Overview
Take Control of Your Cyber Security with Risk Cognizance's Cutting-Edge IT & Cyber Risk Management Software.
Cyber threats are constantly evolving, posing significant risks to businesses of all sizes. From data breaches and ransomware attacks to compliance violations and reputational damage, the consequences of cyber incidents can be devastating.
Risk Cognizance's IT & Cyber Risk Management Software provides a comprehensive solution to help you proactively identify, assess, and mitigate cyber risks. Our platform empowers you to:
- Gain Visibility: Gain a 360-degree view of your entire IT infrastructure and identify potential vulnerabilities.
- Prioritize Risks: Assess and prioritize risks based on their potential impact and likelihood of occurrence.
- Automate Compliance: Ensure compliance with industry regulations (e.g., GDPR, HIPAA, SOC 2) through automated checks and streamlined audits.
- Detect Threats in Real-Time: Monitor for threats 24/7 and receive real-time alerts to enable rapid response.
- Improve Incident Response: Streamline incident response processes to minimize downtime and mitigate the impact of cyberattacks.
- Make Data-Driven Decisions: Leverage powerful analytics and reporting to make informed decisions about your cybersecurity posture.
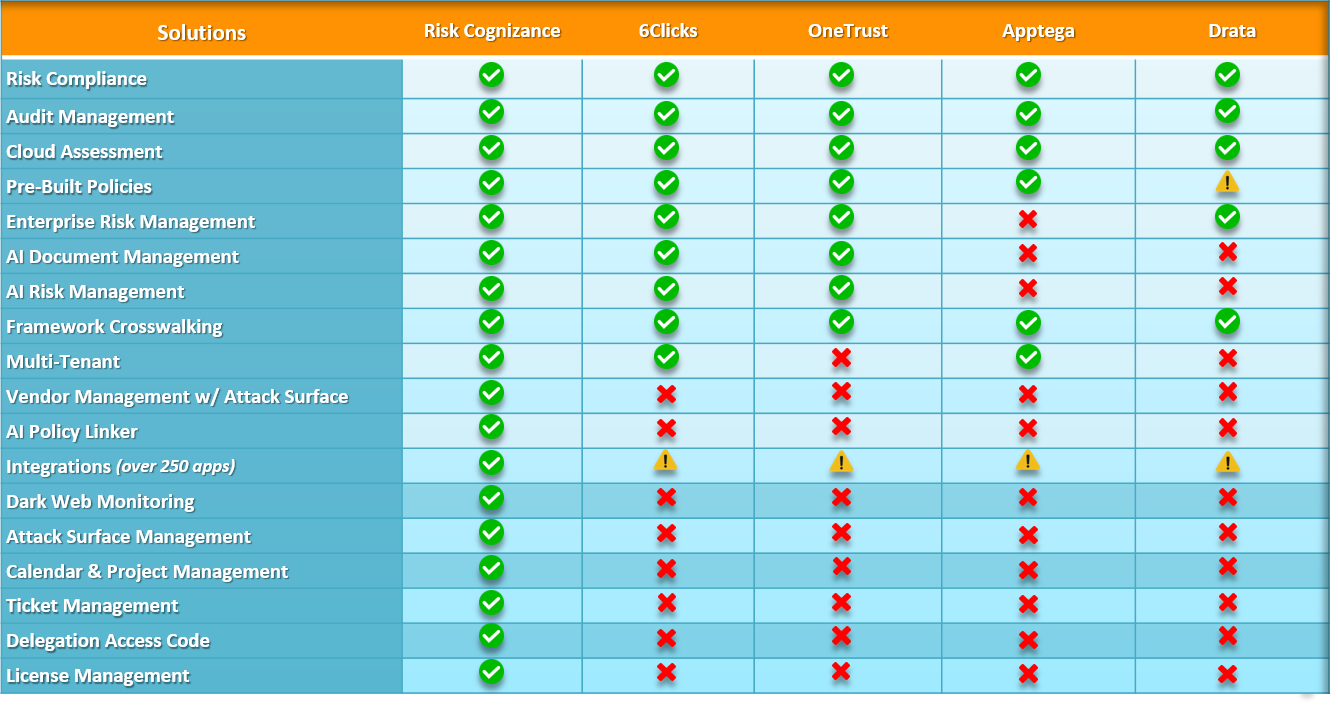
IT & Cyber Risk Management Key Features:
- Threat Intelligence: Access real-time threat intelligence feeds to stay ahead of emerging threats.
- Vulnerability Scanning & Assessment: Continuously scan your systems for vulnerabilities and prioritize remediation efforts.
- Security Information and Event Management (SIEM): Collect, analyze, and correlate security logs to detect and respond to threats.
- Endpoint Detection and Response (EDR): Monitor and protect endpoints from malware, ransomware, and other threats.
- Data Loss Prevention (DLP): Prevent sensitive data from leaving your organization's network.
- Compliance Management: Automate compliance checks and generate reports to demonstrate adherence to industry regulations.
- Third-Party Risk Management: Assess and monitor the security posture of third-party vendors.
- Incident Response Planning & Management: Develop and test incident response plans and streamline incident response processes.
IT Risk Management Software Benefits:
- Reduced Risk of Cyberattacks: Proactively identify and mitigate cyber threats before they can cause significant damage.
- Enhanced Compliance: Ensure compliance with industry regulations and avoid costly fines and penalties.
- Improved Security Posture: Strengthen your overall security posture and protect your valuable assets.
- Increased Efficiency: Automate security tasks and free up your IT team to focus on strategic initiatives.
- Improved Decision Making: Gain valuable insights into your security posture and make informed decisions about your cybersecurity investments.
Risk Cognizance's commitment to excellence:
- Expert Support: Our team of experienced cybersecurity experts provides ongoing support and guidance.
- Scalability and Flexibility: Our platform scales with your business needs and can be customized to meet your specific requirements.
- Continuous Innovation: We are constantly innovating and enhancing our platform to stay ahead of the evolving threat landscape.
 |  |
 |  |
 |  |
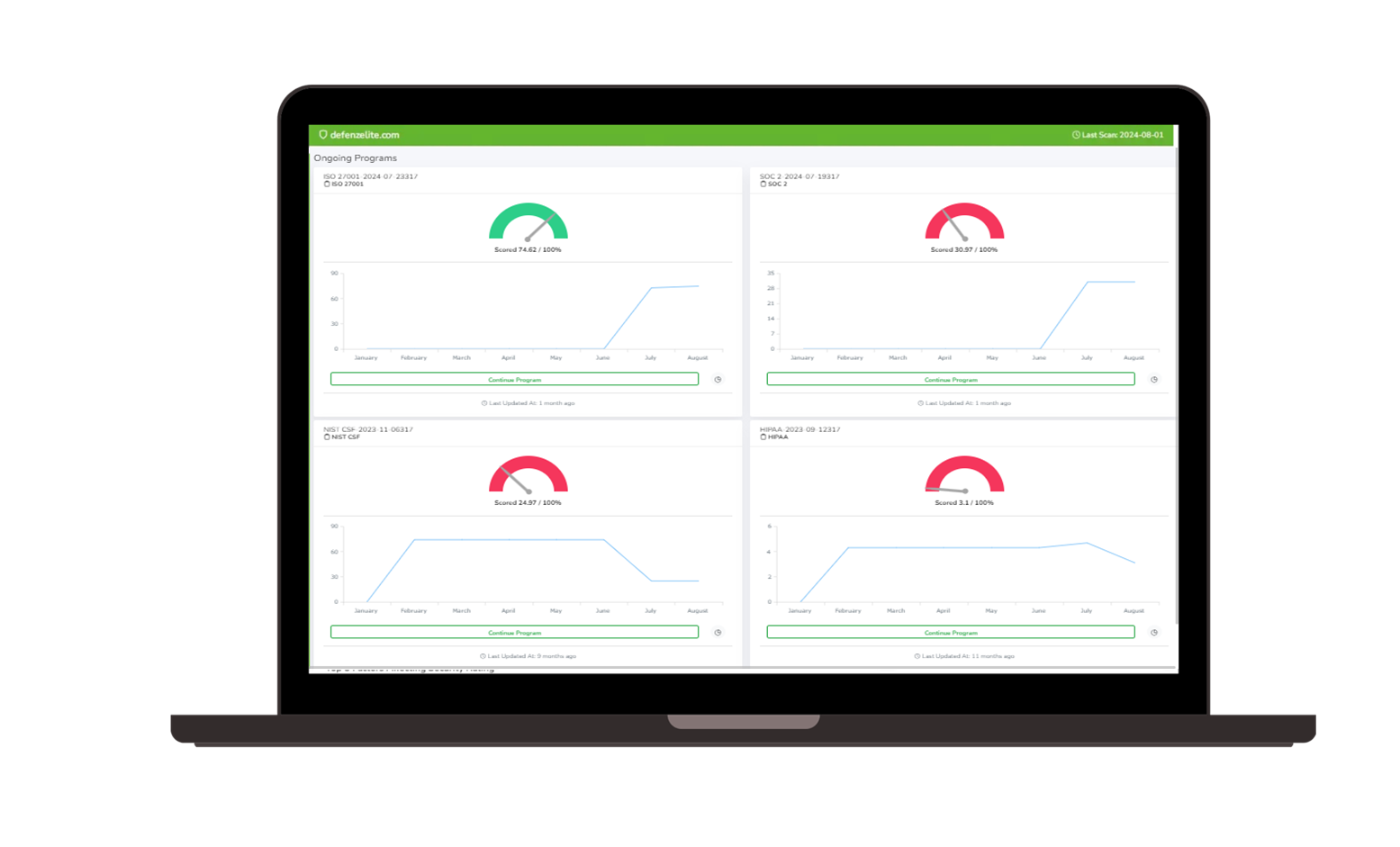
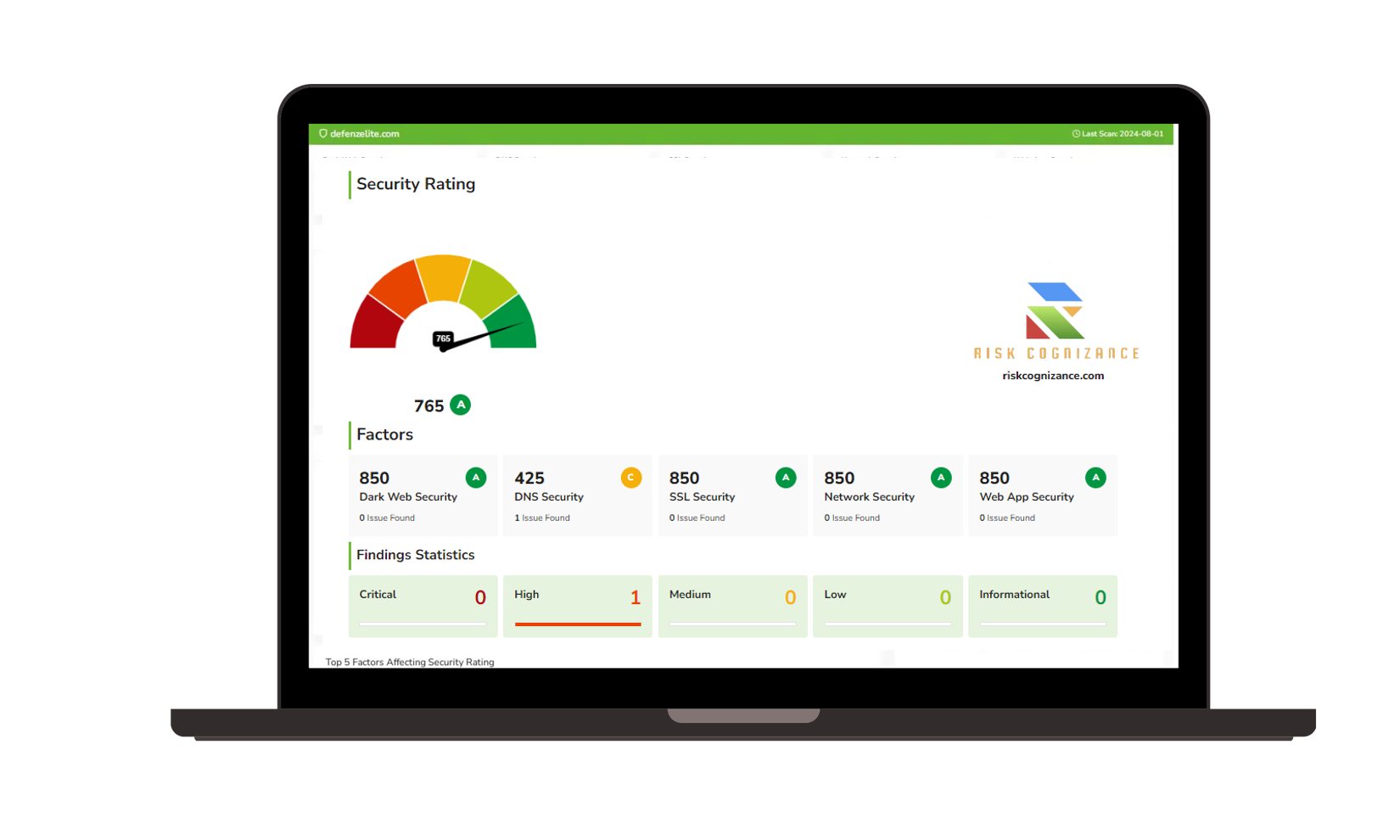
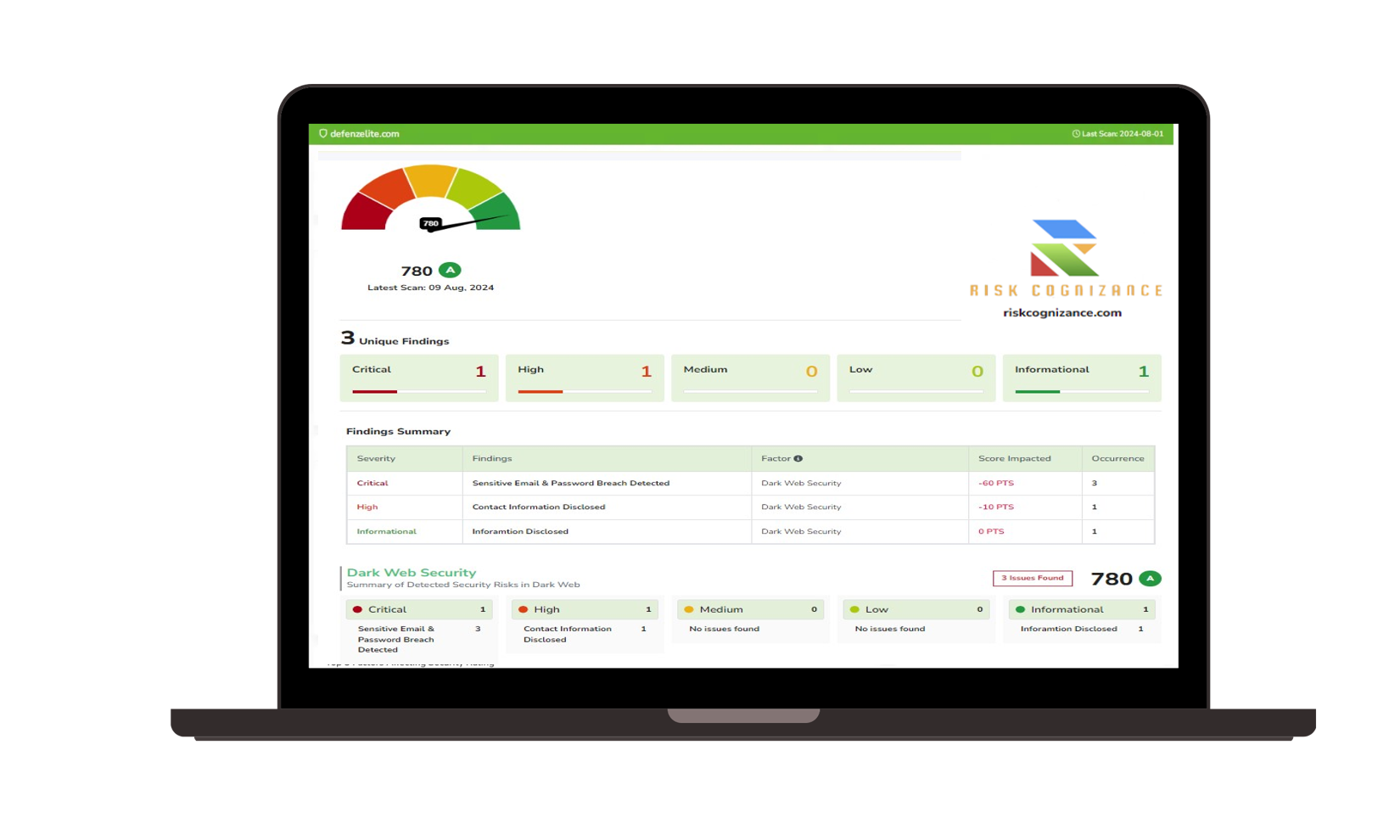
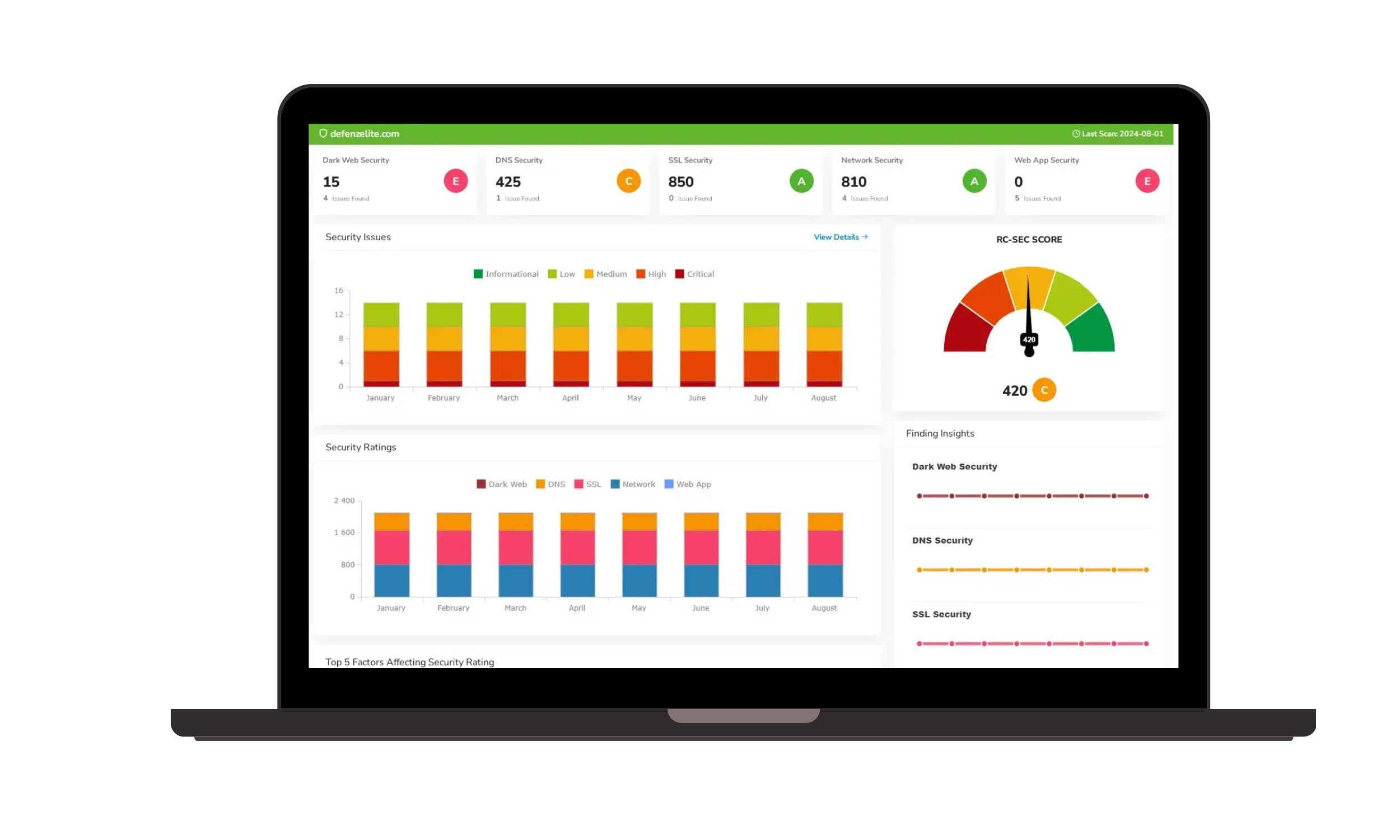
Strengthen Cyber Resilience with Risk Cognizance's IT & Cyber Risk Management Software
IT Risk Management software helps to strengthen cyber resilience by streamlining the process of managing and mitigating IT and cyber risks and threats.
Boost Your Risk Management with Proactive Risk Identification
- Proactive Risk Identification:
- Continuously monitor for vulnerabilities and threats across your IT infrastructure.
- Identify and assess potential risks before they can cause significant damage.
- Enhanced Threat Detection:
- Leverage advanced threat intelligence and real-time monitoring to detect and respond to cyberattacks quickly.
- Utilize features like Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) to identify and contain threats.
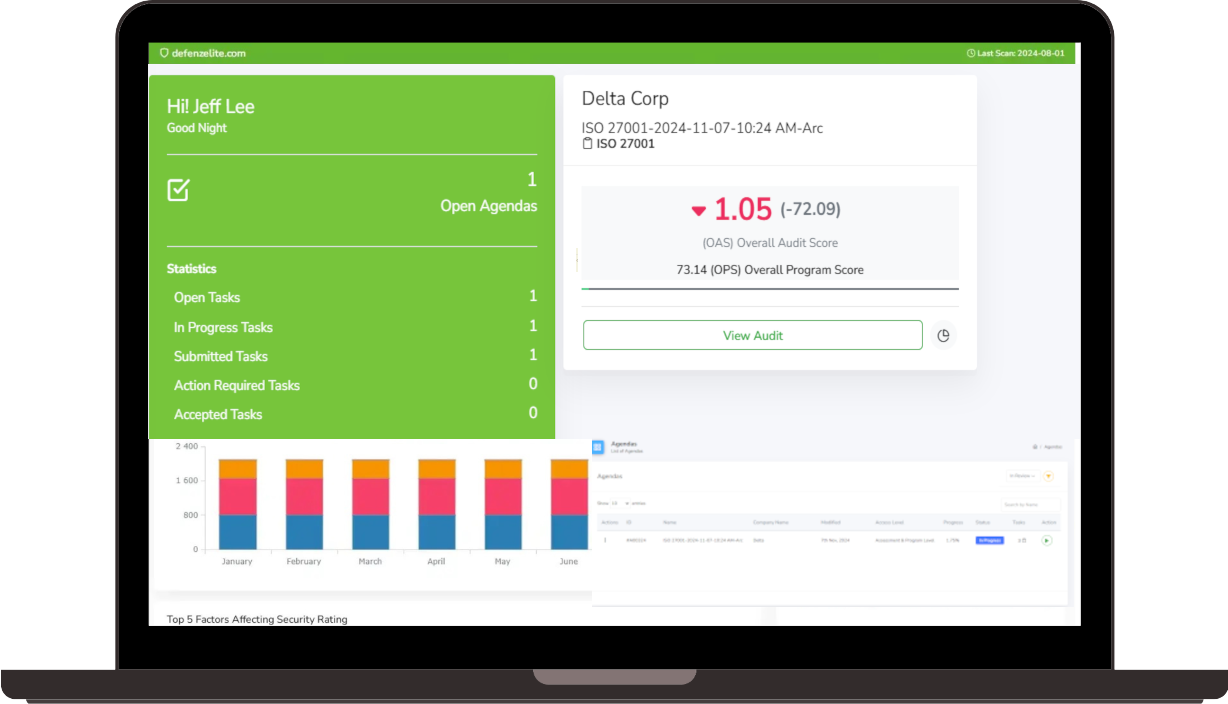
- Improved Incident Response:
- Streamline incident response processes with automated workflows and pre-defined playbooks.
- Minimize downtime and mitigate the impact of cyberattacks.
- Automated Compliance:
- Ensure compliance with industry regulations (e.g., GDPR, HIPAA, SOC 2) through automated checks and streamlined audits.
- Reduce the burden of manual compliance tasks and minimize the risk of non-compliance penalties.
- Data-Driven Decision Making:
- Gain valuable insights into your organization's risk profile through comprehensive reporting and analytics.
- Make informed decisions about your cybersecurity investments based on data-driven insights.
- Increased Efficiency:
- Automate repetitive tasks, such as vulnerability scanning and risk assessments, freeing up your IT team to focus on strategic initiatives.
- Improved Security Posture:
- Strengthen your overall security posture and build a more resilient organization.
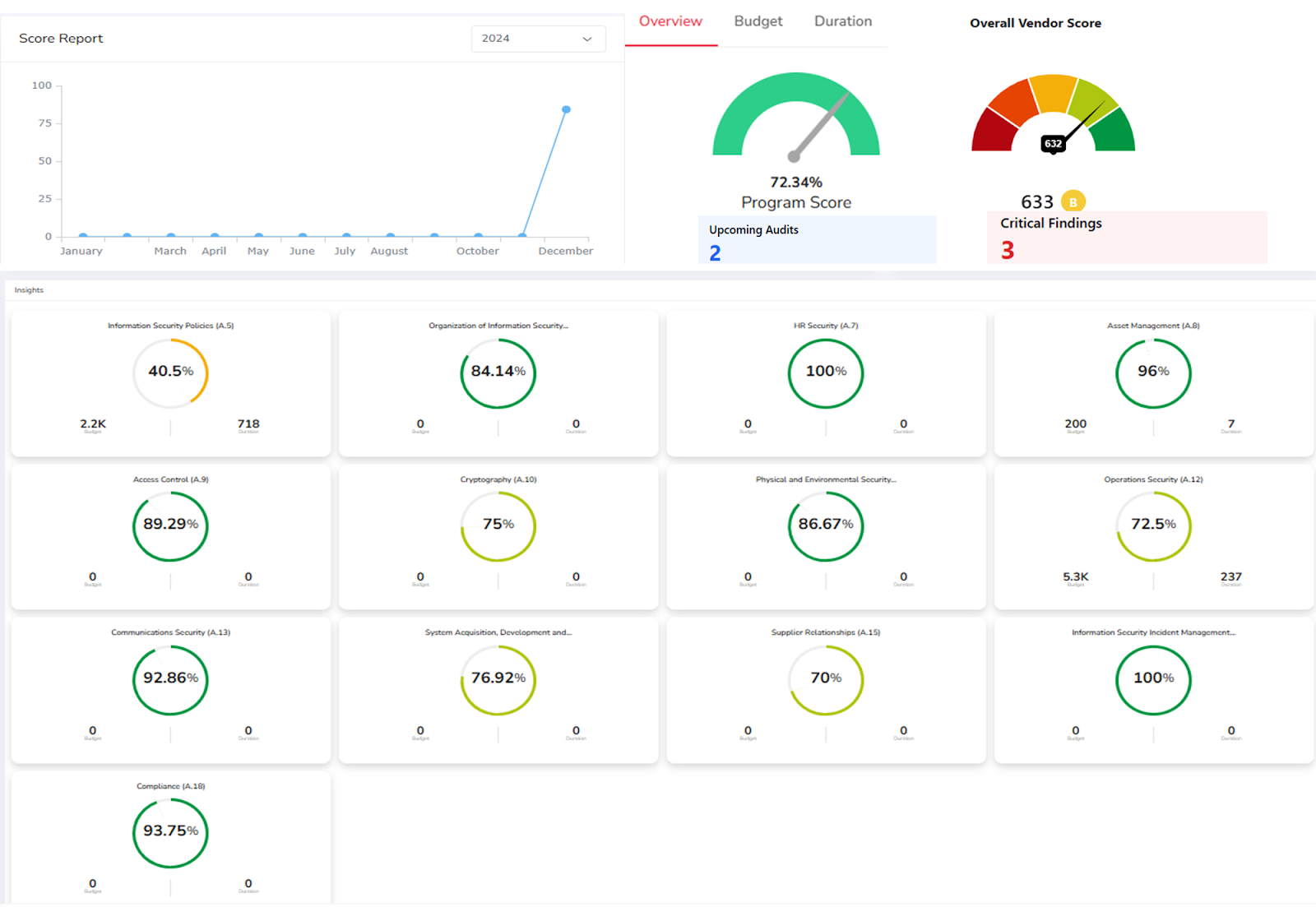
Faster compliance with continuous compliance management insight
- Vulnerability Management:
- Continuous vulnerability scanning and assessment.
- Prioritization of vulnerabilities based on risk severity.
- Threat Intelligence:
- Access to real-time threat intelligence feeds.
- Integration with threat intelligence platforms.
- Compliance Management:
- Automated compliance checks and reporting.
- Streamlined audit preparation and execution.
- Incident Response Management:
- Incident response planning and management capabilities.
- Automated incident response workflows.
- Risk Assessment and Prioritization:
- Risk assessments based on industry best practices and regulatory requirements.
- Prioritization of risks based on impact and likelihood.
- Reporting and Analytics:
- Customizable dashboards and reports to track key risk indicators (KPIs).
- Data-driven insights to inform risk management decisions.
By leveraging Risk Cognizance IT Risk Management software, organizations can proactively address cyber threats, enhance their security posture, and build a more resilient and secure IT environment.
Schedule a free demo today and discover how Risk Cognizance's IT & Cyber Risk Management Software can help you protect your business from cyber threats.
Request Callback
