Overview
Gain Complete Visibility and Proactive Control of Your Cyber Risk
Our comprehensive Attack Surface Management and Cyber Assessment services help you identify, prioritize, and mitigate vulnerabilities before they can be exploited by attackers.
Risk Cognizance Attack Surface Management (ASM) provides comprehensive visibility into your digital infrastructure by:
- Discovering and mapping all internet-facing assets across dynamic, distributed, and cloud-shared environments
- Continuously monitoring your external ecosystem for critical vulnerabilities and potential exploitable exposures
- Proactively identifying risks before attackers can leverage them
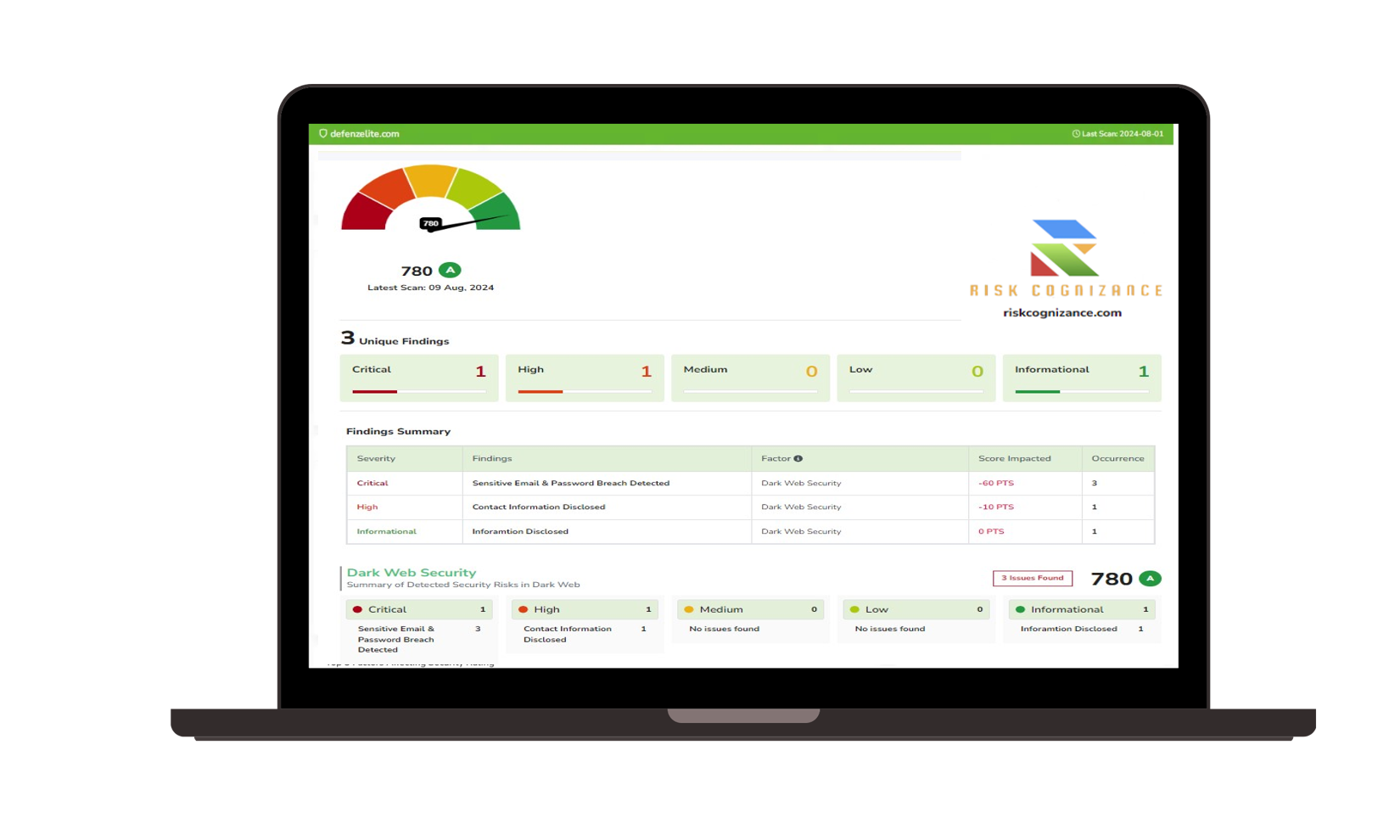
What Is Attack Surface Management?
Attack surface management (ASM) is the process of continuously identifying, monitoring and managing all internal and external internet-connected assets.
Attack surface reduction refers to minimizing the points in a system where an unauthorized user could infiltrate or exploit it. It involves identifying and reducing possible entry points for attackers by eliminating unnecessary functionalities, services, and permissions within a system. This approach aims to lower the risk of attacks by limiting the options available to threat actors.
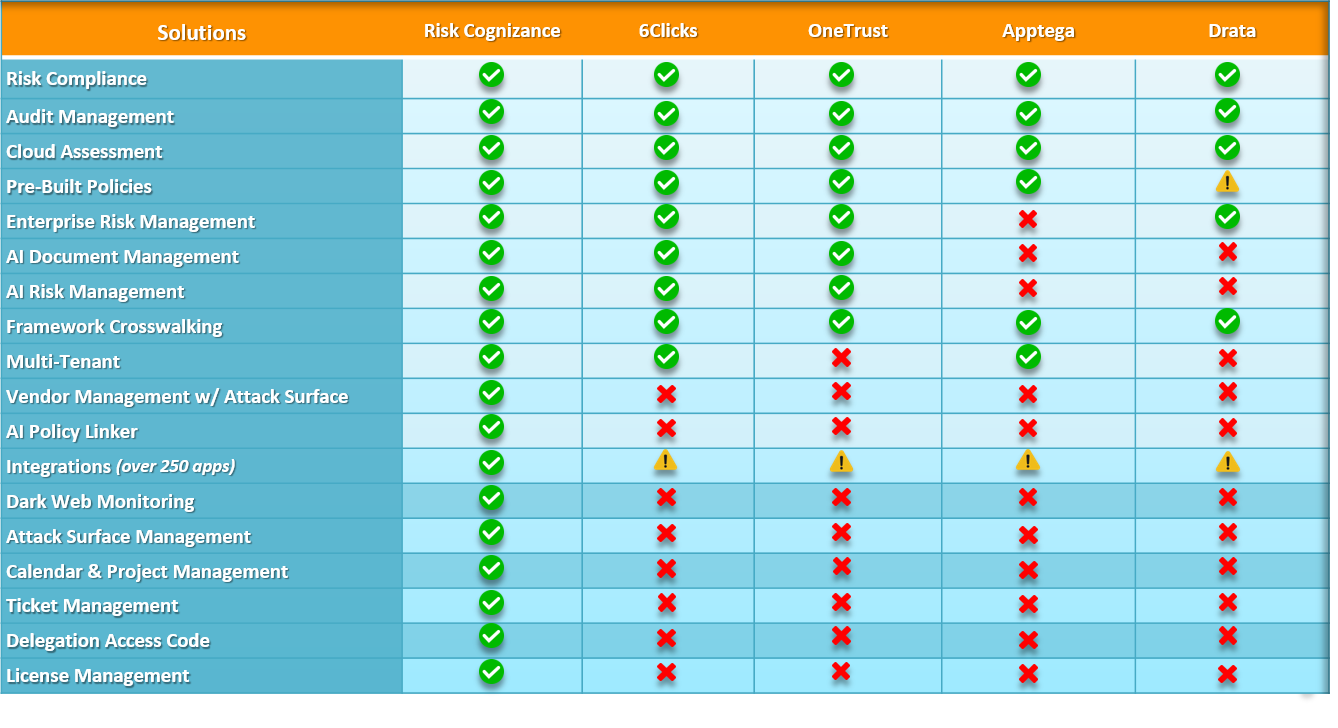
Attack Surface Management Key Services:
Continuous Attack Surface Monitoring:
- Discover and continuously monitor all internet-facing assets, including websites, cloud services, IoT devices, and third-party vendors.
- Identify and track new and emerging threats in real-time.
- Gain deep visibility into your organization's entire attack surface.
Vulnerability Assessment & Penetration Testing:
- Conduct thorough vulnerability assessments to identify and prioritize critical security weaknesses.
- Perform ethical penetration testing to simulate real-world attack scenarios and uncover exploitable vulnerabilities.
- Gain actionable insights to guide your remediation efforts.
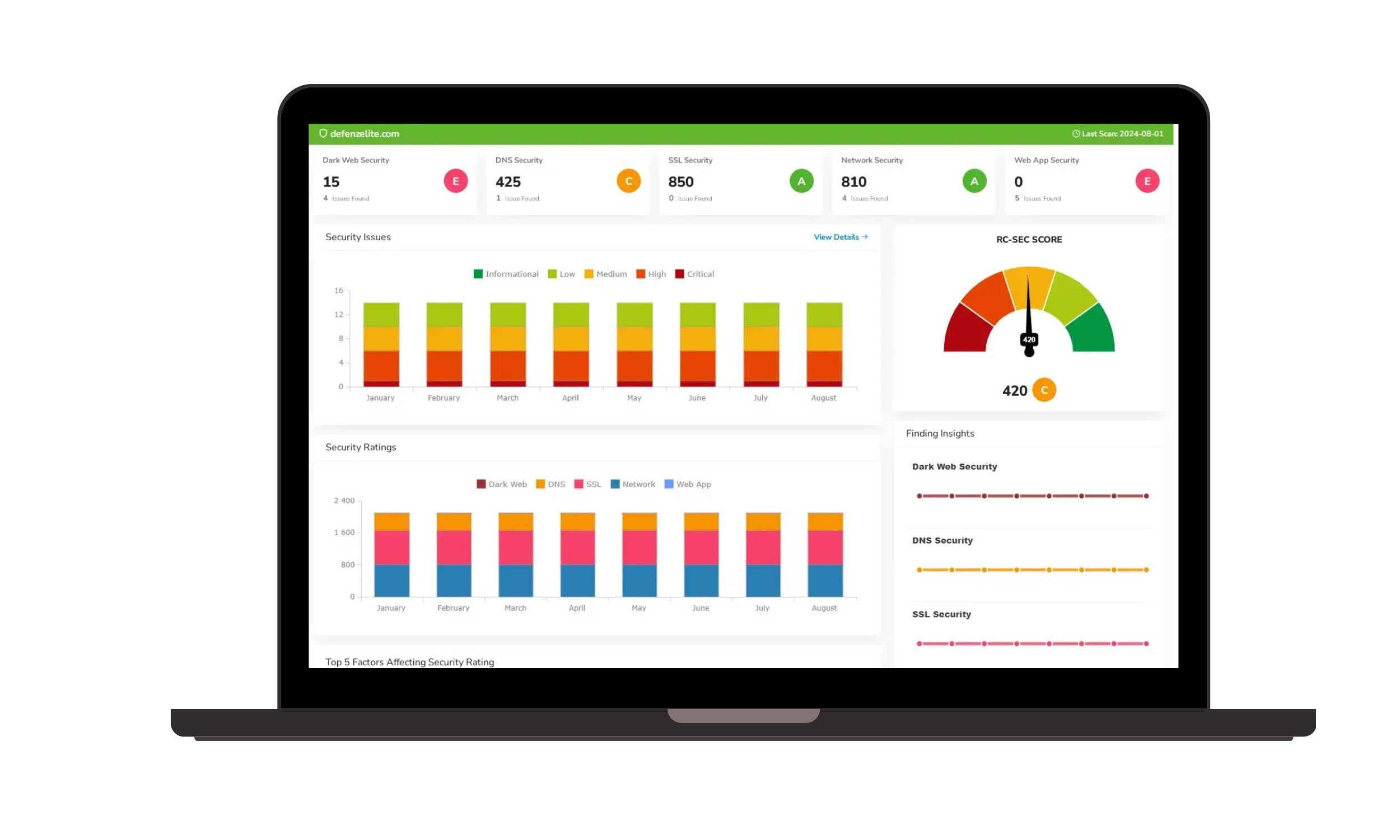
Threat Intelligence & Risk Analysis:
- Leverage threat intelligence feeds to stay informed of the latest cyber threats and attack vectors.
- Conduct comprehensive risk assessments to prioritize vulnerabilities based on their potential impact.
- Develop effective risk mitigation strategies to protect your organization.
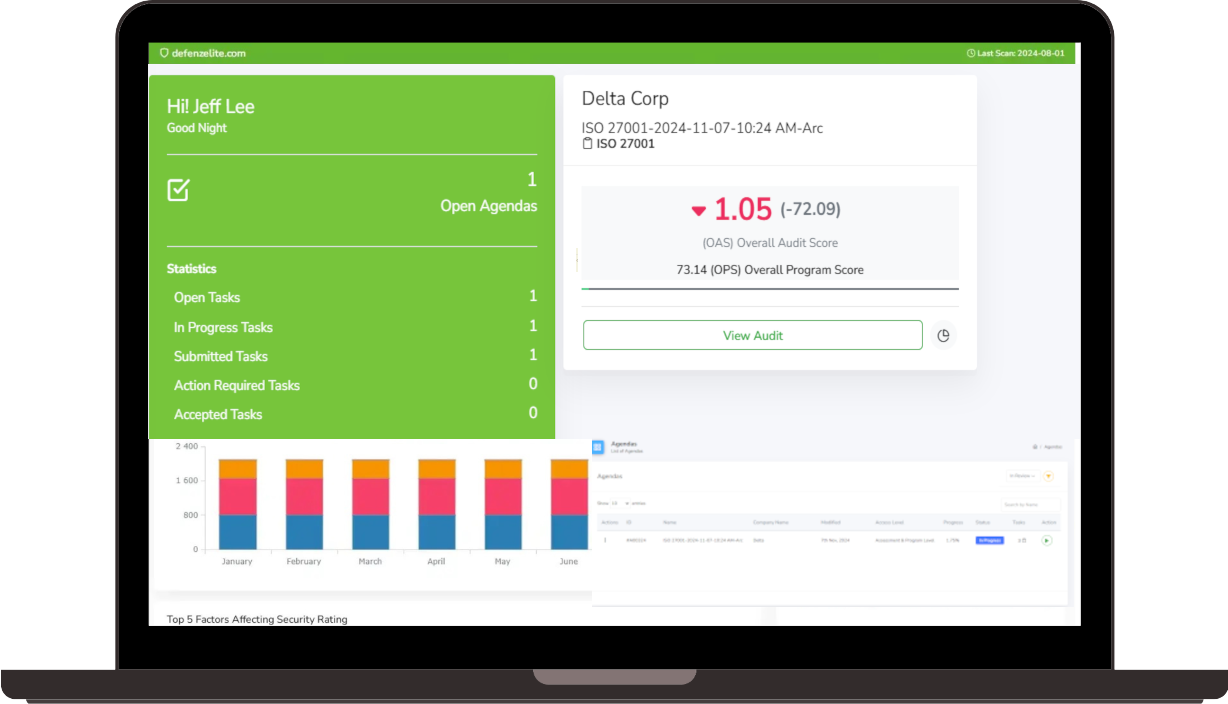
Compliance & Regulatory Support:
- Ensure compliance with industry standards and regulations, such as GDPR, PCI DSS, and HIPAA.
- Conduct regular compliance audits and gap assessments.
- Develop and implement robust security controls to meet regulatory requirements.
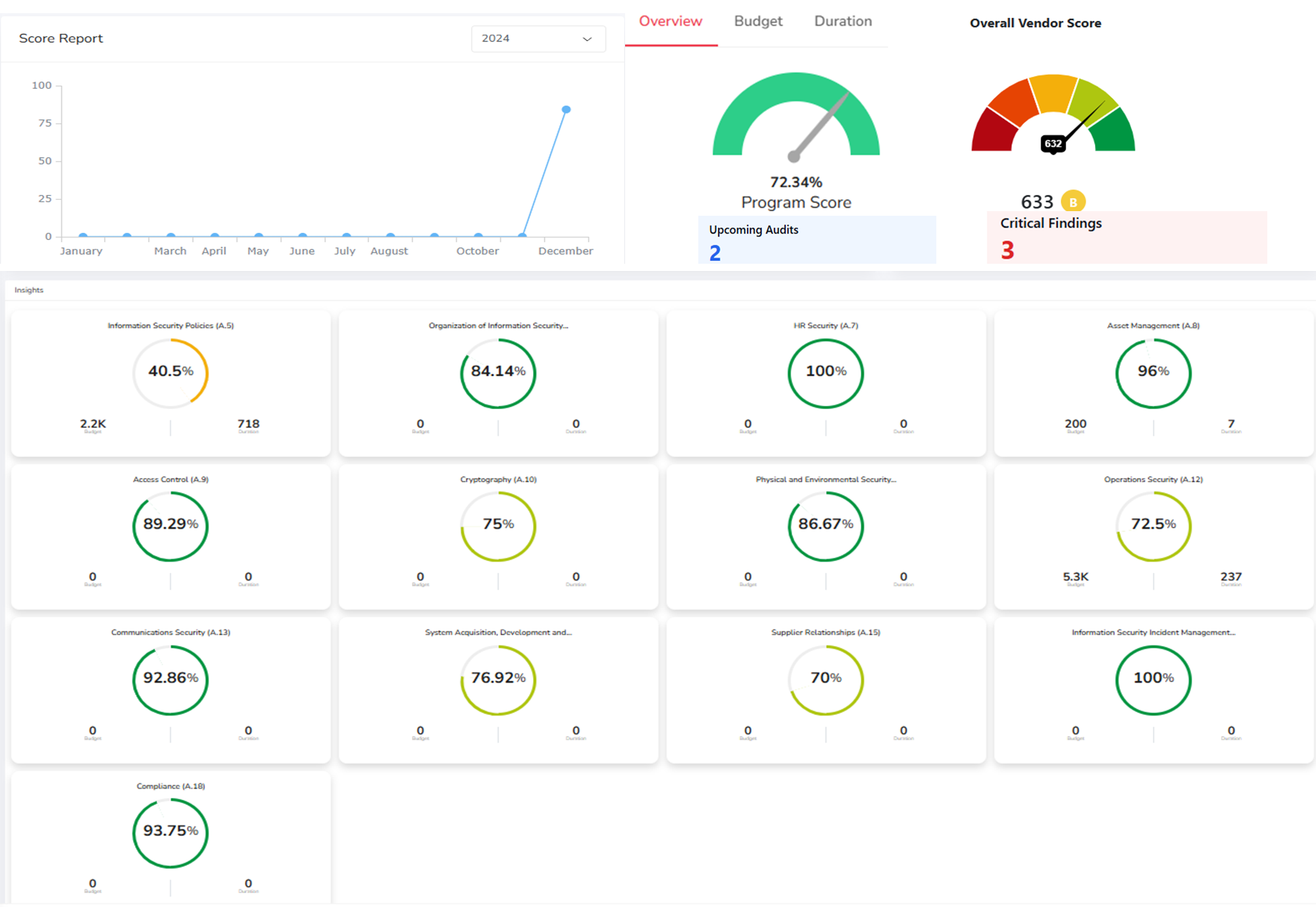
What is External Attack Surface Management?
External Attack Surface Management (EASM) refers to the processes, technology and managed services deployed to discover internet-facing enterprise assets and systems and associated exposures which include misconfigured public cloud services and servers, exposed enterprise data such as credentials and third-party partner software code vulnerabilities that could be exploited by adversaries. EASM provides valuable risk prioritization and context and actionable information through regular or continuously monitoring and discovery for external-facing assets and systems. External attack surface management is a top priority for security teams and security risk managers.
Attack Surface Management and Cyber Assessment Benefits:
- Reduce your organization's overall cyber risk.
- Proactively identify and mitigate vulnerabilities before they are exploited.
- Improve your organization's security posture.
- Gain a competitive advantage in the marketplace.
- Demonstrate a strong commitment to cybersecurity to customers and stakeholders.
- Meet compliance requirements and avoid costly fines.
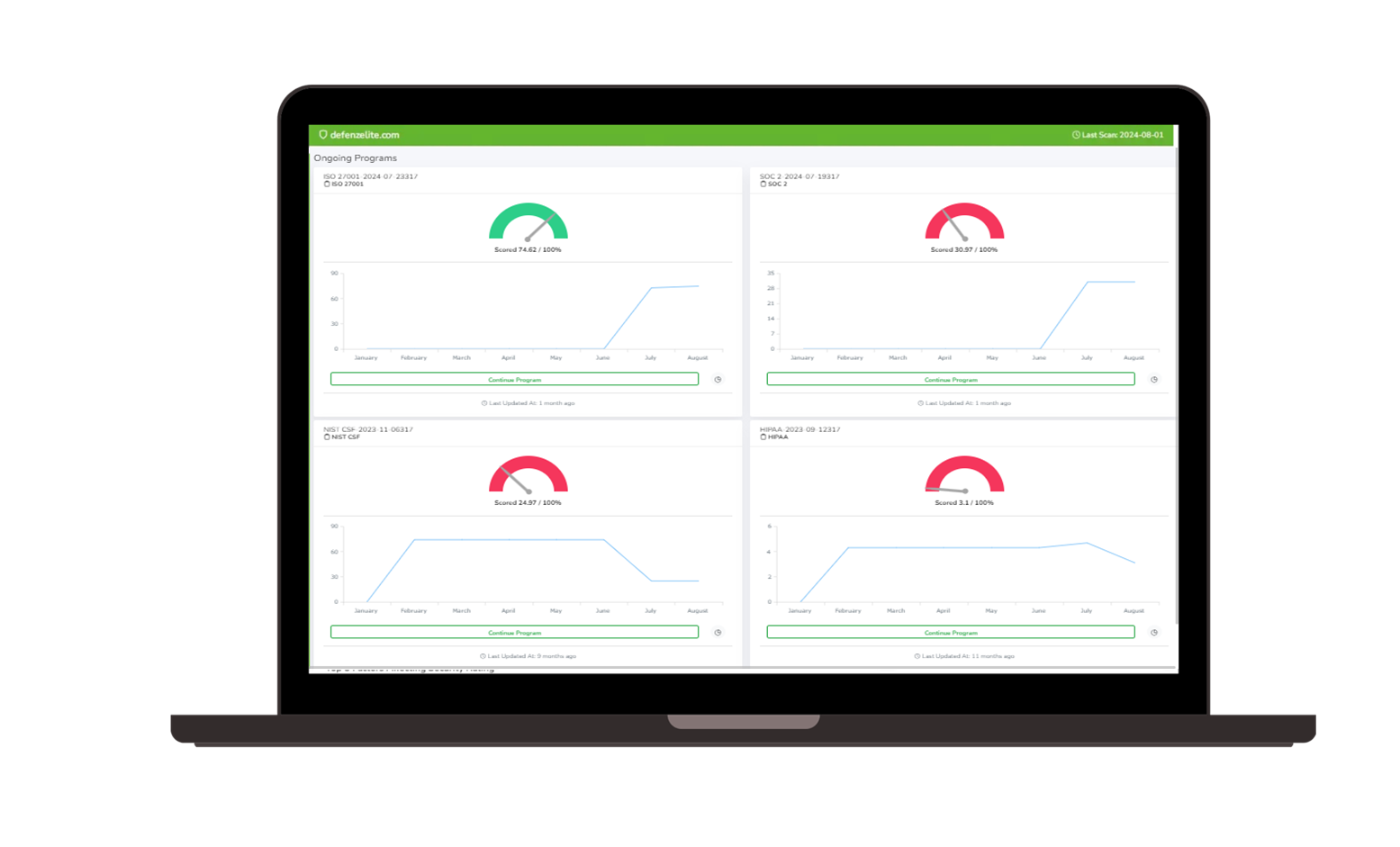 | 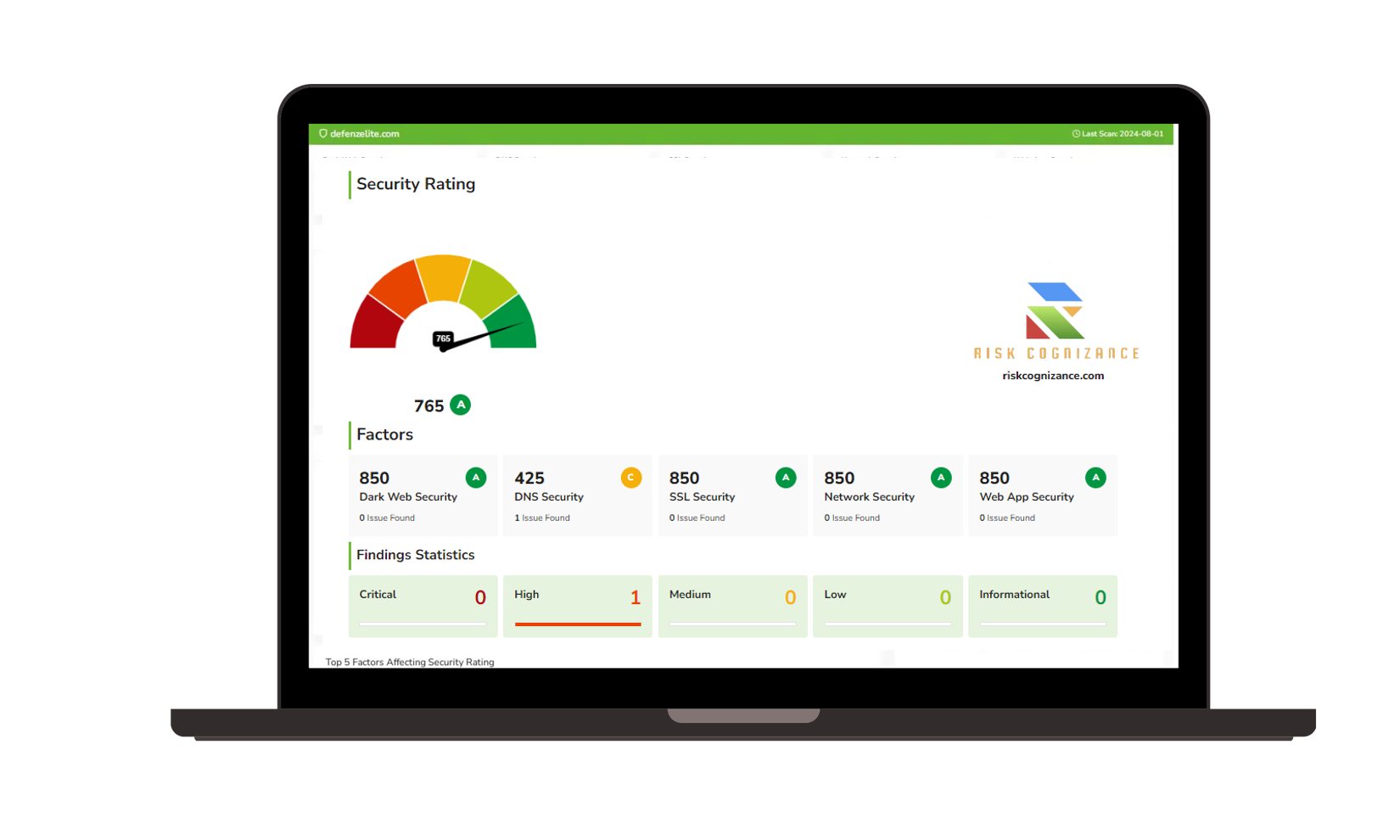 |
 |  |
 |  |
Risk Cognizance Attack Surface Management customers have provided their real-world testimonials in Gartner Peer Insights™.
Contact us today to schedule a consultation and learn how our Attack Surface Management & Cyber Assessment services can help you protect your organization from cyber threats.
Request Callback
