Overview
External Attack Surface Management and Cyber Risk Assessment: Proactively Secure Your Digital Environment
As cyber threats become increasingly sophisticated, organizations face growing challenges in safeguarding their digital assets. External Attack Surface Management (ASM) and Cyber Risk Assessment are crucial for businesses to understand, identify, and mitigate vulnerabilities before attackers can exploit them. Risk Cognizance offers cutting-edge tools for continuous external attack surface monitoring, in-depth risk assessments, and actionable insights, enabling businesses to proactively defend their infrastructure and enhance their cybersecurity posture.
Understanding External Attack Surface Management (ASM)
Your organization's external attack surface constantly evolves as new digital assets, applications, and third-party services are integrated. External Attack Surface Management involves continuously identifying, monitoring, and securing every asset within your digital ecosystem, from internet-facing endpoints to cloud services, IoT devices, and third-party vendors.
- Continuous Monitoring: ASM provides a continuous, real-time view of your organization's external assets, ensuring you’re aware of every component that could be exploited by attackers.
- Dynamic Mapping: Regular updates to your attack surface map reflect the constant evolution of your infrastructure.
The Importance of Cyber Risk Assessment
Cyber risk assessment is crucial for identifying, evaluating, and mitigating potential risks to your organization’s systems, data, and assets. Risk Cognizance's tools allow businesses to conduct comprehensive assessments, understand their vulnerabilities, and implement targeted security measures.
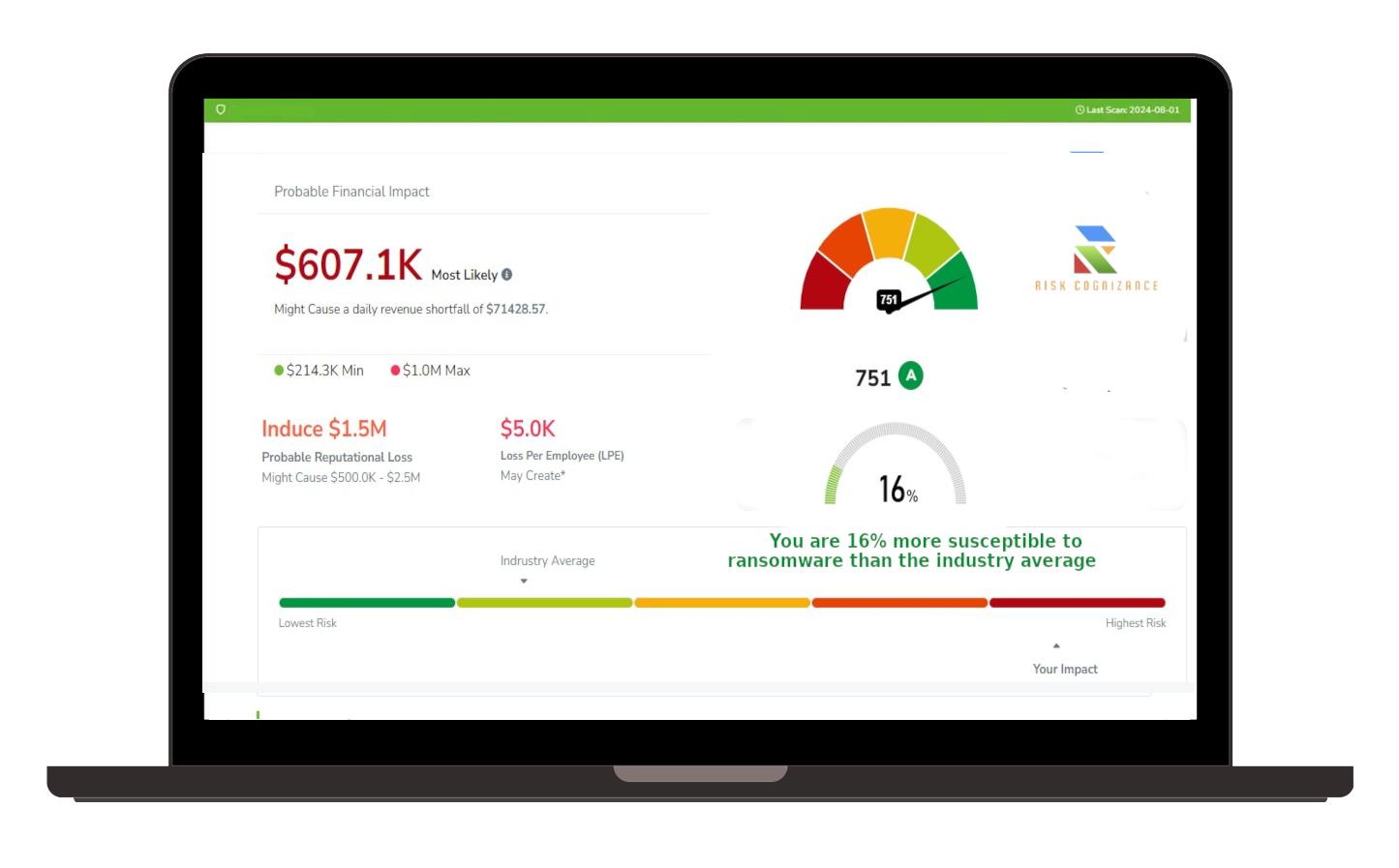
- Prioritized Risk Mitigation: By continuously assessing risks, organizations can prioritize remediation efforts based on their business-critical needs.
- Risk Modeling: Simulating potential attack scenarios helps evaluate the impact and severity of various threats.
 |  |
 |  |
 |  |
Key Benefits of Risk Cognizance Solutions
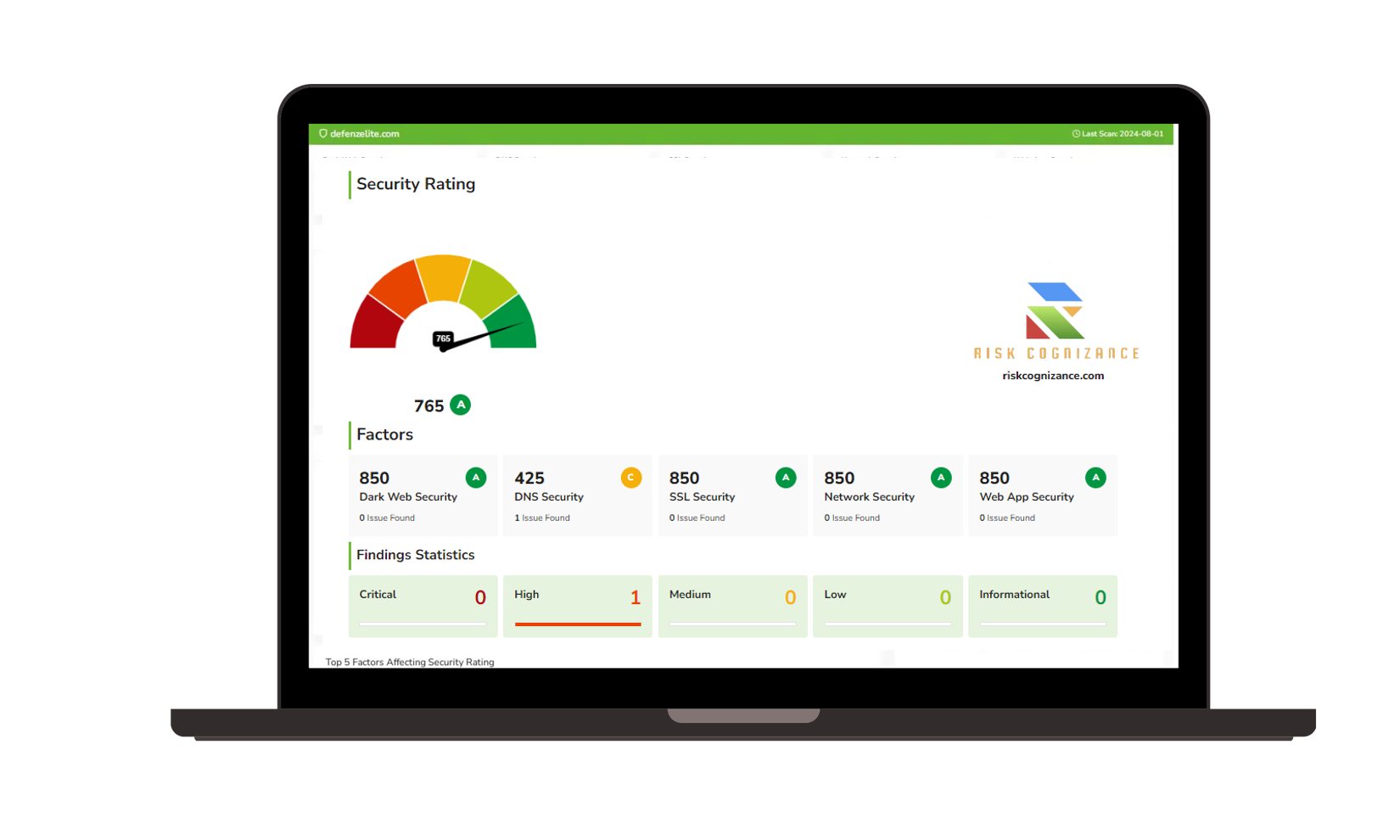
Continuous Visibility into Your External Attack Surface
- Automated Asset Discovery: Identify all digital assets across cloud services, endpoints, applications, and third-party vendors.
- Real-Time Risk Identification: Receive continuous updates and alerts on emerging risks.
- Dynamic Mapping: Keep an up-to-date, accurate external attack surface map.
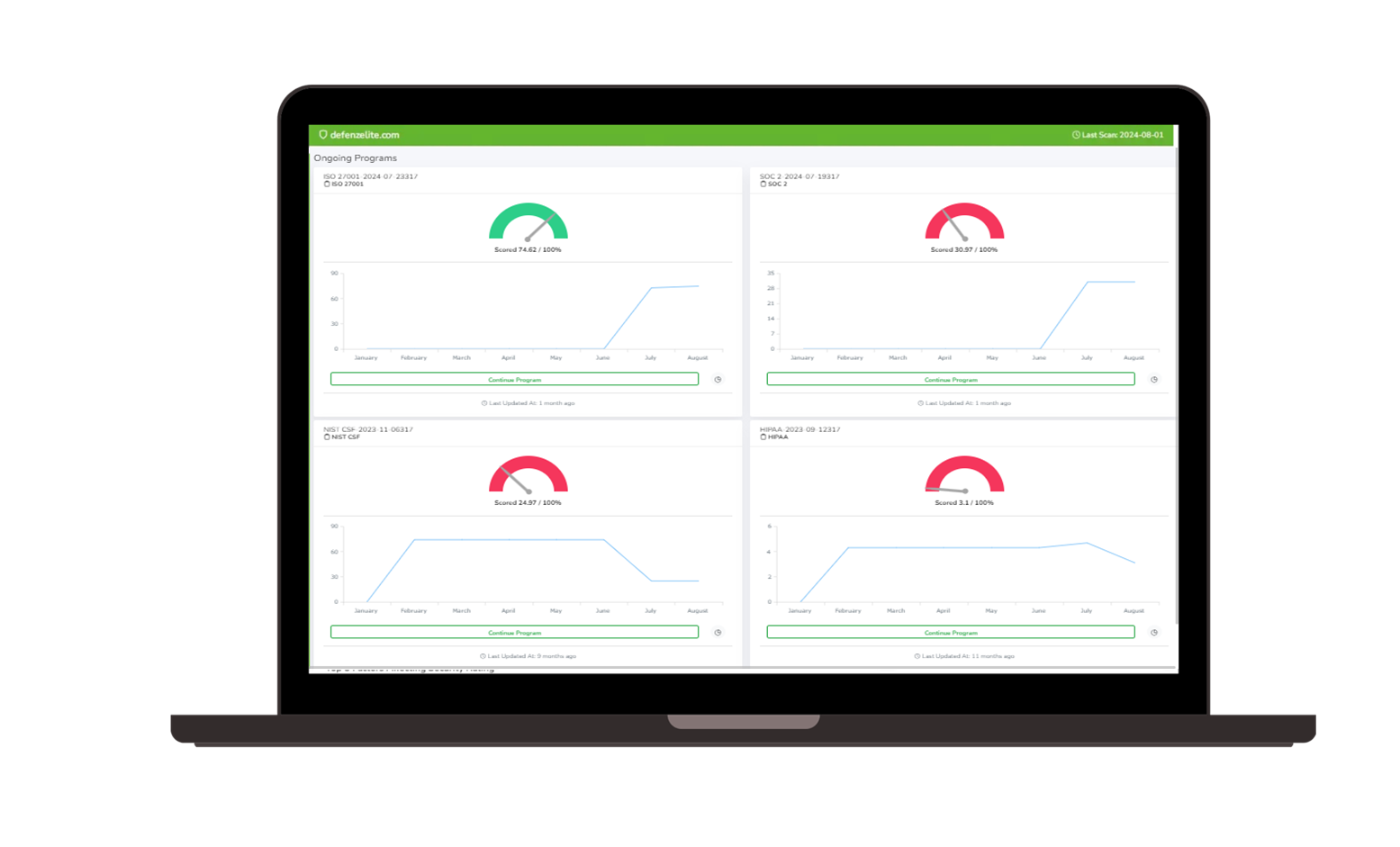
Proactive Cyber Risk Assessment
- Vulnerability Scanning and Analysis: Regular scans identify weaknesses in your environment.
- Risk Scoring: Rank risks based on their potential impact and likelihood.
- Scenario Modeling: Model real-world attack scenarios to understand vulnerabilities' potential impact.
Real-Time Threat Intelligence and Alerts
- Integrated Threat Intelligence: Stay updated on emerging threats with integrated intelligence feeds.
- Real-Time Alerts: Receive immediate notifications of vulnerabilities or risks detected across your environment.
- Automated Reports: Generate risk assessment reports for clear, actionable security insights.
Enhanced Vulnerability Management and Mitigation
- Automated Vulnerability Scanning: Regular scans uncover system weaknesses.
- Prioritization and Remediation: Prioritize vulnerabilities and receive actionable recommendations for patching or mitigating risks.
Third-Party Risk and External Threat Monitoring
- Third-Party Discovery: Identify and assess external vendor assets and integrations.
- Continuous Monitoring: Track risks associated with third-party relationships to prevent security gaps.
Explore Our External Attack Surface Management and Cyber Risk Assessment Technologies
External Attack Surface Discovery and Mapping
- Automated Asset Discovery: Continuously scan your digital ecosystem for assets.
- Real-Time Updates: Ensure your attack surface is always up-to-date as new assets are added or removed.
Cyber Risk Assessment Platform
- Vulnerability Scanning: Uncover system weaknesses before attackers exploit them.
- Risk Prioritization: Focus on addressing the most critical vulnerabilities.
- Scenario-Based Risk Modeling: Test how vulnerabilities could be exploited in real-world scenarios.
Governance, Risk, and Compliance (GRC) Software
- Ensure your organization adheres to regulatory standards while managing risk effectively.
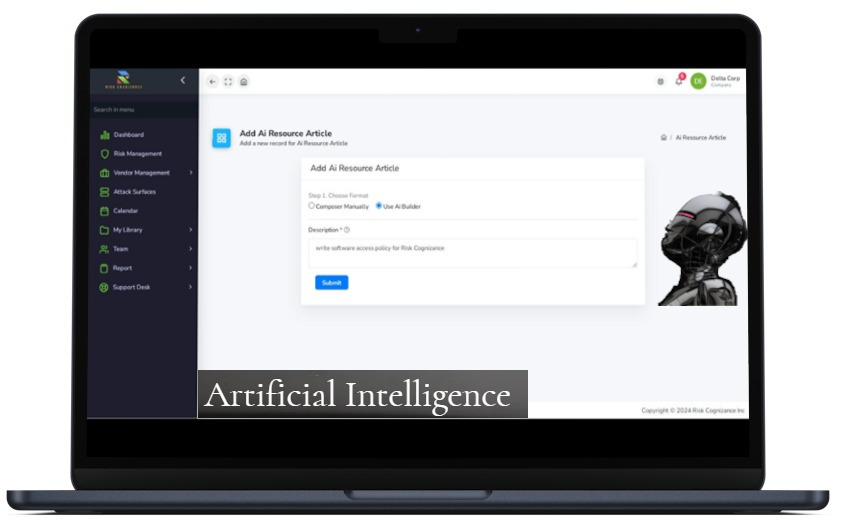
Artificial Intelligence and Threat Intelligence Integration
- Utilize AI to predict and assess potential risks based on emerging threat intelligence.
Our Solutions
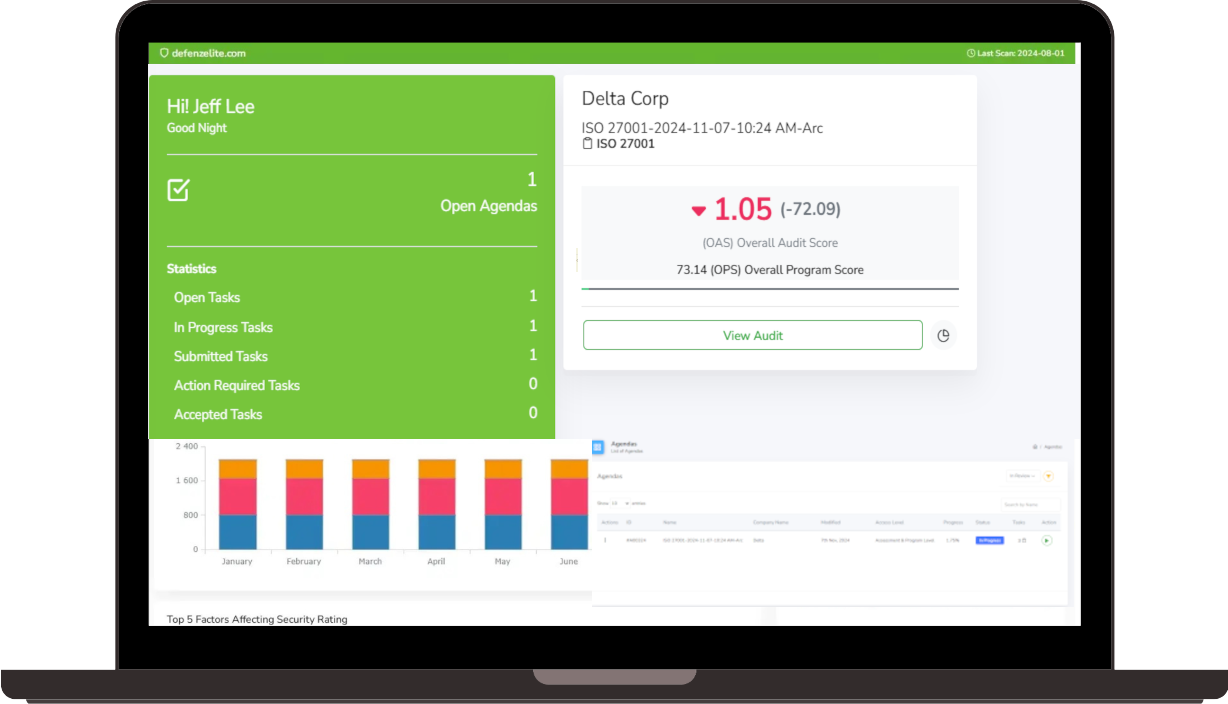
External Attack Surface Management Dashboard
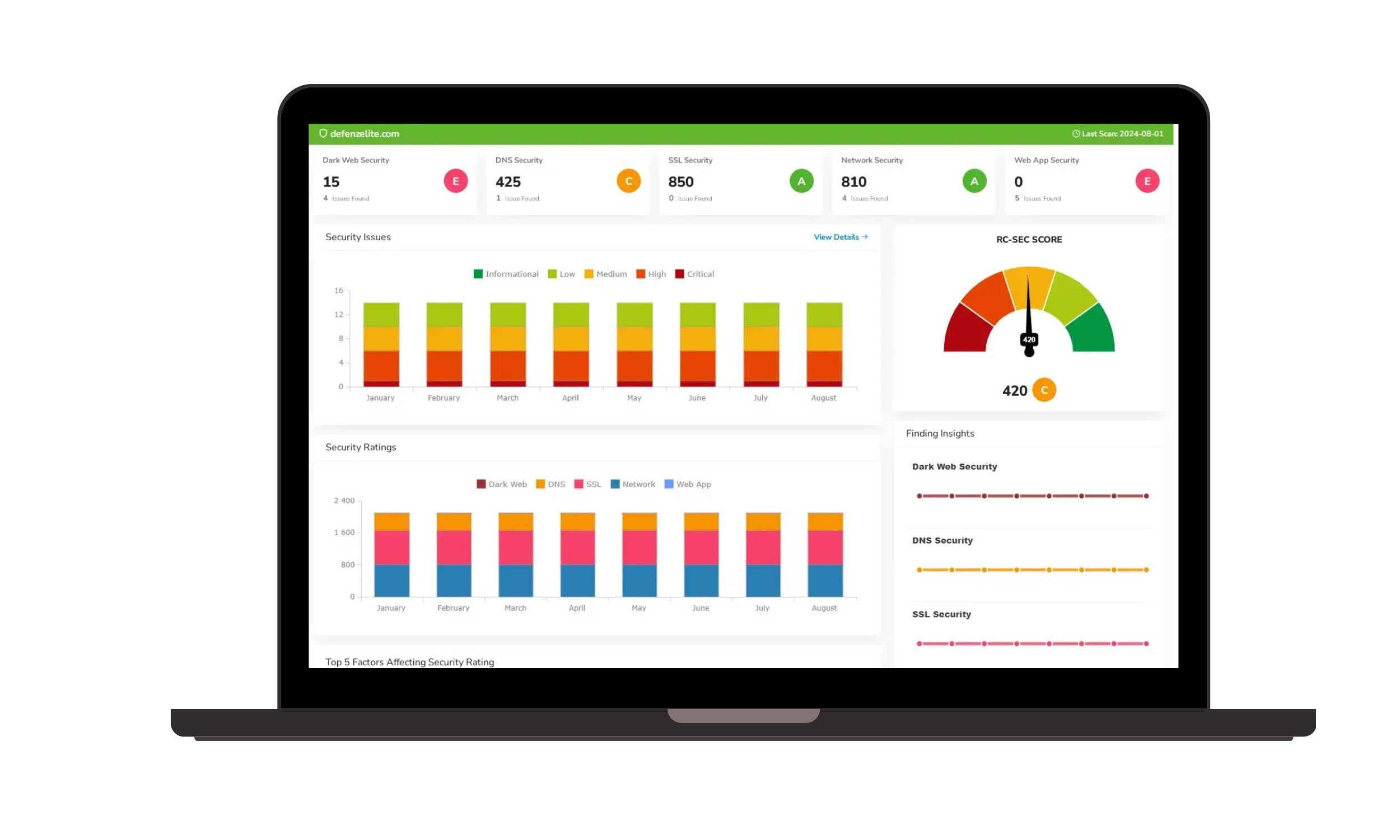
- Comprehensive Dashboards: Access a unified view of your external attack surface with actionable risk insights.
- Risk Analytics: Visualize trends, identify weak points, and gauge the potential impact of emerging threats.
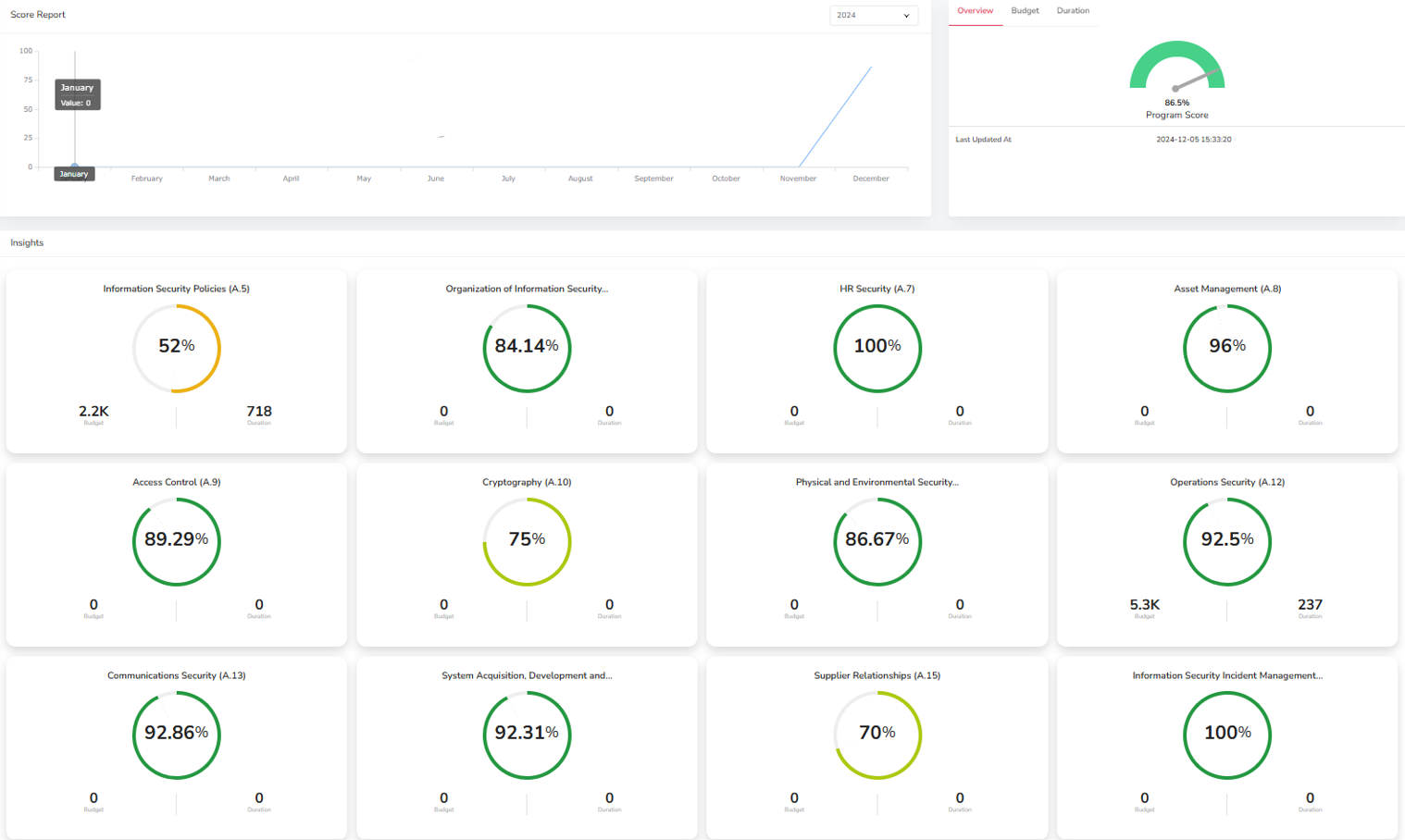
Cyber Risk Assessment Reports
- Automated Reporting: Generate detailed, automated risk reports to guide your security strategies.
- Compliance Reports: Ensure adherence to industry regulations, providing transparency to stakeholders.
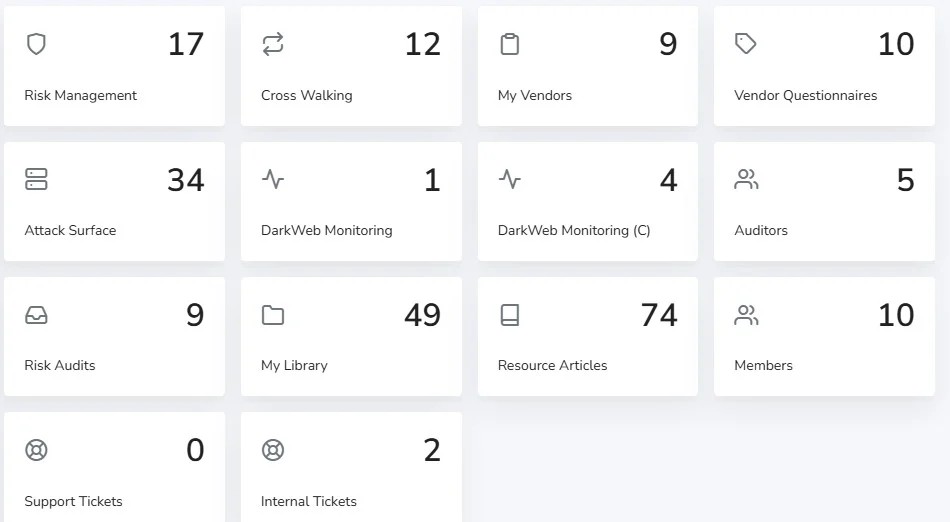
Third-Party and Supply Chain Risk Management
- Third-Party Monitoring: Continuously assess the security posture of your vendors and partners.
- Supply Chain Security: Identify and address potential risks within your supply chain, ensuring external relationships don't introduce vulnerabilities.
Risk Cognizance’s comprehensive External Attack Surface Management and Cyber Risk Assessment solutions empower organizations to stay ahead of evolving cyber threats. By providing continuous visibility, real-time alerts, and actionable insights, our platform ensures that businesses can proactively manage risks, protect critical assets, and strengthen their overall cybersecurity posture.
Request Callback
