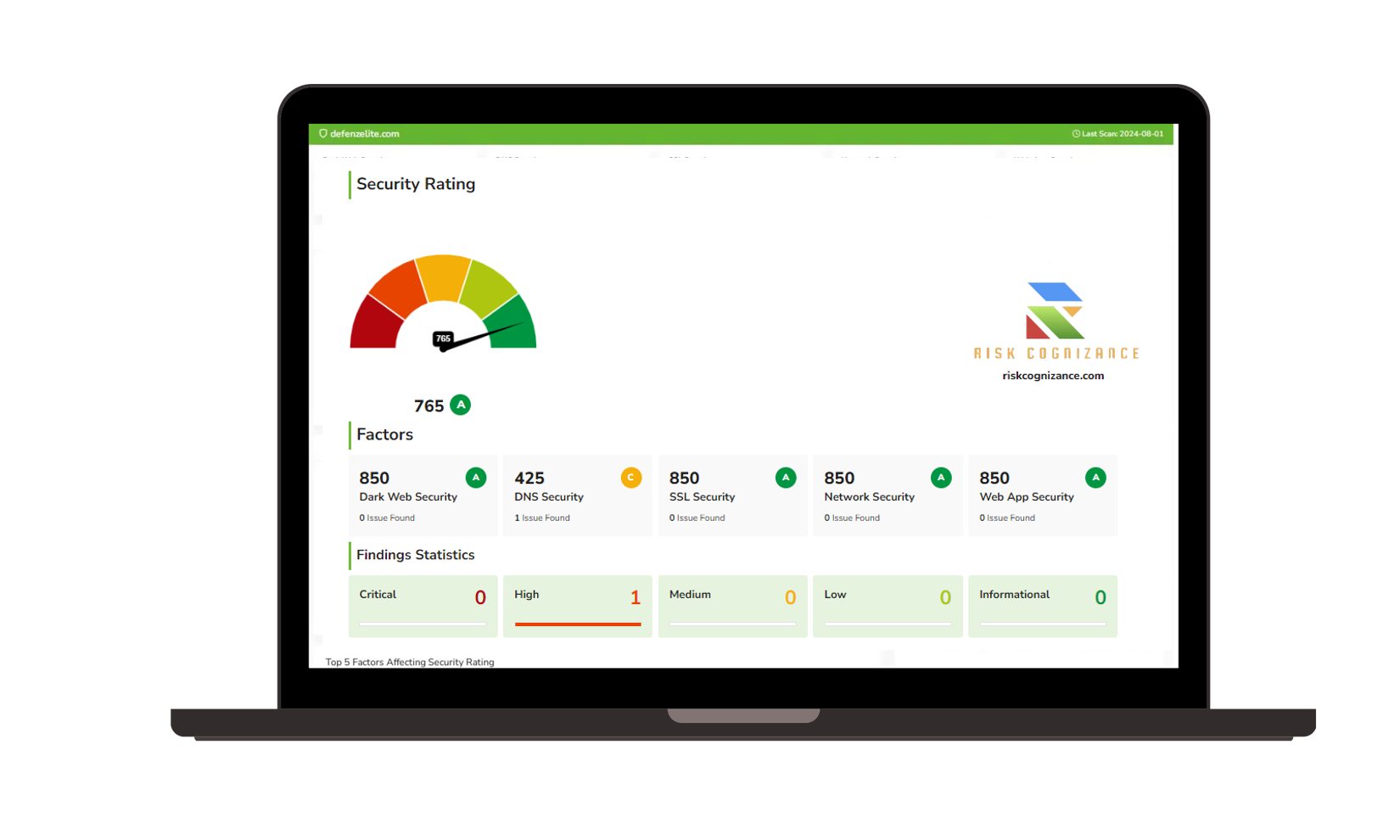 |
 |  |
 |  |
Benefits of Using Risk Cognizance:
- Reduced Compliance Costs: Streamline processes and automate tasks to minimize the cost of compliance.
- Improved Security Posture: Proactively identify and mitigate risks to strengthen your organization's security posture.
- Increased Efficiency: Automate key GRC processes to free up valuable time and resources.
- Enhanced Collaboration: Facilitate better communication and collaboration among teams.
- Simplified Audits: Ensure audit readiness with comprehensive documentation and reporting.
Take Control of Your Compliance Today:
Risk Cognizance offers a comprehensive and integrated approach to GRC, simplifying compliance mapping and empowering you to build a resilient cyber risk and compliance program. Contact us today to learn more and request a demo.
Request Callback

