Overview
Navigate the FTC Safeguards Rule with Confidence Using Risk Cognizance
The Federal Trade Commission (FTC) Safeguards Rule requires financial institutions to implement robust safeguards to protect customer information. Risk Cognizance offers a comprehensive solution to help organizations comply with these regulations, ensuring that your security practices meet federal standards while enhancing your overall data protection strategies.
 Governance, Risk, and Compliance (GRC) | 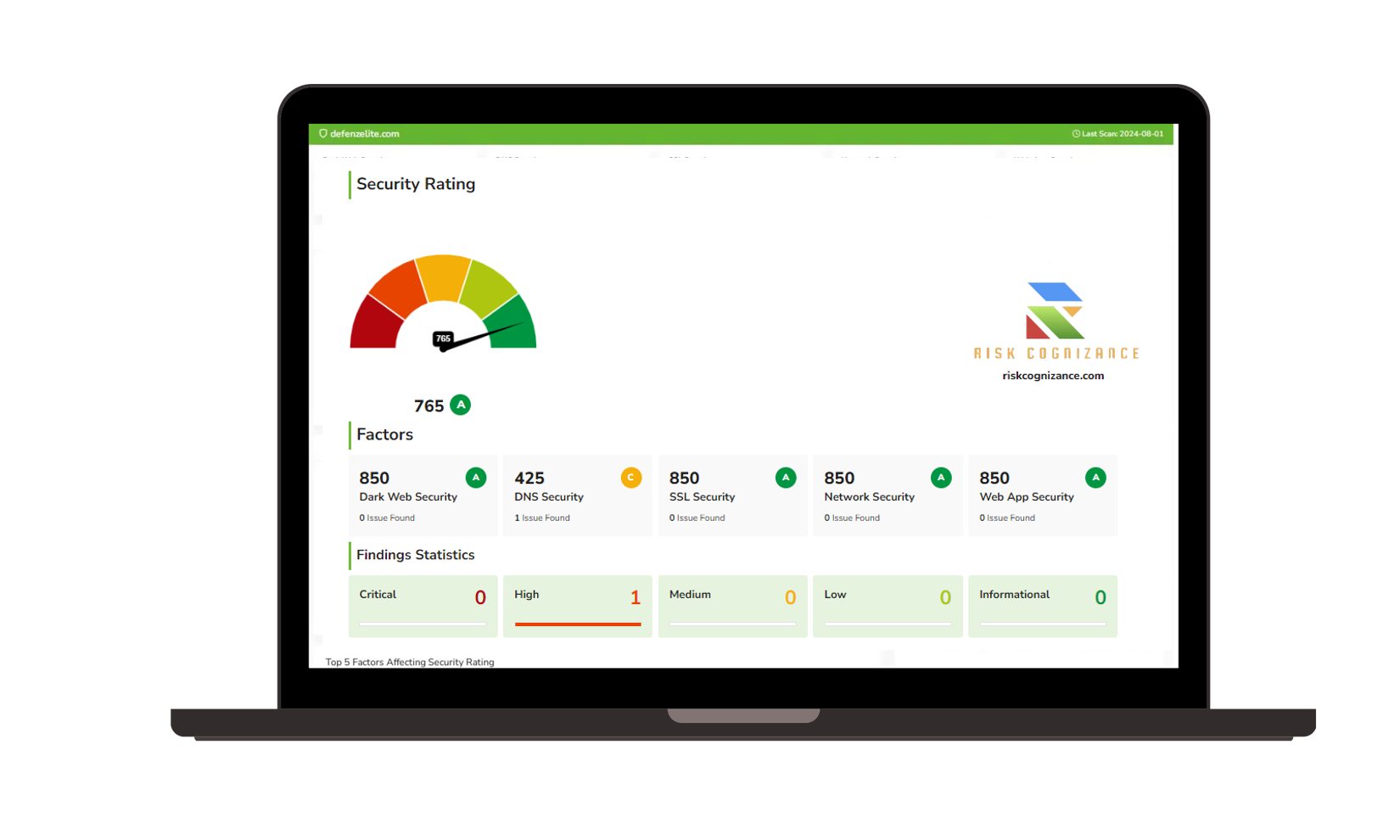 Third-party Risk Management |
 Ransomware Susceptibility | 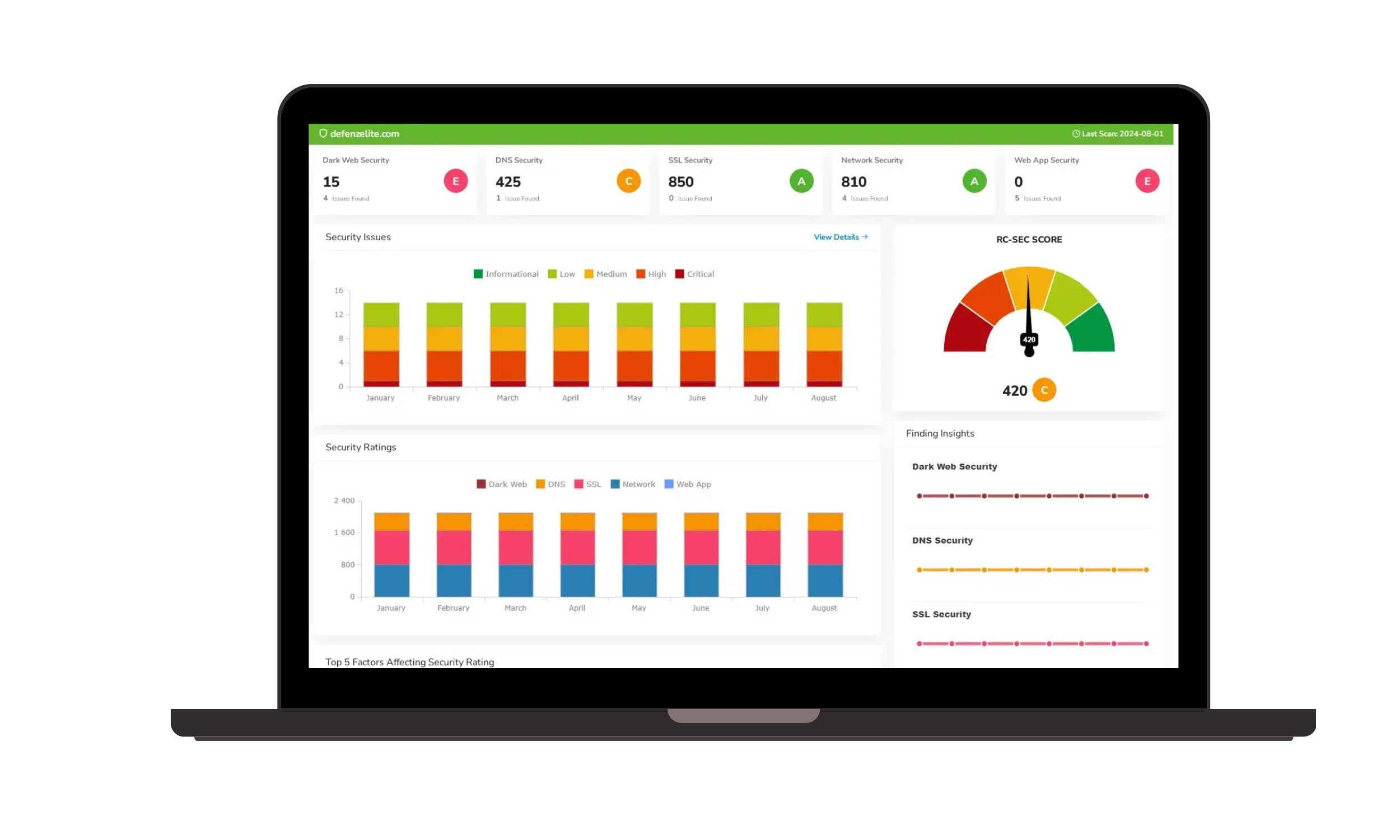 GRC and Attack Surface |
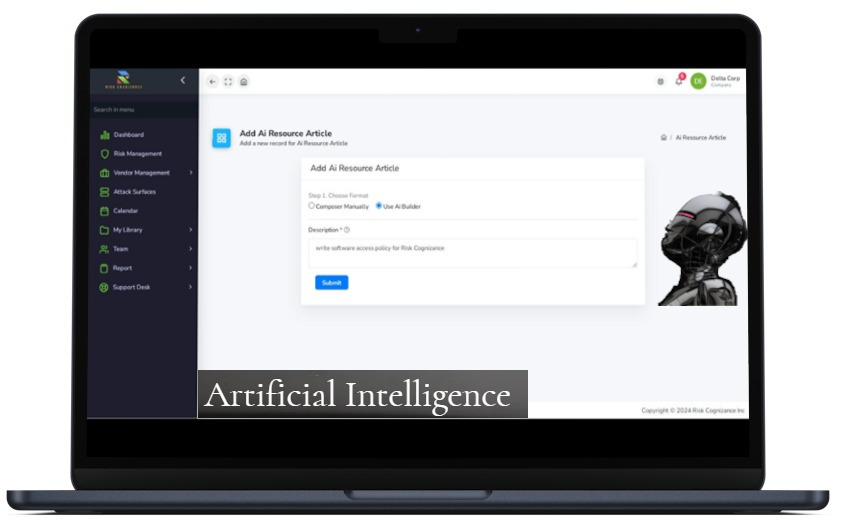
Artificial Intelligence | |
Why Risk Cognizance for FTC Safeguards Rule Compliance?
Risk Cognizance provides an advanced platform designed to meet the specific requirements of the FTC Safeguards Rule. Our solution ensures that your organization adheres to regulatory mandates efficiently while strengthening your data protection measures. Here’s how our platform supports FTC Safeguards Rule compliance:
1. Comprehensive Compliance Management:
- Regulatory Adherence: Ensure compliance with all aspects of the FTC Safeguards Rule, including risk assessments, information security programs, and employee training.
- Policy Development: Develop and manage information security policies and procedures that align with FTC requirements.
- Audit Preparation: Streamline the audit process with tools for documentation, tracking, and issue resolution.
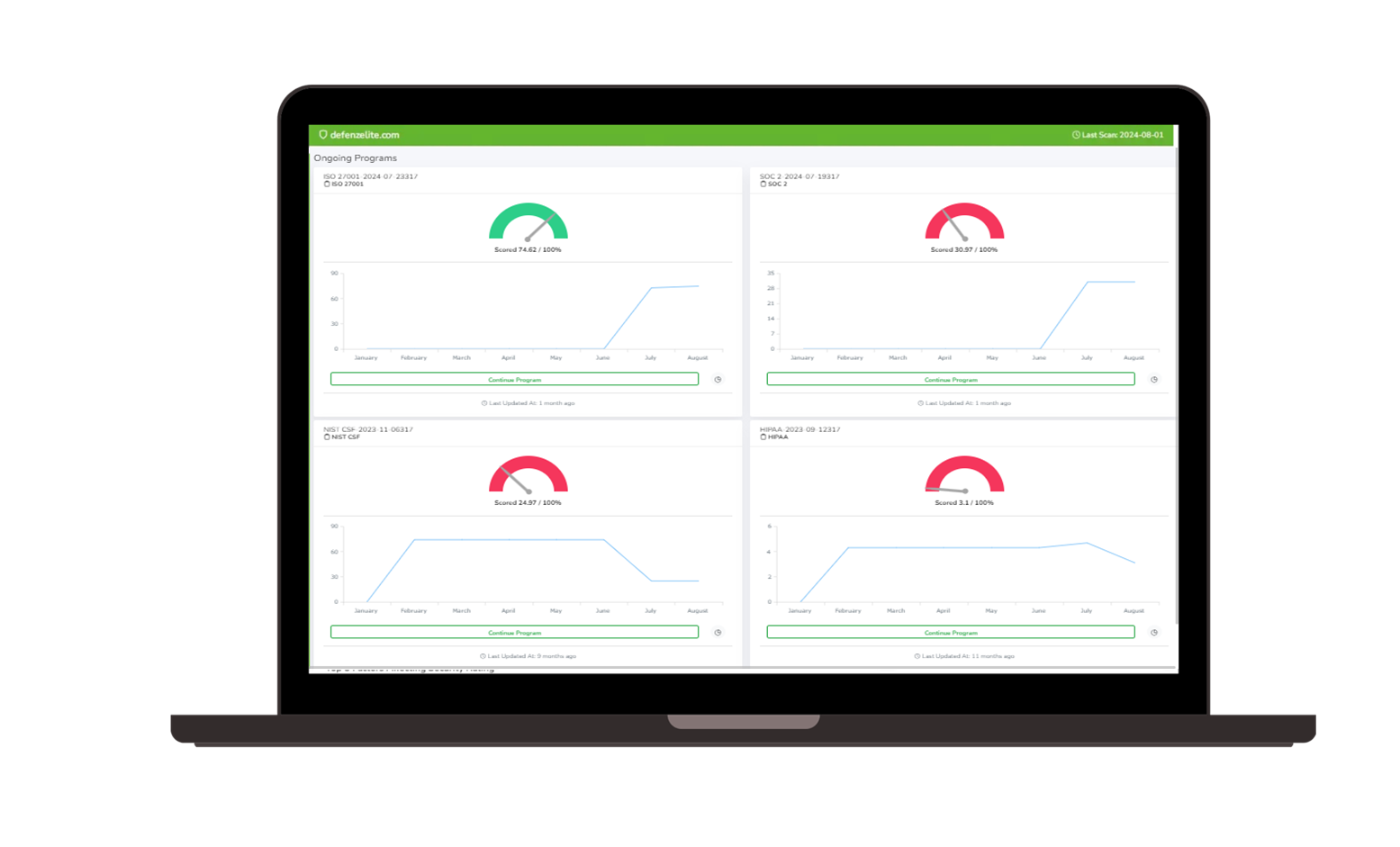
2. Advanced Risk Assessment and Management:
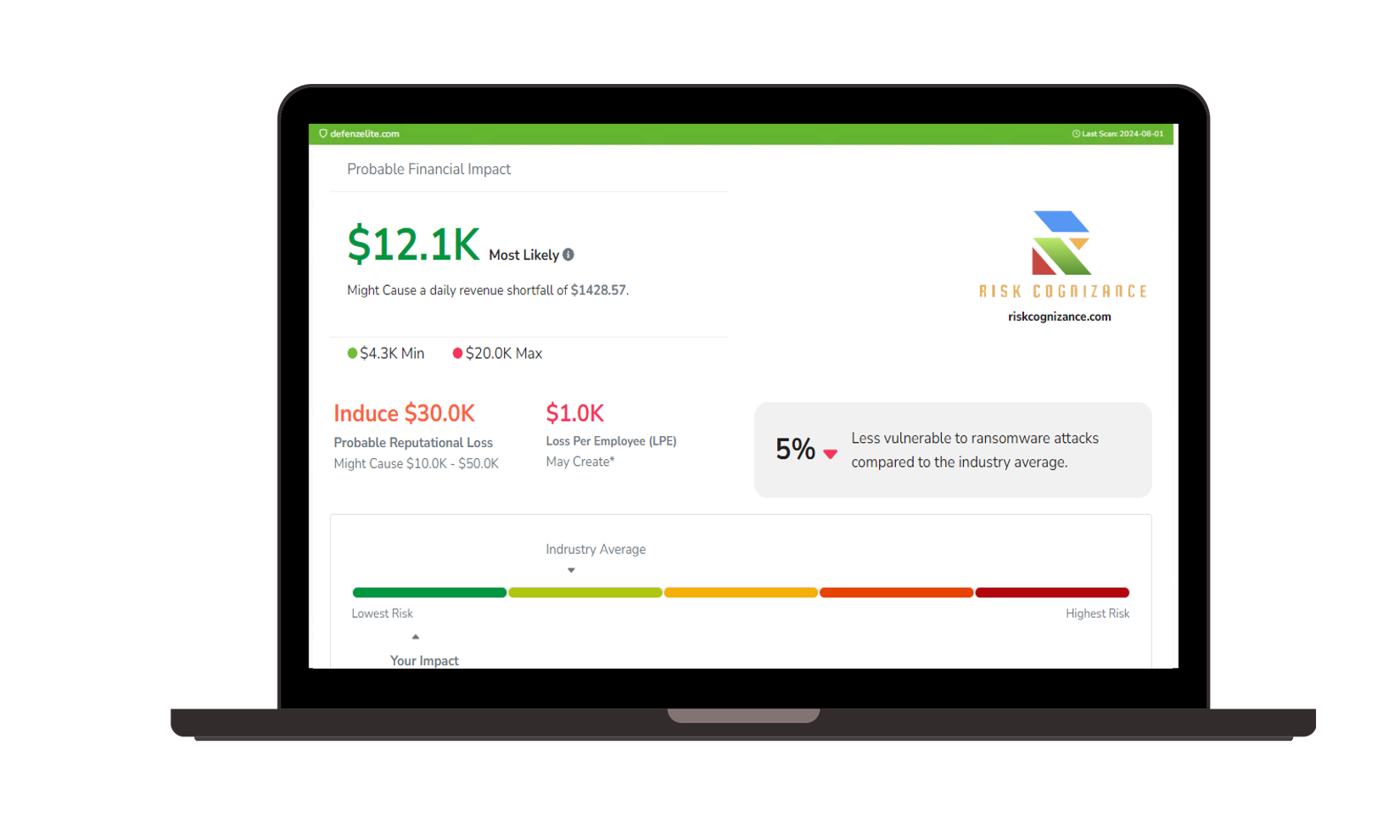
- Risk Identification: Conduct detailed risk assessments to identify potential threats and vulnerabilities impacting your organization.
- Control Implementation: Implement and manage cybersecurity controls to mitigate identified risks and meet FTC standards.
- Continuous Monitoring: Monitor risk indicators in real-time to detect and address potential issues proactively.
3. Automated Compliance Reporting:
- Customizable Reports: Generate detailed, customizable compliance reports to demonstrate adherence to the FTC Safeguards Rule.
- Regulatory Documentation: Maintain and manage all necessary documentation for FTC audits and inspections.
- Automated Alerts: Receive alerts and notifications related to compliance status and regulatory updates.
4. Incident Management and Response:
- Incident Response Plan: Develop and implement a comprehensive incident response plan in accordance with FTC requirements.
- Incident Tracking: Track and manage cybersecurity incidents from detection through resolution.
- Post-Incident Review: Conduct thorough post-incident reviews to evaluate response effectiveness and enhance future practices.
5. Data Protection and Privacy:
- Data Encryption: Ensure robust data encryption and protection to safeguard sensitive customer information.
- Access Controls: Implement role-based access controls to secure critical data and systems.
- Privacy Compliance: Adhere to data privacy regulations and ensure that personal and financial information is handled securely.
6. Security Program Oversight:
- Program Management: Oversee and manage your organization’s information security program to ensure ongoing compliance and effectiveness.
- Control Optimization: Optimize security controls and practices based on real-time data and regulatory updates.
- Continuous Improvement: Benefit from continuous platform updates and improvements to stay ahead of evolving cybersecurity threats.
7. User Education and Training:
- Training Programs: Conduct regular training sessions on information security best practices and regulatory requirements for employees.
- Awareness Campaigns: Implement awareness campaigns to educate staff on recognizing and responding to potential security threats.
8. Integration and Scalability:
- Seamless Integration: Integrate Risk Cognizance with your existing security infrastructure and financial management systems.
- Scalable Solution: Adapt the platform to fit the needs of organizations of all sizes, from small businesses to large enterprises.
- Flexible Deployment: Choose from on-premises, cloud-based, or hybrid deployment options to suit your organization’s infrastructure.
9. Advanced Analytics and Reporting:
- Real-Time Analytics: Utilize advanced analytics to gain actionable insights into your cybersecurity posture and compliance status.
- Interactive Dashboards: Access interactive dashboards for a comprehensive view of compliance metrics, risk indicators, and security performance.
10. Dedicated Support and Updates:
- Customer Support: Access dedicated customer support for assistance with implementation, training, and ongoing usage.
- Regular Updates: Stay up-to-date with the latest cybersecurity standards and regulatory requirements through continuous platform updates.
Ensure Compliance with the FTC Safeguards Rule
When evaluating solutions for FTC Safeguards Rule compliance, organizations consider factors such as:
- Regulatory Adherence: Ensuring the solution meets all specific requirements of the FTC Safeguards Rule.
- Risk Management Capabilities: Assessing the effectiveness of risk assessment, control implementation, and incident management features.
- Reporting and Documentation: Evaluating the ability to generate detailed compliance reports and manage regulatory documentation.
- Support and Updates: Considering the quality of customer support and the frequency of platform updates.
Explore how Risk Cognizance can help your organization navigate the complexities of the FTC Safeguards Rule with confidence. Our platform offers comprehensive solutions to ensure compliance while enhancing your data protection strategies.
Ready to achieve FTC Safeguards Rule compliance? Contact Risk Cognizance today to discover how our advanced cybersecurity solutions can support your regulatory needs and protect your organization from emerging threats.
Request Callback