Overview
Virtual CISO (vCISO) Services and Compliance Software Solutions: A Comprehensive Guide
Struggling with cybersecurity management costs? Discover how Virtual CISO (vCISO) services and Compliance-as-a-Service (CaaS) software can transform your organization's security posture while reducing expenses. This comprehensive guide explores everything you need to know about implementing virtual security leadership and automated compliance solutions.
What is a Virtual CISO (vCISO)? Understanding Modern Security Leadership
Essential vCISO Services:
- Enterprise security strategy development and execution
- Comprehensive cyber risk management programs
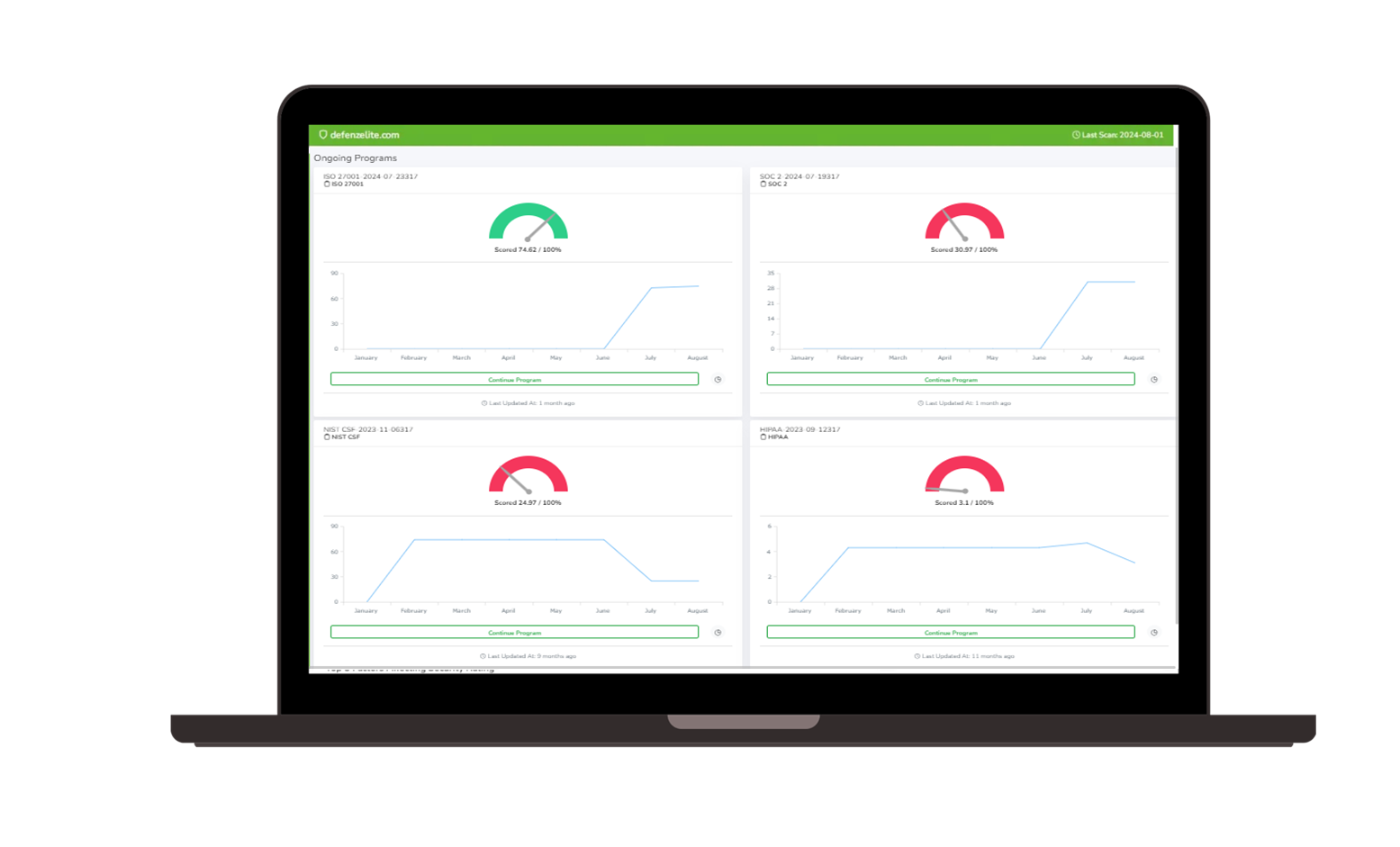
- Regulatory compliance oversight (HIPAA, SOC 2, ISO 27001, GDPR)
- Information security policy framework implementation
- Real-time security incident response management
 |  |
 |  |
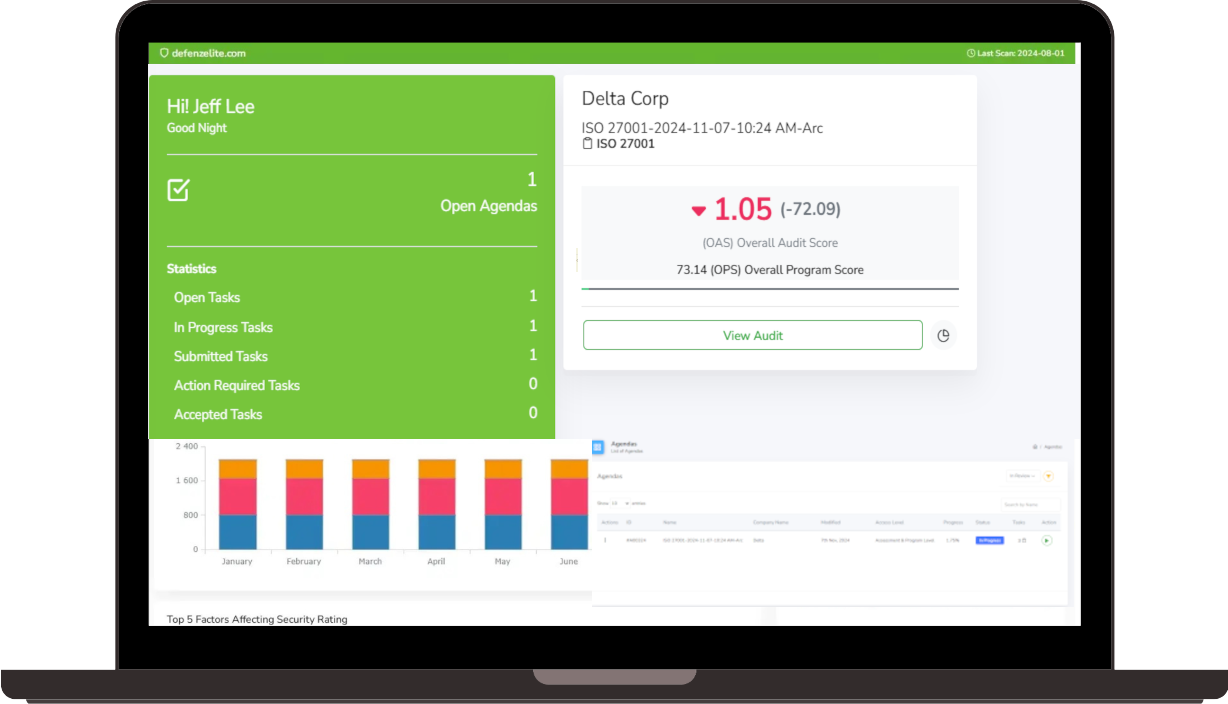 |  |
Compliance-as-a-Service (CaaS) Platform Benefits
Risk Cognizance Compliance-as-a-Service (CaaS) platform offers several benefits, including: cost-effectiveness by reducing the need for dedicated compliance staff, access to expert knowledge on the latest regulations, improved risk management through continuous monitoring, streamlined operations by automating compliance tasks, and flexibility to adapt to changing regulations as your business grows; essentially allowing businesses to outsource compliance management to a third-party provider with specialized expertise, freeing up internal resources to focus on core operations.
Advanced CaaS Technology Features:
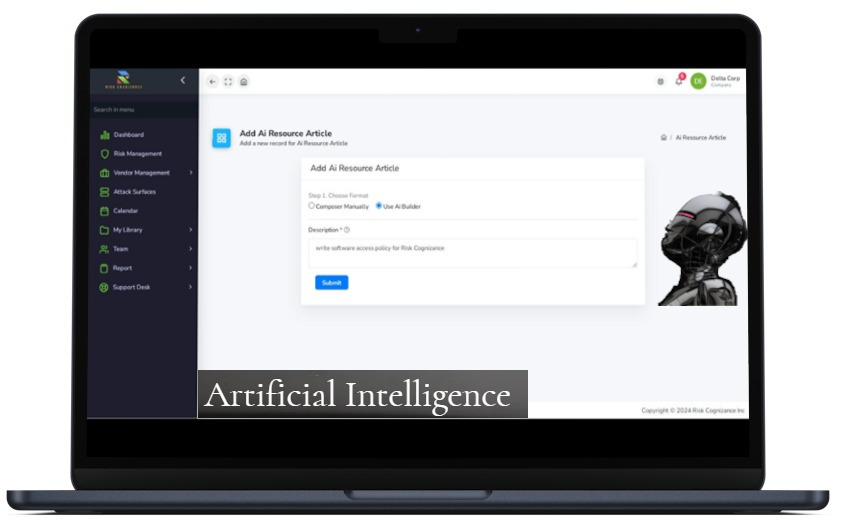
- AI-powered risk assessment automation
- Real-time compliance monitoring dashboards
- Enterprise-grade policy management systems
- Automated incident response workflows
- Third-party vendor risk assessment tools
Key Advantages of vCISO and Compliance Software
- Cost-Effective Security Leadership: Save 70-86% compared to traditional CISO hiring costs
- Enhanced Threat Protection: Implement enterprise-grade security controls and monitoring
- Automated Compliance Management: Streamline regulatory requirements across multiple frameworks
- Strategic Security Planning: Develop data-driven cybersecurity roadmaps
- Flexible Security Solutions: Scale security operations with business growth
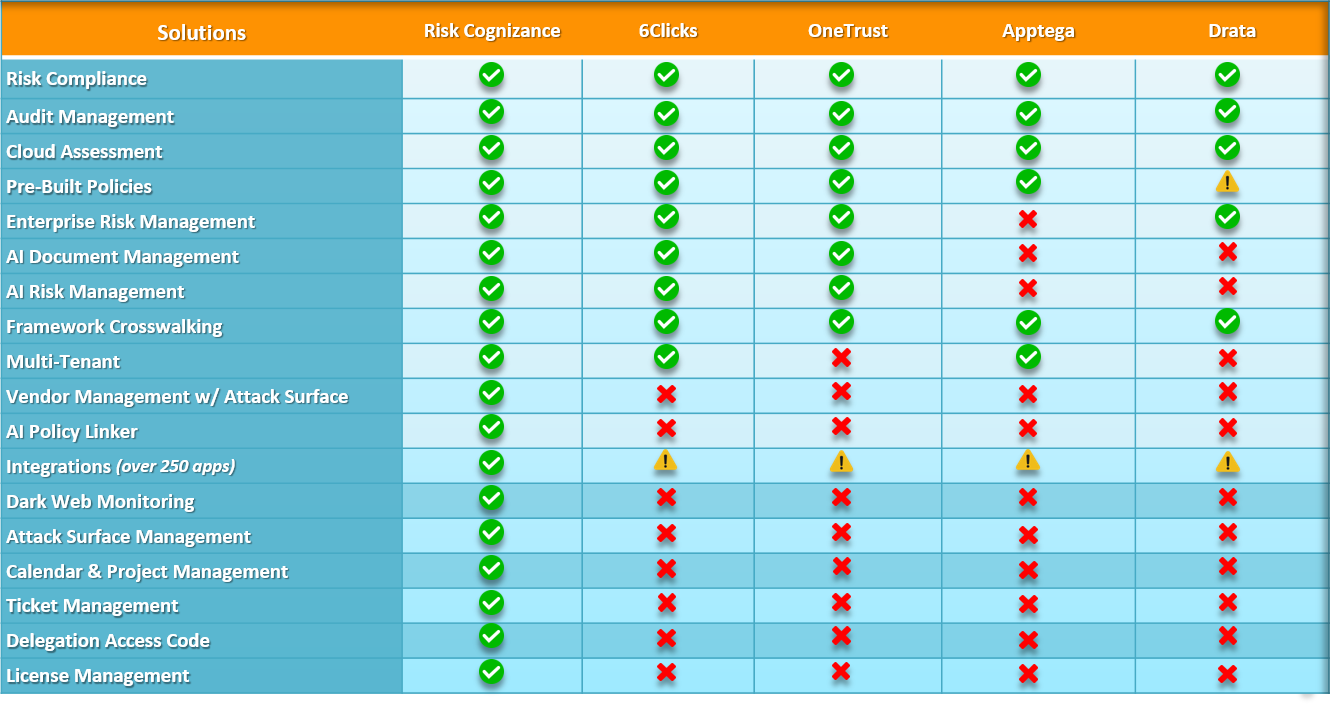
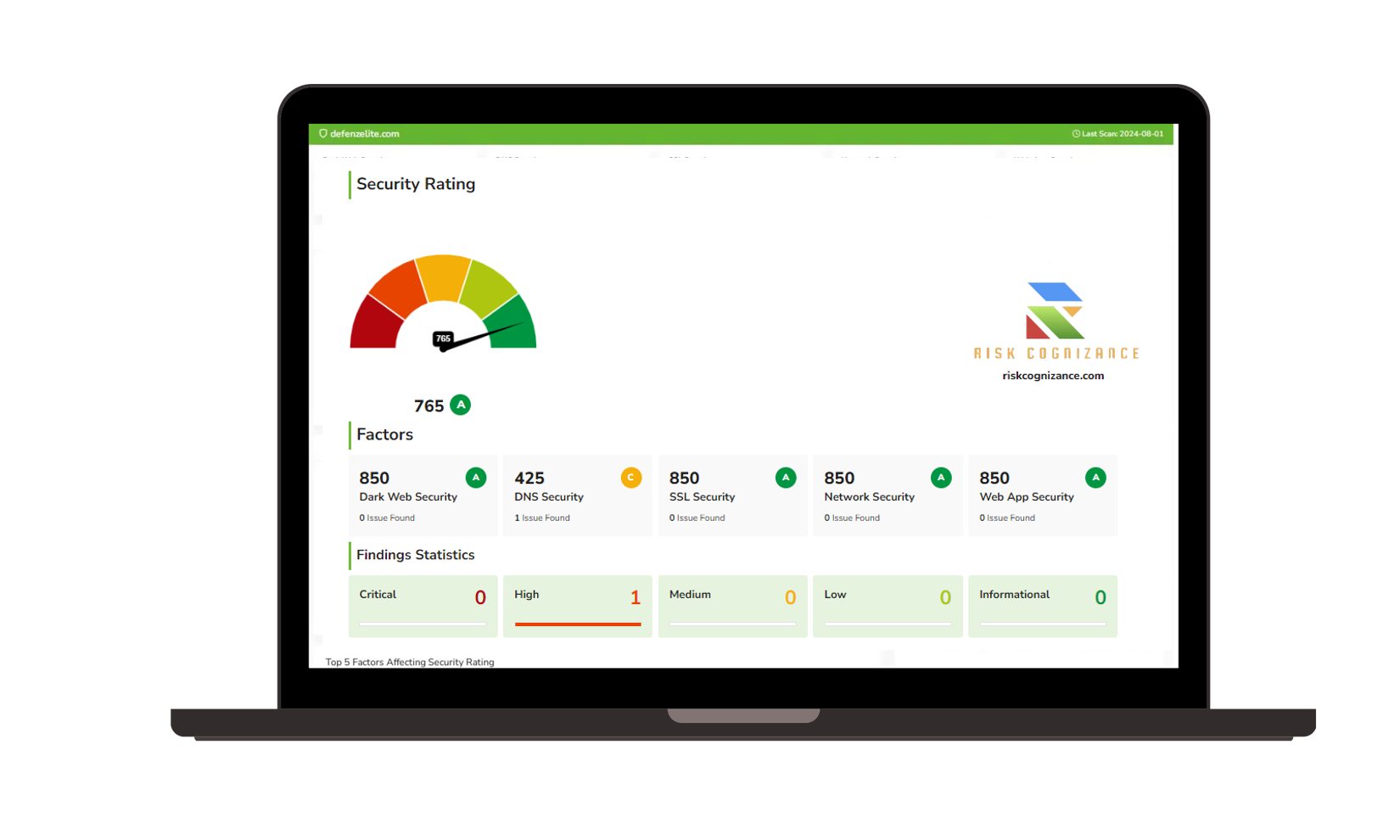
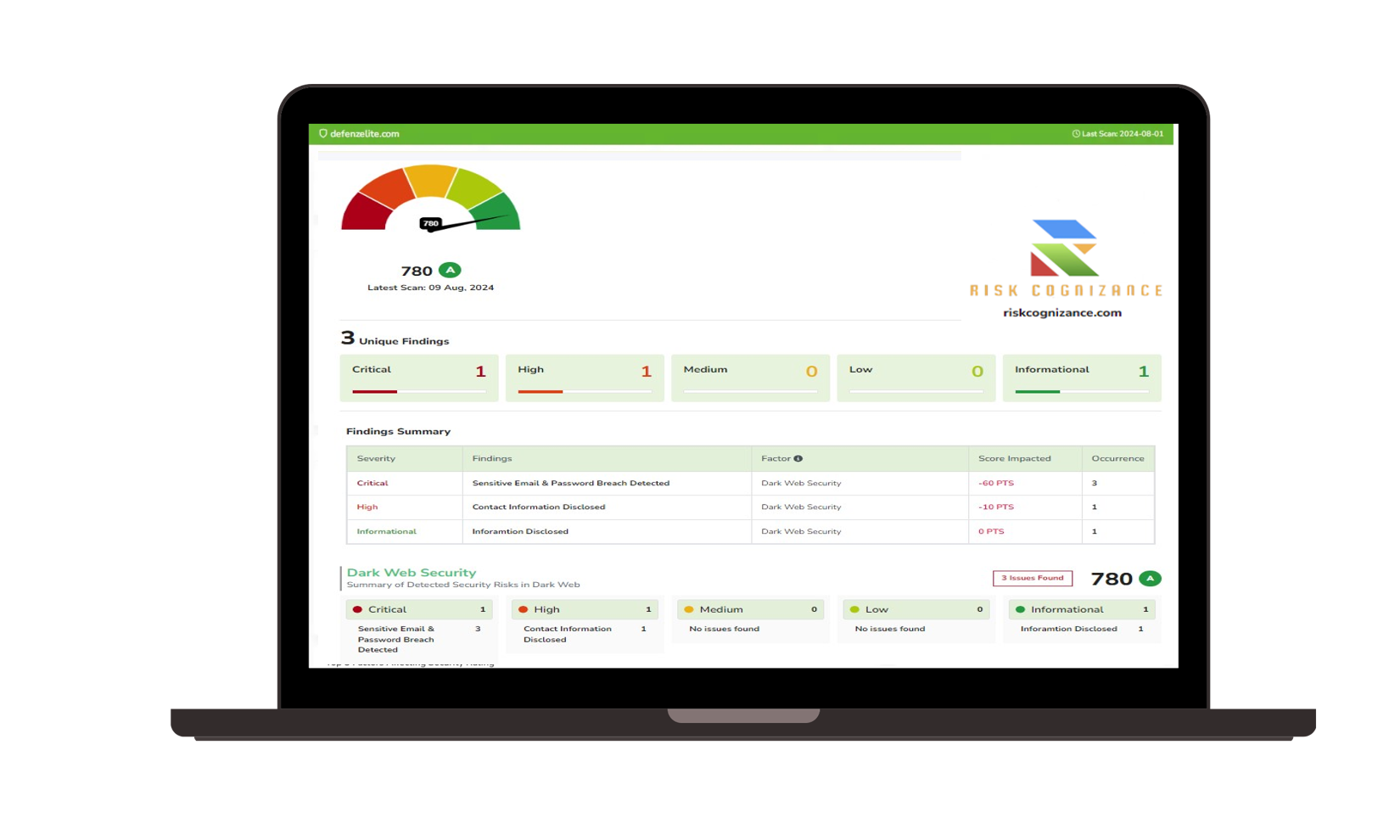
Enterprise Security Features and Tools
Compliance as a Service (CaaS) minimizes risk exposure by integrating a robust compliance layer into existing IT security systems, utilizing cloud-based automation to streamline the compliance process and alleviate the operational workload for businesses.
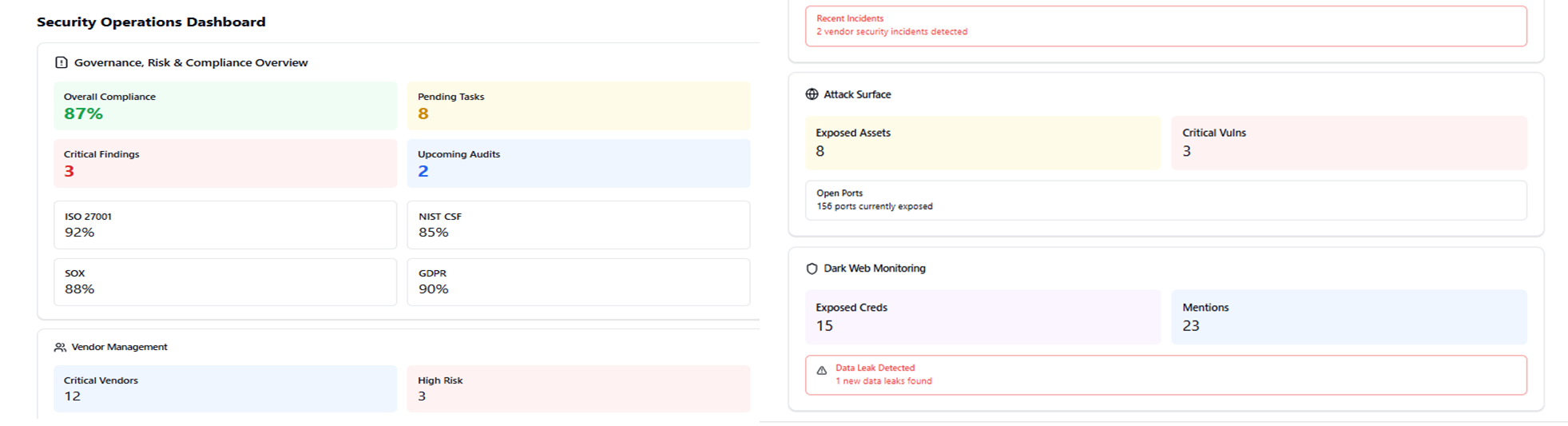
Advanced Risk Management Platform:
- Continuous vulnerability assessment engines
- Risk scoring and prioritization matrices
- Automated remediation tracking systems
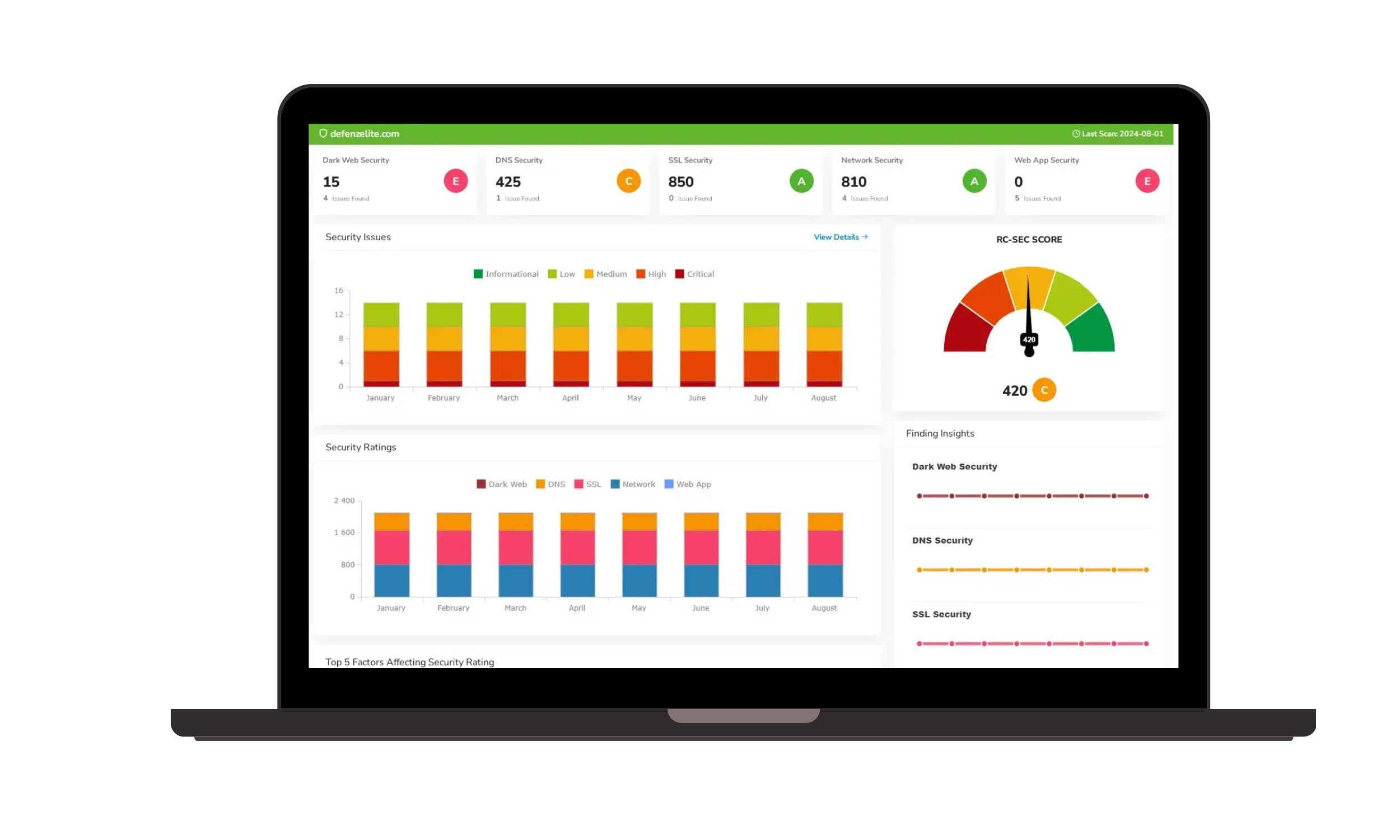
Enterprise Compliance Dashboard:
- Multi-framework compliance monitoring
- Automated compliance reporting tools
- Custom KPI tracking capabilities
Security Policy Management System:
- Customizable policy templates
- Automated version control
- Enterprise-wide policy distribution
Incident Response Management:
- Customizable response playbooks
- Automated workflow management
- Integrated communication systems
Vendor Security Management:
- Third-party risk assessment platform
- Continuous security monitoring
- API-driven integration capabilities
How to Choose the Right vCISO Solution
To choose the right vCISO solution, consider factors like your organization's specific security needs, the provider's expertise in your industry, their ability to tailor services to your size, their communication style, cost structure, and the level of access and support provided, ensuring they can effectively assess your current security posture and develop a comprehensive strategy aligned with your business goals.
Essential Selection Criteria:
- Industry-specific cybersecurity expertise
- Enterprise security platform capabilities
- System integration flexibility
- 24/7 security support availability
- Seamless implementation process
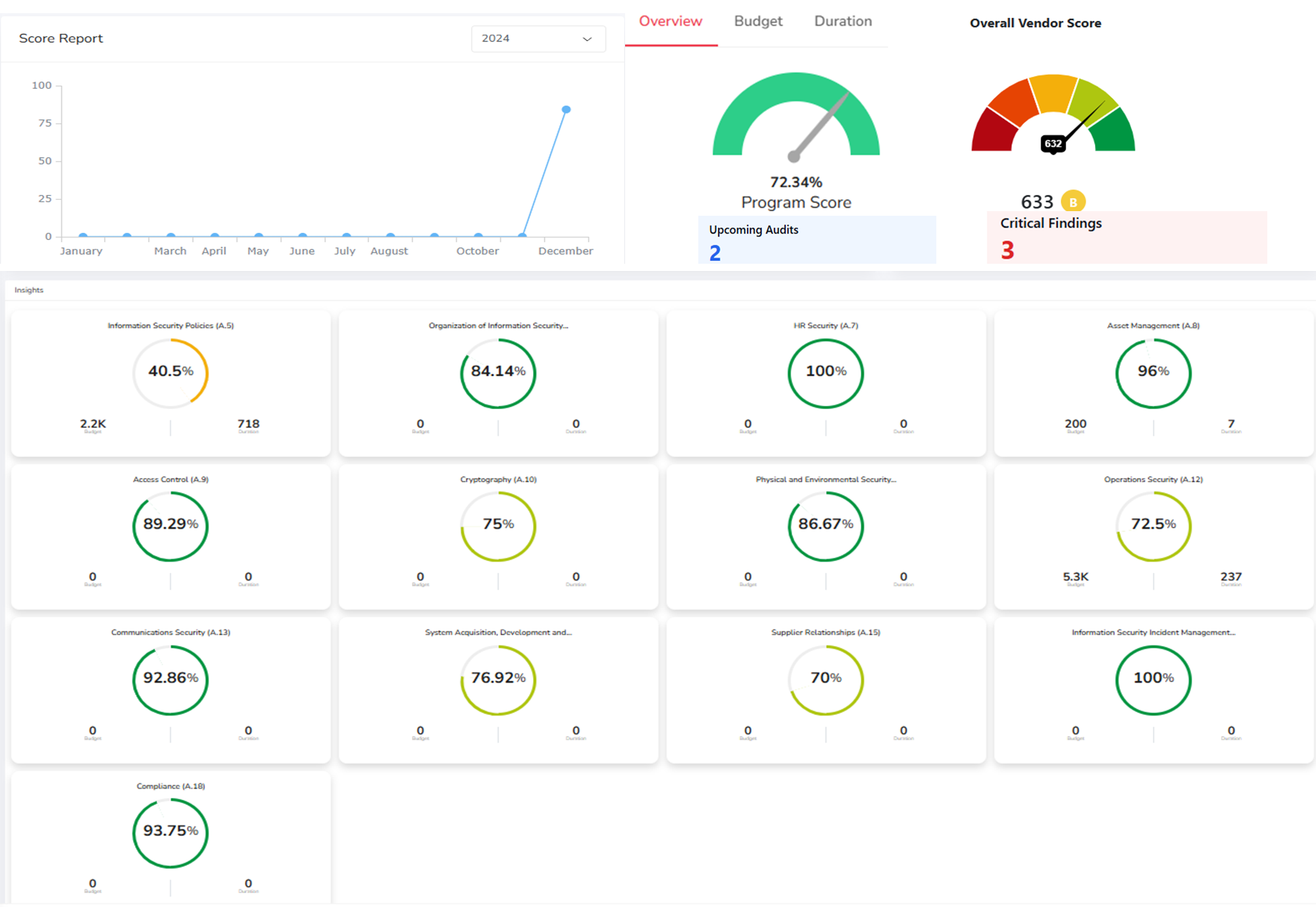
Measuring Security Program Success
Key Performance Indicators:
- Quantifiable security posture improvements
- Streamlined compliance processes
- Demonstrated cost savings and ROI
- Scalable security operations
- Responsive technical support metrics
Risk Management Software for vCISO service to scale while ensuring that cybersecurity measures remain effective. We offer precise risk measurement, automated compliance, and streamlined management.
Request Callback
