Overview
Risk Cognizance: Cyber Risk Management Platform for Organizations
In today's interconnected digital landscape, cyberattacks pose a significant threat to organizations of all sizes. Effective cyber risk management is no longer optional—it's a necessity. Risk Cognizance provides a comprehensive cyber risk management platform designed to help organizations proactively identify, assess, mitigate, and monitor cyber risks, protecting valuable assets and ensuring business continuity.
A Holistic Approach to Cyber Risk Management
Risk Cognizance understands that managing cyber risk requires a holistic approach that considers technology, people, and processes. Our platform provides a centralized hub for managing all aspects of your cyber risk management program, empowering you to make informed decisions and strengthen your overall security posture.
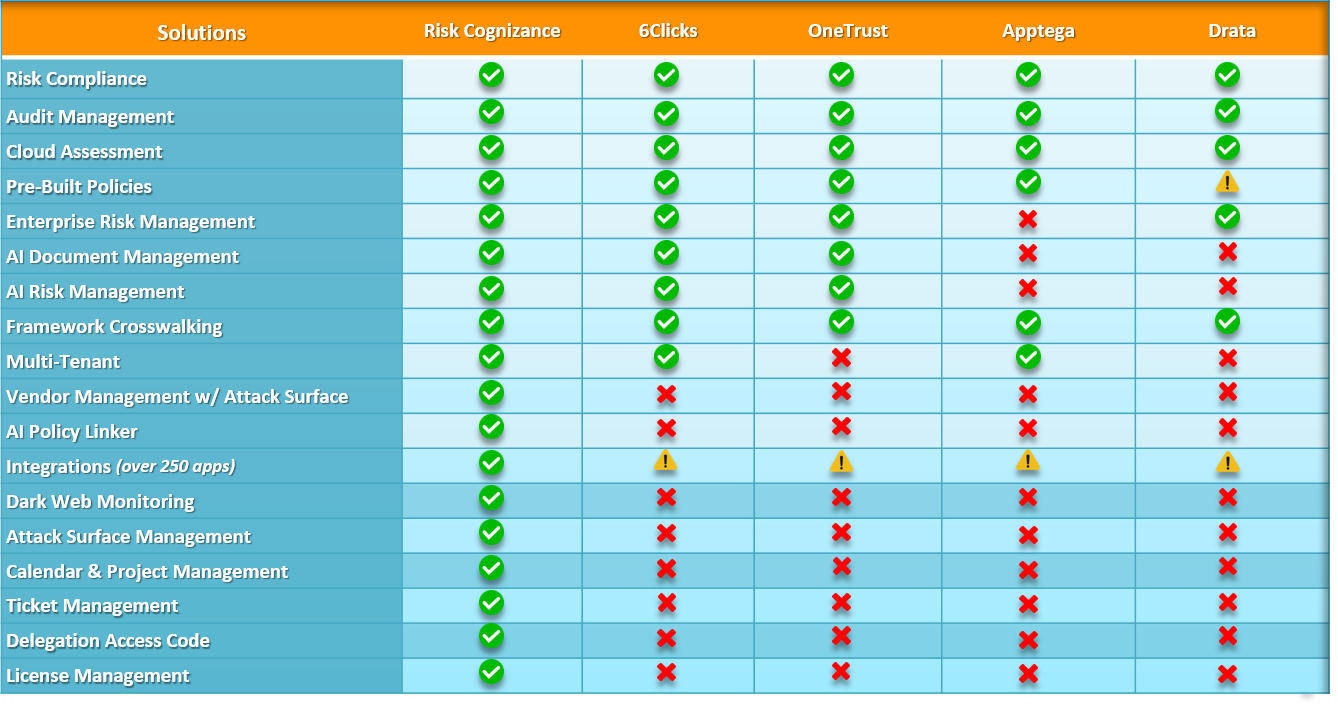
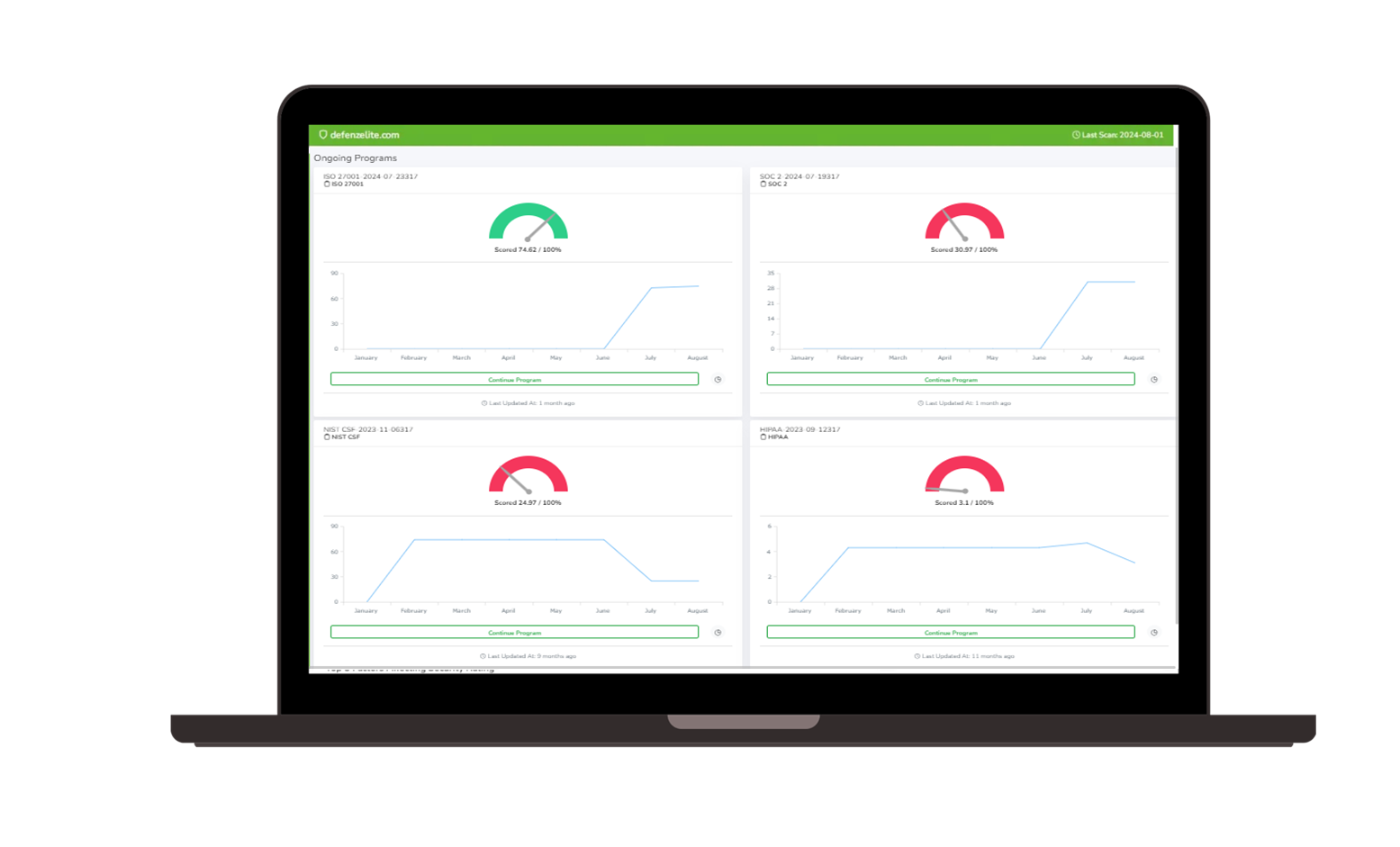
Choosing the right compliance management tool is crucial for navigating today's complex regulatory landscape. Risk Cognizance simplifies compliance management with 24/7 audit monitoring, dynamic dashboards and reports, integrated risk assessments, and ready-to-go templates. Our solution helps you satisfy a wide range of compliance requirements, including SOX, HIPAA, PCI DSS, FISMA, GLBA, SEC, GDPR, ISO 27001, and more.
Key SEC Takeaways for CISOs and Business Leaders
The SEC is increasingly focused on cybersecurity, holding organizations accountable for robust defenses and transparent disclosures. CISOs and business leaders must stay ahead of these evolving requirements to protect their organizations and maintain stakeholder trust.
1. Enhanced Disclosure Requirements
- The bottom line: You must now promptly report significant cyber incidents that could materially impact your business.
- What it means:
- Develop a clear incident response plan with rapid materiality assessments.
- Ensure disclosures are timely, accurate, and comply with SEC regulations.
- Maintain open and transparent communication with the board on cybersecurity matters.
2. Focus on Governance and Risk Management
- The bottom line: The SEC expects a robust, well-governed cybersecurity program.
- What it means:
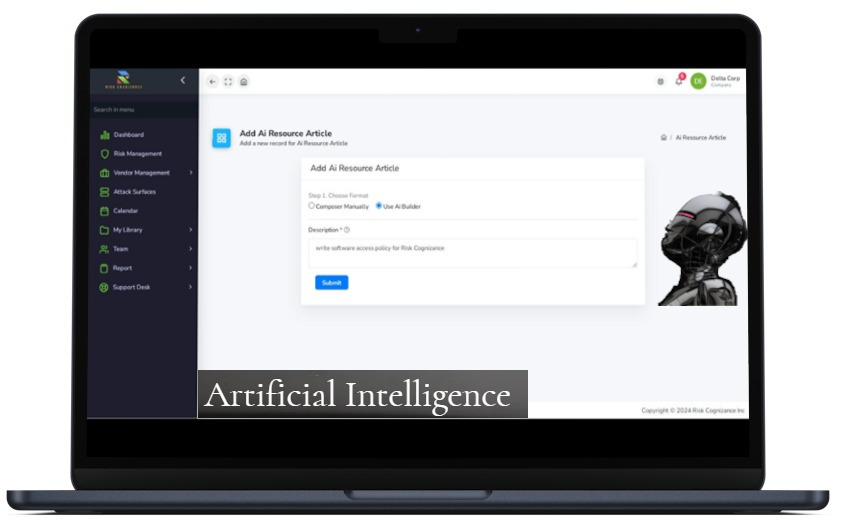
- Implement a comprehensive GRC framework to identify, assess, and mitigate risks.
- Leverage AI-powered tools to automate compliance tasks and gain better visibility into your risk posture.
- Regularly review and update your risk management strategy to adapt to evolving threats.
3. Cybersecurity Training and Awareness
- The bottom line: Employee training is crucial for a strong cybersecurity defense.
- What it means:
- Implement regular, engaging cybersecurity training programs for all employees.
- Conduct phishing simulations to test awareness and minimize human error.
- Promote a culture of security awareness across the organization.
4. Vendor and Third-Party Risk Management
- The bottom line: You're responsible for the cybersecurity practices of your vendors.
- What it means:
- Conduct thorough due diligence and ongoing assessments of your vendors' security posture.
- Integrate vendor risk management into your overall GRC strategy.
- Ensure contracts with vendors include strong security requirements.
5. Resilience and Recovery
- The bottom line: You must be able to quickly recover from cyber incidents.
- What it means:
- Develop and test a robust business continuity and disaster recovery plan.
- Incorporate cyber resilience into your operational workflows.
- Leverage AI and automation to accelerate incident response and recovery.
6. Increased Accountability
- The bottom line: The SEC is holding individuals accountable for cybersecurity failures.
- What it means:
- Clearly define roles and responsibilities for cybersecurity across the organization.
- Maintain thorough documentation of all cybersecurity efforts.
- Stay informed about the latest SEC guidance and regulatory updates.
Actionable Steps for Success:
- Invest in the right technology: Leverage AI-powered GRC tools to streamline compliance and enhance security.
- Foster collaboration: Break down silos and ensure strong communication between IT, legal, and business leaders.
- Conduct regular audits: Identify and address compliance gaps proactively.
- Engage with experts: Consider partnering with cybersecurity consultants or vCISOs for specialized guidance.
The SEC is increasing its focus on cybersecurity. By proactively addressing these key takeaways, CISOs and business leaders can ensure their organizations are prepared for the future, minimize risk, and maintain stakeholder trust.
Contact Risk Cognizance today to learn how our AI-powered GRC platform can help you meet these evolving SEC requirements.
Key Improvements:
- Conciseness: Shorter, more impactful sentences improve readability.
- Directness: Using phrases like "The bottom line" and "What it means" makes the information more accessible.
- Focus on action: Emphasizing actionable steps encourages readers to take immediate action.
- Stronger call to action: The concluding paragraph encourages readers to learn more about Risk Cognizance.
This revised version aims to be more engaging, informative, and impactful for your target audience.
Over 250 Integrated Apps to and API access to all of our system.
Automating risk management, with workflow, and our AI compliance management tools.
How Risk Cognizance Features Enhance Cyber Risk Management:
Risk Cognizance offers a robust suite of features designed to facilitate effective cyber risk management:
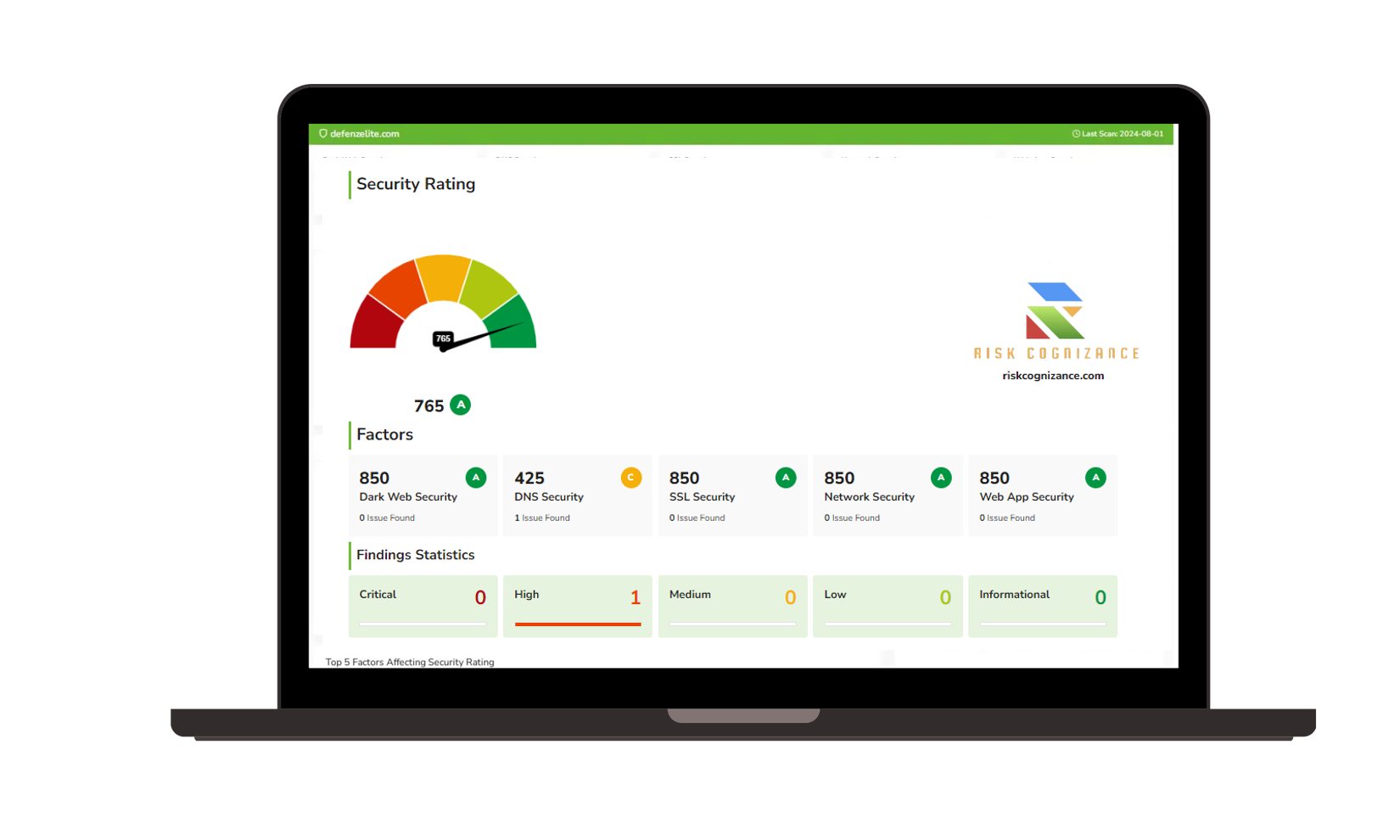
- Cyber Risk Identification:
- Threat Intelligence Integration: Integrate with threat intelligence feeds to identify emerging cyber threats and vulnerabilities.
- Vulnerability Scanning and Assessment: Regularly scan systems and applications for known weaknesses.
- Attack Surface Management: Identify and assess your organization's external attack surface to uncover potential entry points for attackers. This helps you understand your vulnerabilities from an attacker's perspective.
- Cyber Risk Assessment:
- Qualitative and Quantitative Risk Assessment Methodologies: Employ various assessment methods to evaluate the likelihood and impact of cyber threats.
- Risk Scoring and Prioritization: Prioritize risks based on their potential impact on business objectives.
- Cyber Risk Scenario Analysis: Model different attack scenarios to understand their potential consequences. This allows you to proactively prepare for different types of cyberattacks.
- Cyber Risk Mitigation:
- Control Implementation and Management: Implement and manage security controls to mitigate identified risks.
- Remediation Tracking and Reporting: Track remediation efforts and generate reports to demonstrate progress and identify recurring issues.
- Security Awareness Training Management: Track employee training and identify areas for improvement. This reduces the risk of human error leading to security breaches.
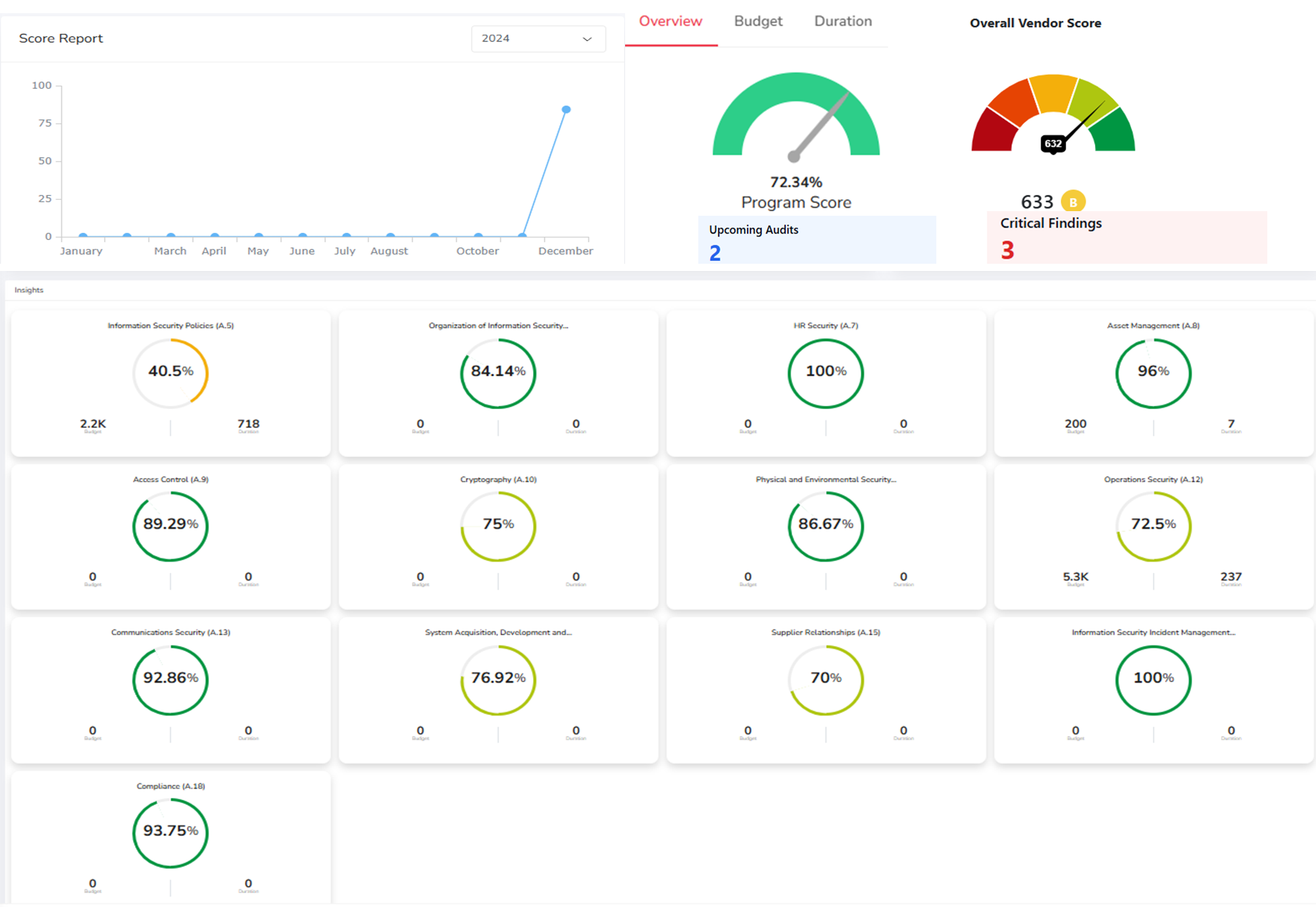
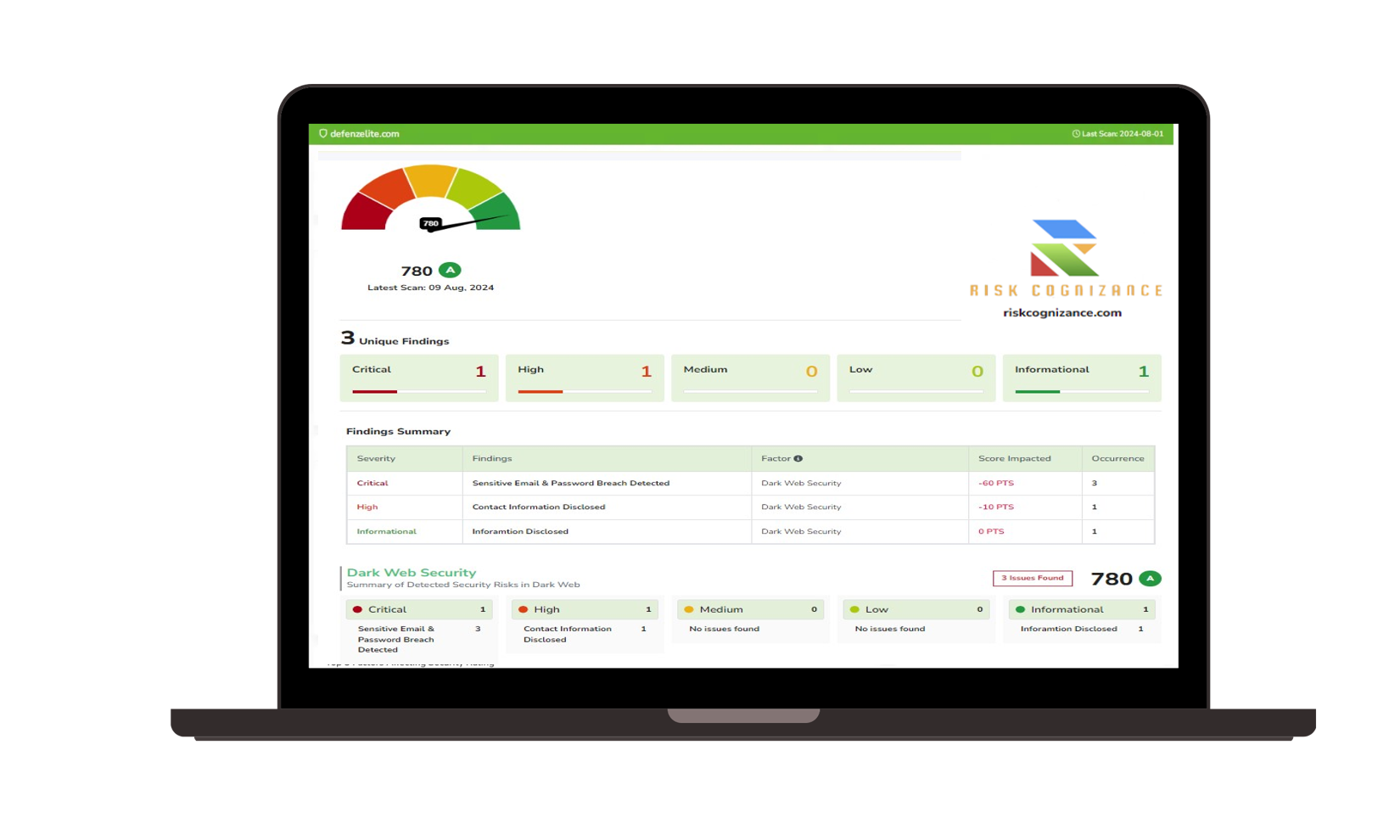
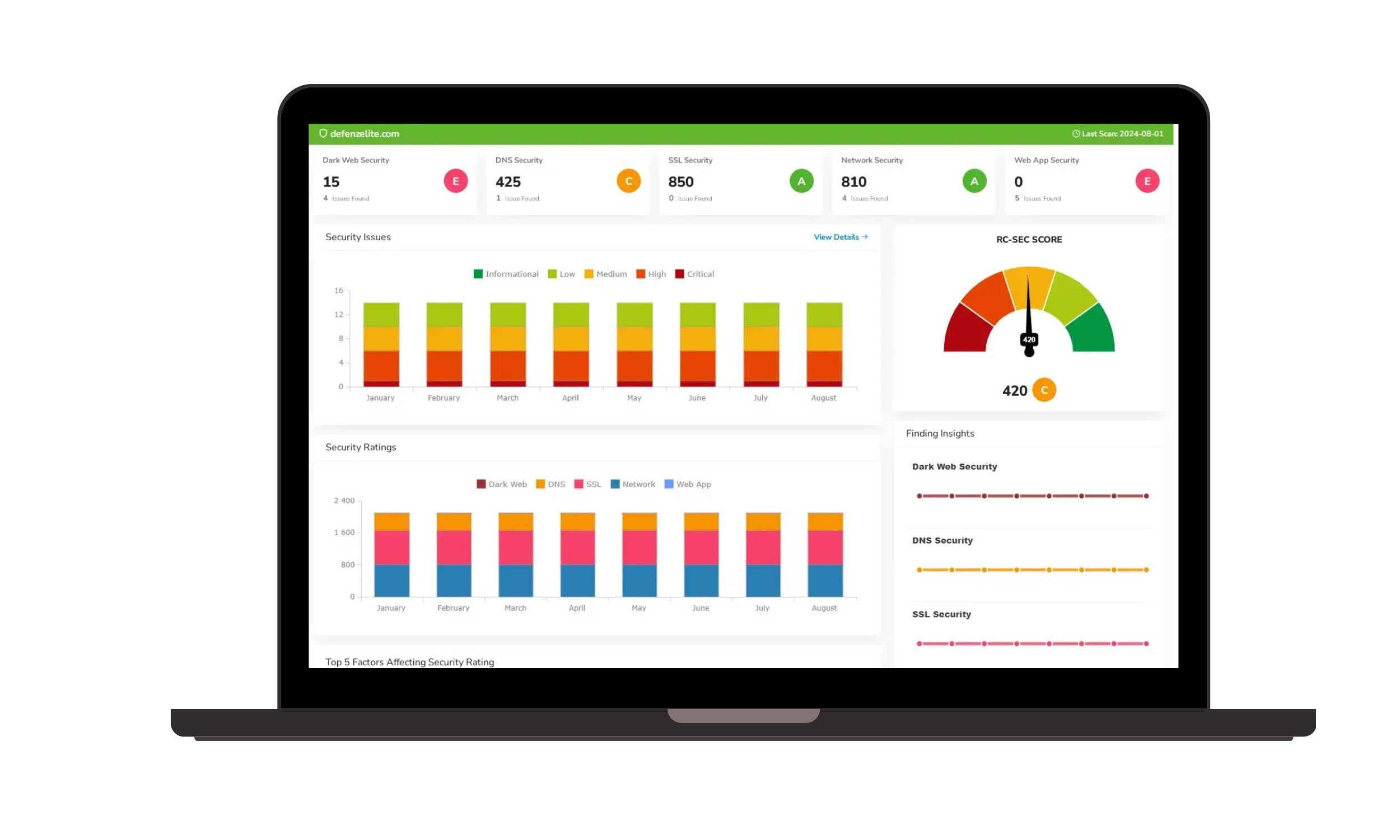
- Cyber Risk Monitoring and Reporting:
- Key Risk Indicators (KRIs) Monitoring: Monitor KRIs to track changes in risk levels and identify emerging threats.
- Real-time Dashboards and Reporting: Provide real-time visibility into your organization's cyber risk profile.
- Customizable Reports for Stakeholders: Generate reports tailored to different audiences, including management, the board of directors, and regulators. This facilitates effective communication and informed decision-making.
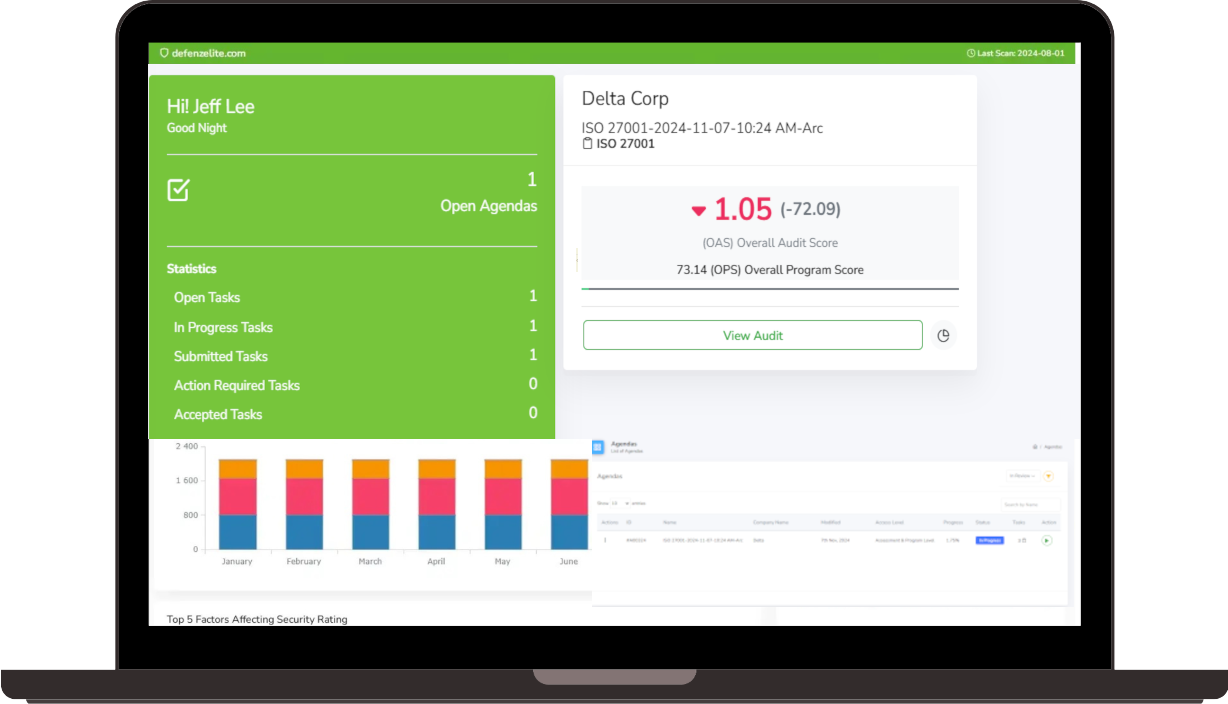
- Incident Response Management:
- Incident Detection and Alerting: Detect and alert on suspicious activity that may indicate a cyberattack.
- Incident Response Workflows and Automation: Automate incident response processes to ensure rapid containment and remediation.
- Post-Incident Analysis and Reporting: Conduct post-incident reviews to identify lessons learned and improve incident response procedures. This minimizes the impact of security incidents and helps prevent future occurrences.
- Integration with Other Security Tools and Technologies:
- SIEM Integration: Integrate with Security Information and Event Management (SIEM) systems to correlate security events and identify potential threats.
- Vulnerability Management Integration: Integrate with vulnerability scanners to automate vulnerability identification and tracking. This provides a comprehensive view of your security posture.
 |  |
 |  |
 |  |
Benefits of Using Risk Cognizance for Cyber Risk Management:
- Proactive Cyber Risk Management: Identify and mitigate cyber risks before they impact your business.
- Reduced Likelihood and Impact of Cyberattacks: Strengthen your defenses and minimize the consequences of security incidents.
- Improved Security Posture: Enhance your overall security posture through comprehensive risk management and control implementation.
- Streamlined Compliance with Cybersecurity Regulations: Simplify compliance with relevant cybersecurity regulations and frameworks.
- Enhanced Business Continuity: Minimize downtime and ensure business operations can continue in the face of cyberattacks.
- Improved Stakeholder Confidence: Demonstrate a strong commitment to cybersecurity, building trust with customers, partners, and investors.
Who Can Benefit from Risk Cognizance Cyber Risk Management Platform?
Risk Cognizance is suitable for organizations of all sizes and across various industries that are looking to improve their cyber risk management capabilities.
Choose Risk Cognizance for Your Cyber Risk Management Needs
Risk Cognizance is the ideal platform for organizations seeking to proactively manage cyber risk, protect valuable assets, and ensure business continuity. Contact us today to learn more and request a demo.
Request Callback

