Overview
Risk Cognizance is a powerful GRC (Governance, Risk, and Compliance) software designed to help organizations effectively manage and mitigate risks. With its comprehensive suite of features, Risk Cognizance empowers security professionals to identify, assess, prioritize, and address risks across their entire organization.
Managing risk is essential for protecting your organization's assets, reputation, and bottom line. Risk Cognizance provides a centralized platform for managing all aspects of your GRC program, from risk assessment and mitigation to compliance management and incident response.
By leveraging advanced analytics and automation, Risk Cognizance enables you to:
- Identify and assess risks: Accurately identify and assess risks across your organization, including cyber threats, operational hazards, and regulatory non-compliance.
- Prioritize and mitigate risks: Prioritize risks based on their likelihood and impact, and develop effective mitigation strategies to address them.
- Ensure compliance: Streamline compliance efforts and reduce audit risk by automating compliance tasks and tracking regulatory changes.
- Improve decision-making: Make data-driven decisions based on real-time risk intelligence and insights.
- Enhance security posture: Protect your organization from cyber threats and data breaches with robust security controls and threat detection capabilities.
Risk Cognizance is designed to meet the needs of organizations of all sizes and industries. Whether you're a small business or a large enterprise, Risk Cognizance can help you improve your risk management program and achieve your business objectives.
 Governance, Risk, and Compliance (GRC) | 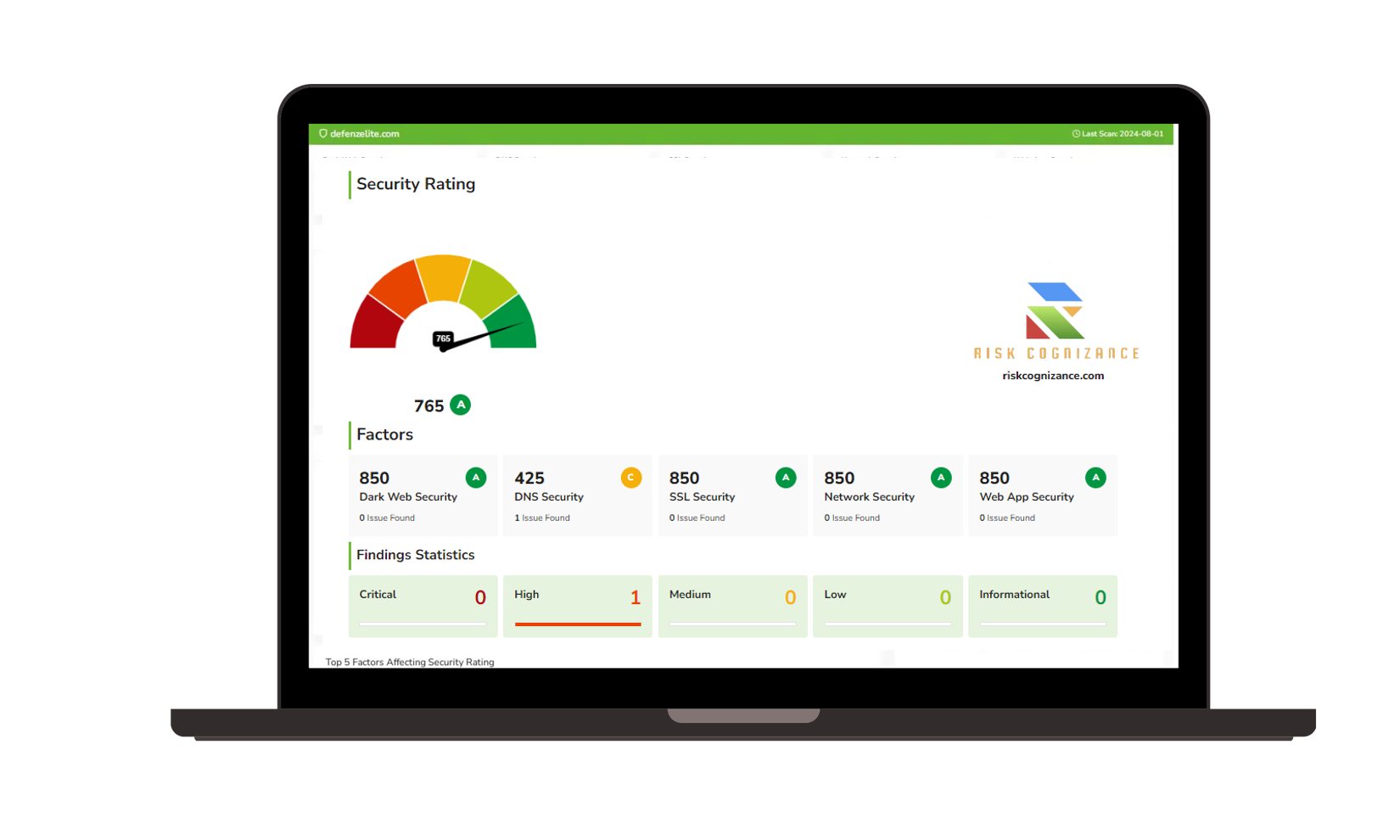 Third-party Risk Management |
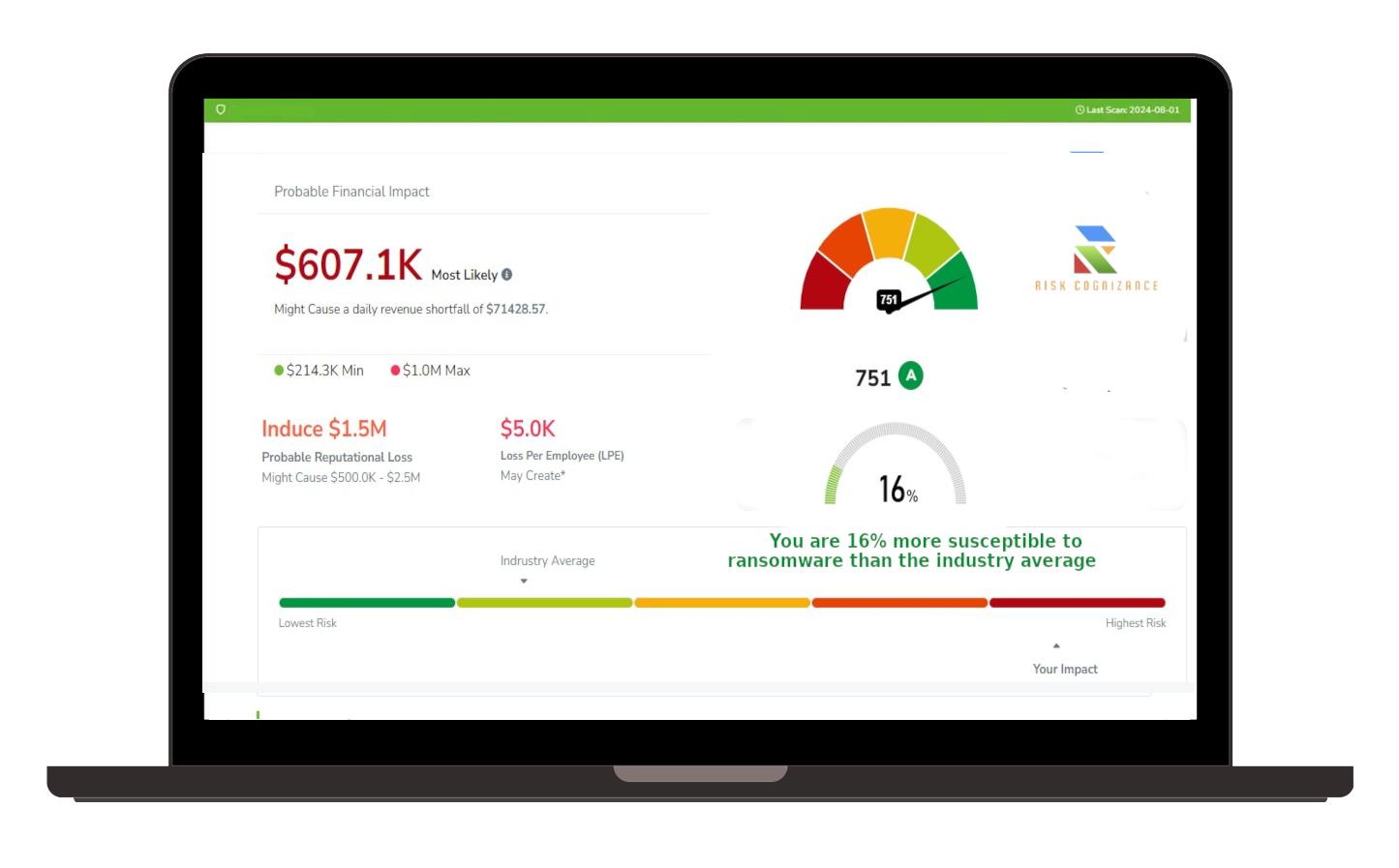 Ransomware Susceptibility | 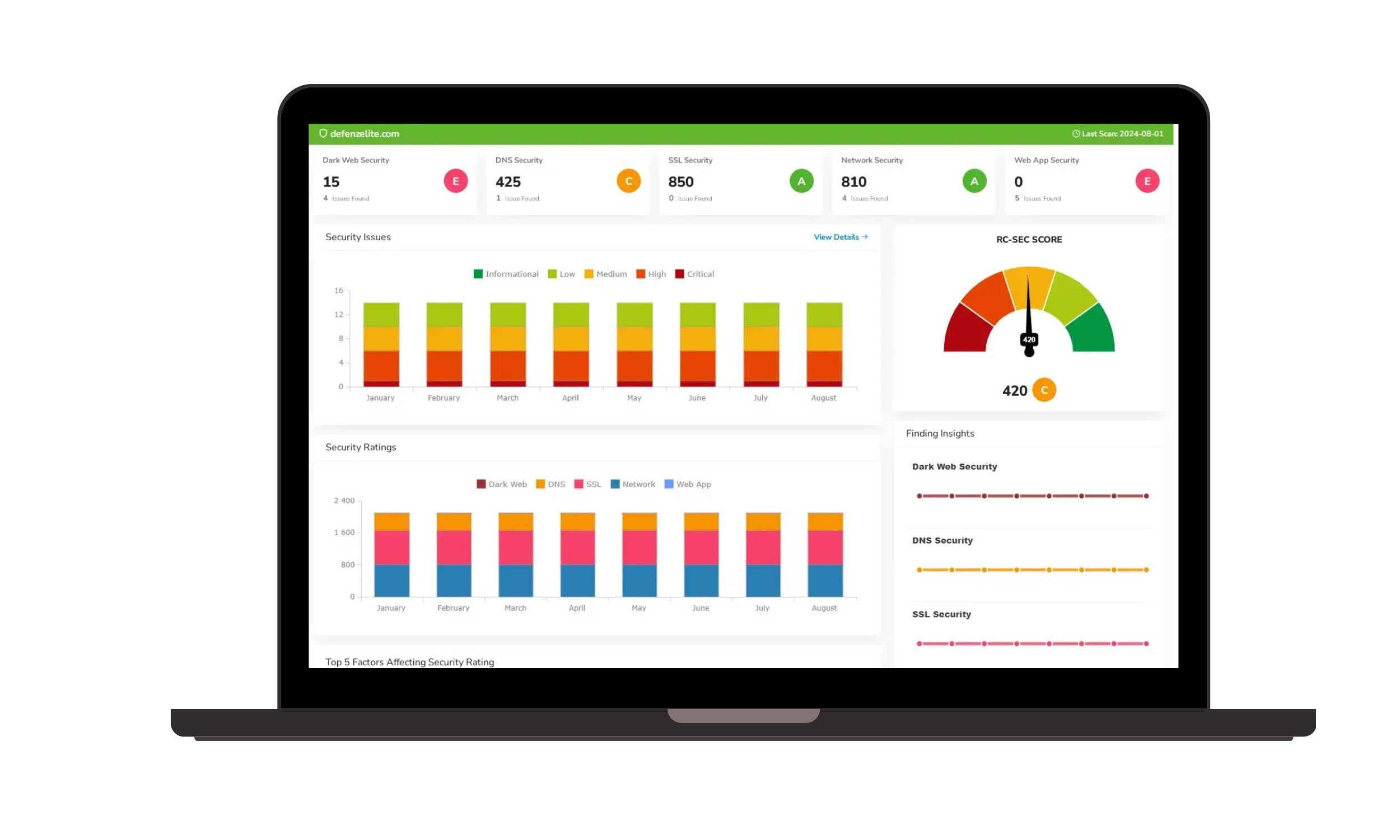 GRC and Attack Surface |
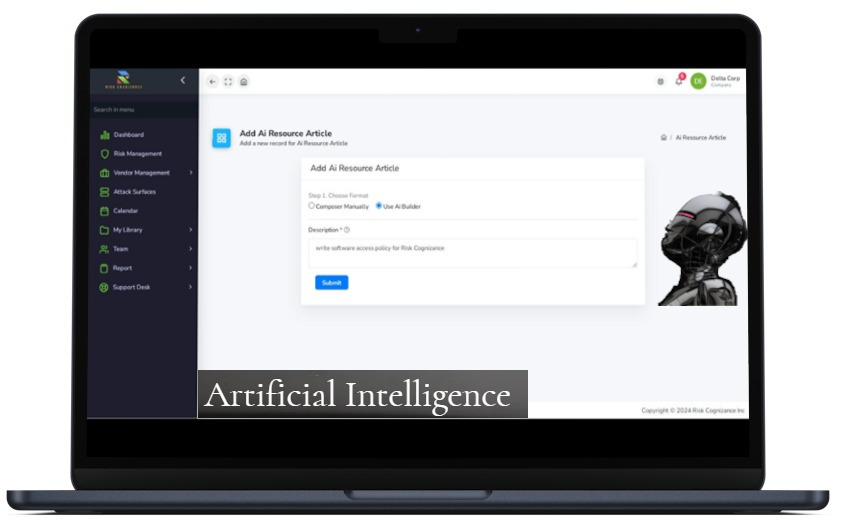
Artificial Intelligence | |
Key Features
Risk Management
- Comprehensive risk assessment and identification: Our software enables you to systematically identify and assess a wide range of risks, from cyber threats to operational hazards.
- Prioritization and mitigation strategies: Once risks are identified, Risk Cognizance helps you prioritize them based on their likelihood and impact, allowing you to focus on the most critical issues. Our platform also provides recommendations for effective mitigation strategies.
- Real-time risk monitoring and reporting: Stay informed about your organization's risk profile with real-time monitoring and reporting capabilities. Our software continuously scans for new threats and provides timely alerts, ensuring you can respond promptly to emerging risks.
Risk Assessment
- Customizable assessment frameworks: Tailor your risk assessment process to your organization's specific needs and industry requirements. Choose from pre-built frameworks or create your own custom templates.
- Vulnerability scanning and penetration testing: Identify vulnerabilities in your systems and networks through automated vulnerability scanning and simulated attacks. Our software helps you uncover potential weaknesses before they can be exploited.
- Impact and likelihood analysis: Quantify the potential impact and likelihood of each risk to make informed decisions about resource allocation and mitigation efforts.
Cybersecurity Assessment
- Continuous monitoring of security posture: Gain a comprehensive view of your organization's security posture with continuous monitoring capabilities. Our software tracks a wide range of security metrics, including vulnerability status, threat detection, and compliance adherence.
- Detection and response to threats: Detect and respond to cyber threats in real time with our advanced threat detection and response capabilities. Our software leverages machine learning and artificial intelligence to identify suspicious activity and trigger automated response actions.
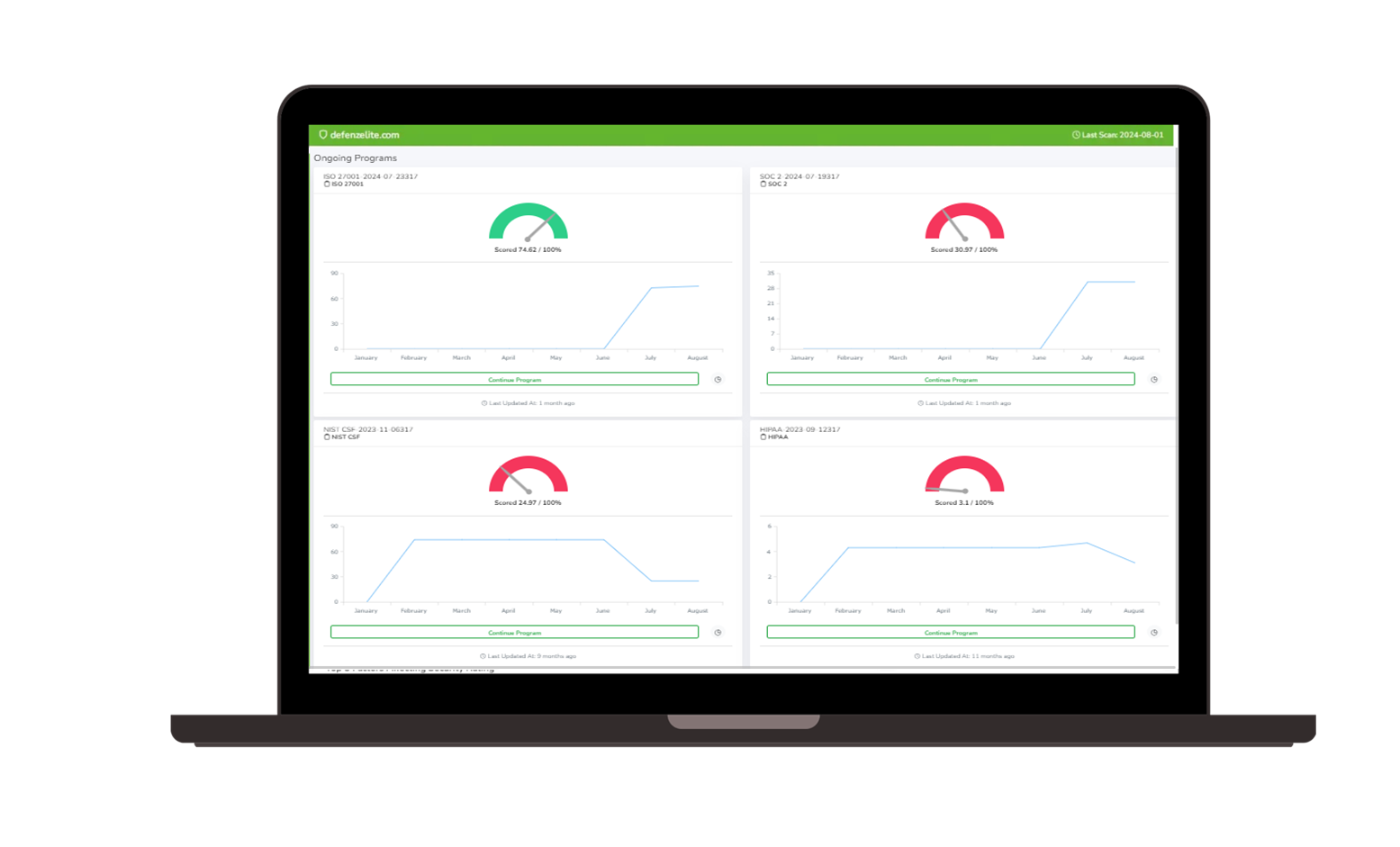
- Compliance with industry standards (e.g., NIST, ISO 27001): Ensure compliance with industry-recognized security standards and regulations. Our software provides built-in templates and guidance to help you meet the requirements of standards like NIST and ISO 27001.
Threat Intelligence
- Access to up-to-date threat feeds: Stay informed about the latest cyber threats with access to real-time threat intelligence feeds. Our software provides insights into emerging threats, vulnerabilities, and attack trends.
- Identification of emerging risks: Proactively identify potential risks by analyzing threat intelligence data. Our software helps you stay ahead of emerging threats and take preventive measures.
- Proactive threat prevention: Use threat intelligence to inform your security strategy and implement proactive measures to prevent attacks. Our software provides recommendations for security controls and best practices based on the latest threat intelligence.
Ransomware Attacks Reporting
- Streamlined incident response processes: Respond effectively to ransomware attacks with our streamlined incident response processes. Our software provides step-by-step guidance and automation to help you contain the attack and minimize damage.
- Compliance with regulatory requirements: Ensure compliance with relevant regulations and standards related to ransomware attacks. Our software provides templates and guidance for documenting incident response activities and reporting requirements.
- Recovery planning and testing: Develop and test your organization's recovery plan to minimize downtime and disruption in the event of a ransomware attack. Our software helps you create and maintain a comprehensive recovery plan.
Vendor Management
- Third-party risk assessment: Assess the risks posed by third-party vendors and suppliers. Our software provides tools for evaluating vendor security practices, contract terms, and compliance status.
- Contract management and compliance: Manage vendor contracts and ensure compliance with contractual obligations. Our software helps you track contract expiration dates, enforce SLAs, and monitor vendor performance.
- Supplier performance monitoring: Monitor the performance of your vendors and suppliers to identify and address any issues. Our software provides tools for tracking vendor performance metrics and conducting regular reviews.
Data Protection
- Data classification and sensitivity labeling: Classify and label data based on its sensitivity and value. Our software helps you implement appropriate security controls and access restrictions based on data sensitivity.
- Access controls and encryption: Implement robust access controls and encryption to protect sensitive data. Our software provides tools for managing user access, enforcing access policies, and encrypting data at rest and in transit.
- Data breach response and notification: Develop a data breach response plan and notify affected individuals and authorities in accordance with applicable regulations. Our software provides templates and guidance for data breach response and notification.
Compliance Management
- Automation of compliance tasks: Streamline compliance efforts with automated compliance tasks. Our software can help you track compliance requirements, collect evidence, and generate reports.
- Evidence collection and audit support: Collect and organize evidence to support compliance audits. Our software provides tools for storing and managing audit evidence.
- Tracking of regulatory changes: Stay up-to-date with regulatory changes that impact your organization. Our software provides alerts and notifications about new regulations and updates.
Understanding Risk Management
- Educational resources and training materials: Access educational resources and training materials to help your team understand risk management concepts and best practices. Our software includes training modules and documentation to support your team's development.
- Best practices and industry benchmarks: Learn from industry best practices and benchmarks to improve your risk management program. Our software provides insights into industry trends and best practices.