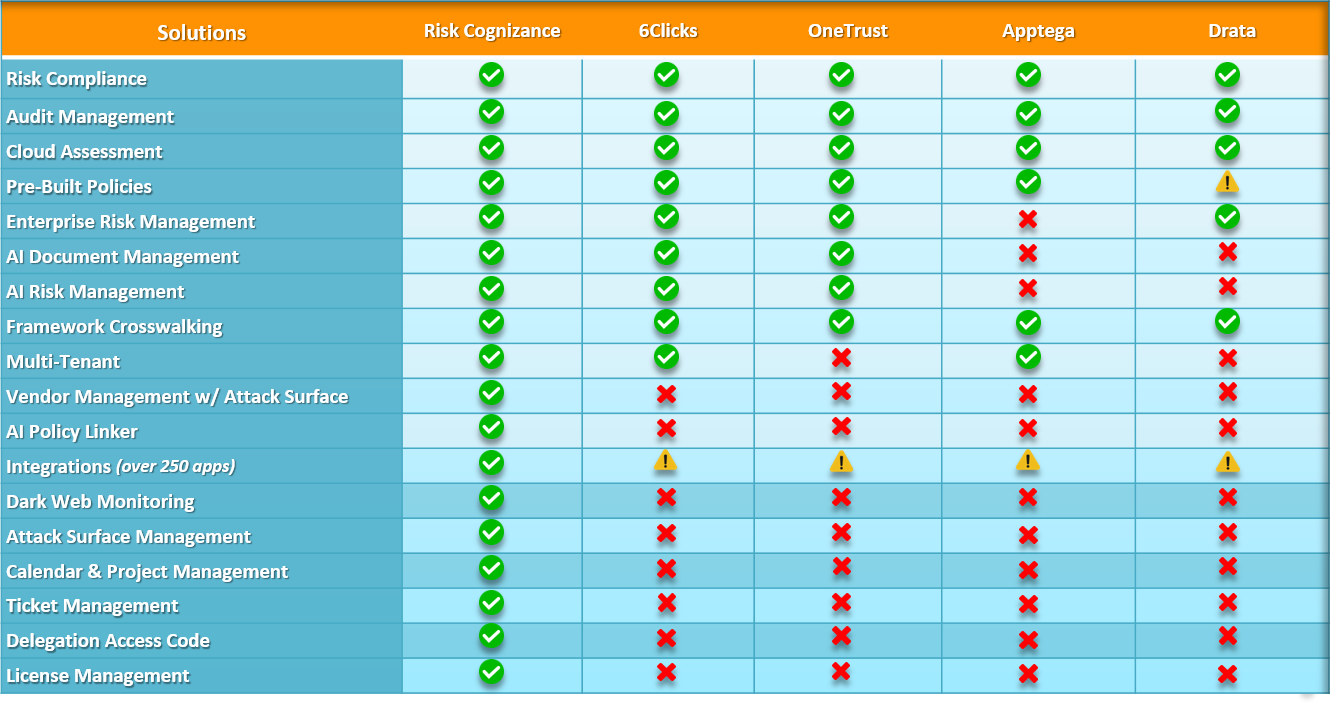
Overview
Protect Your Organization with Cutting-Edge Risk Monitoring Solutions
Businesses are under constant threat from cybercriminals, many of whom operate on the Deep and Dark Web. These hidden areas of the internet provide a sanctuary for illegal activities such as selling stolen data, illicit software, counterfeit goods, and hacking services. For businesses, this means that sensitive information—like employee credentials, intellectual property, and customer data—could be exposed, sold, or traded without your knowledge.
With Deep and Dark Web Monitoring for Business from Risk Cognizance, you gain a proactive defense against these risks. We provide continuous surveillance of online spaces that traditional search engines can’t reach, identifying threats before they become full-scale cyberattacks. Our monitoring solution helps you stay one step ahead, ensuring that your business and its sensitive data remain protected.

What is the Difference Between the Deep Web & Dark Web?
Understanding the difference between the Deep Web and the Dark Web is crucial for appreciating the risks that each presents to your business:
Deep Web:
The Deep Web consists of any content that is not indexed by standard search engines like Google or Bing. This includes password-protected content (such as email accounts, corporate intranets, and bank accounts), subscription-based content (like academic journals, medical records, and paywalled news articles), and encrypted communications (like private chats and financial transactions). While the Deep Web is not inherently dangerous, it houses a vast amount of sensitive, non-public information, much of which, if exposed, could present a significant risk to your business’s privacy, security, and reputation.
Example: Internal company documents stored in private cloud servers or secure emails.
Dark Web:
The Dark Web is a portion of the Deep Web that has been intentionally hidden and can only be accessed using special software like Tor (The Onion Router). The Dark Web is infamous for its use by criminals to conduct illegal activities such as selling stolen data, drugs, counterfeit goods, and weapons. Unlike the Deep Web, the Dark Web is intentionally anonymous and encrypted, making it a hub for illicit activities.
Example: Markets where hackers sell stolen credit card data, login credentials, or other personal information.
What is Deep & Dark Web Monitoring?
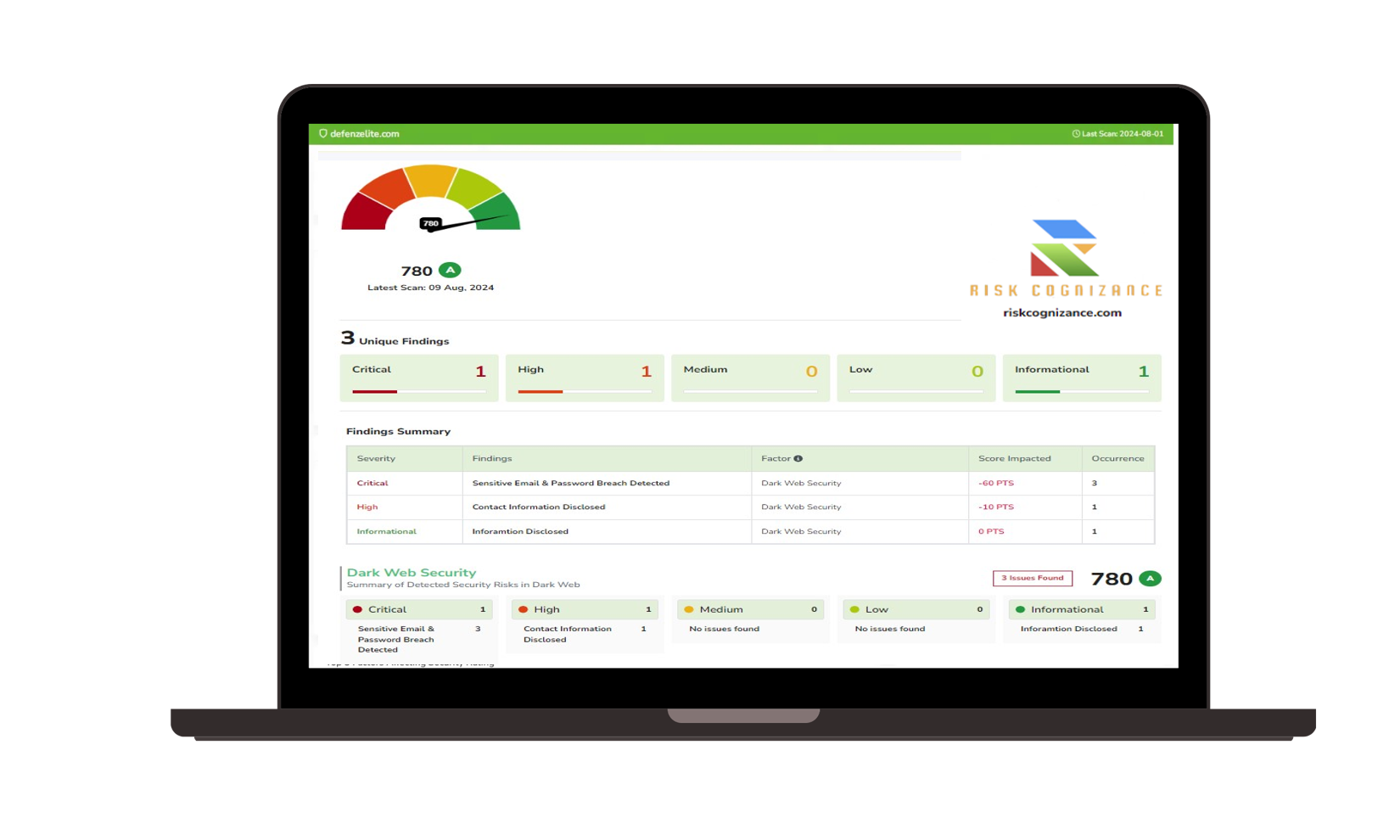
Deep & Dark Web Monitoring refers to the continuous scanning of these hidden areas of the internet, where cybercriminals are known to steal, sell, and trade stolen business and personal data. As a business, you are at risk of having your data exposed or bought and sold in these underground markets without even knowing it. By proactively monitoring these spaces, you can detect potential threats before they escalate into full-blown cyberattacks.
How does it work?
- Continuous Scanning: Our monitoring tools scan forums, marketplaces, and encrypted networks where illegal activities occur. We search for any mention of your company’s proprietary information, sensitive data, or employee credentials.
- Data Breach Detection: Once any of your organization’s sensitive data (such as passwords, financial records, or internal communications) is found, our system flags it, sending real-time alerts to your security team.
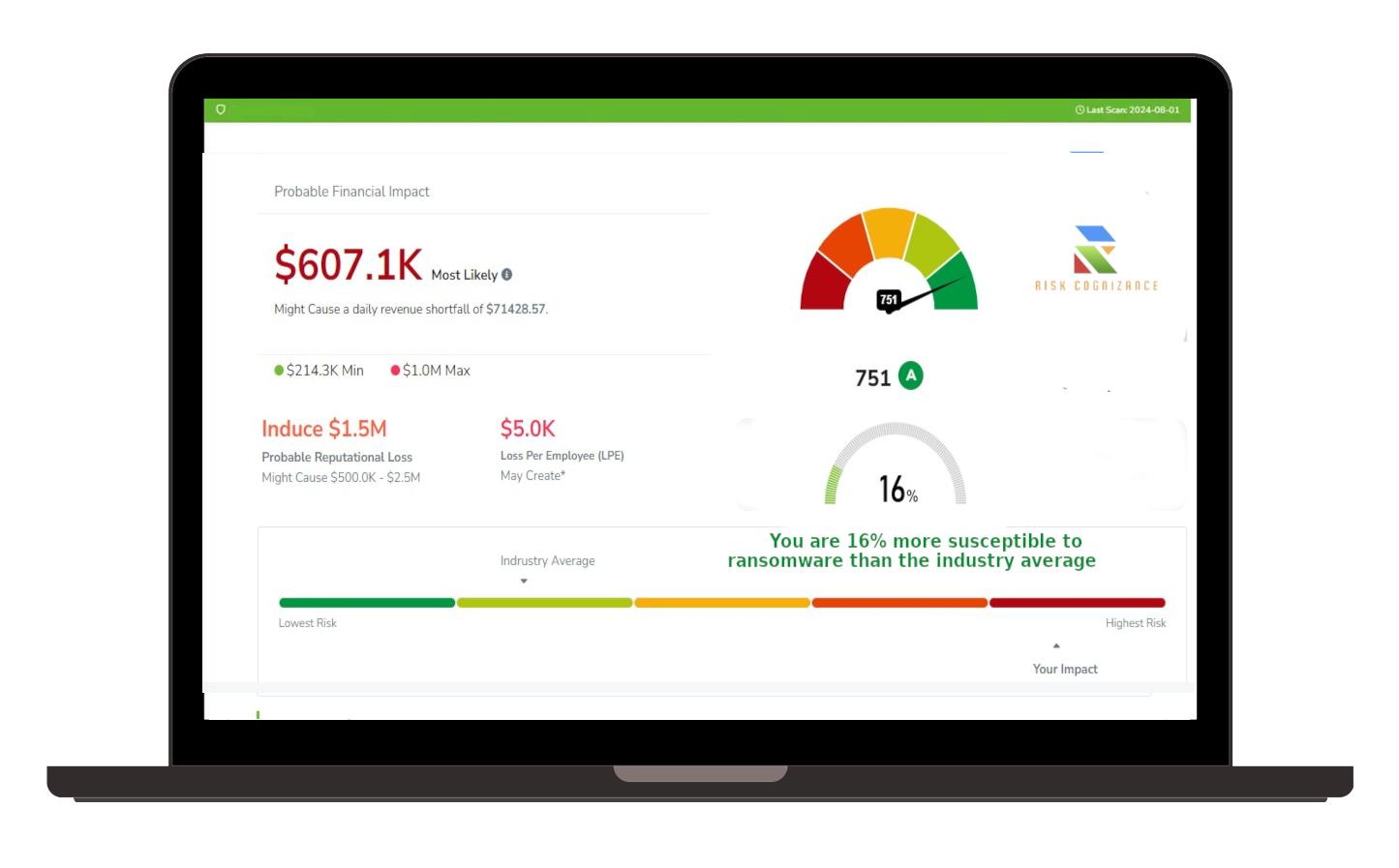
- Risk Assessment & Alerts: We provide in-depth, actionable intelligence about the threat, including the severity of the issue and potential consequences. The alert triggers a response, allowing you to investigate further, mitigate risks, and prevent future breaches.
Why is it important for your business?
Early detection of stolen data can save your business from major financial and reputational damage. Our monitoring solution not only helps you prevent breaches but also ensures compliance with data protection laws, reduces the risk of fraud, and enhances your cybersecurity posture.
Deep and Dark Monitoring Key Features
1. Comprehensive Deep & Dark Web Monitoring
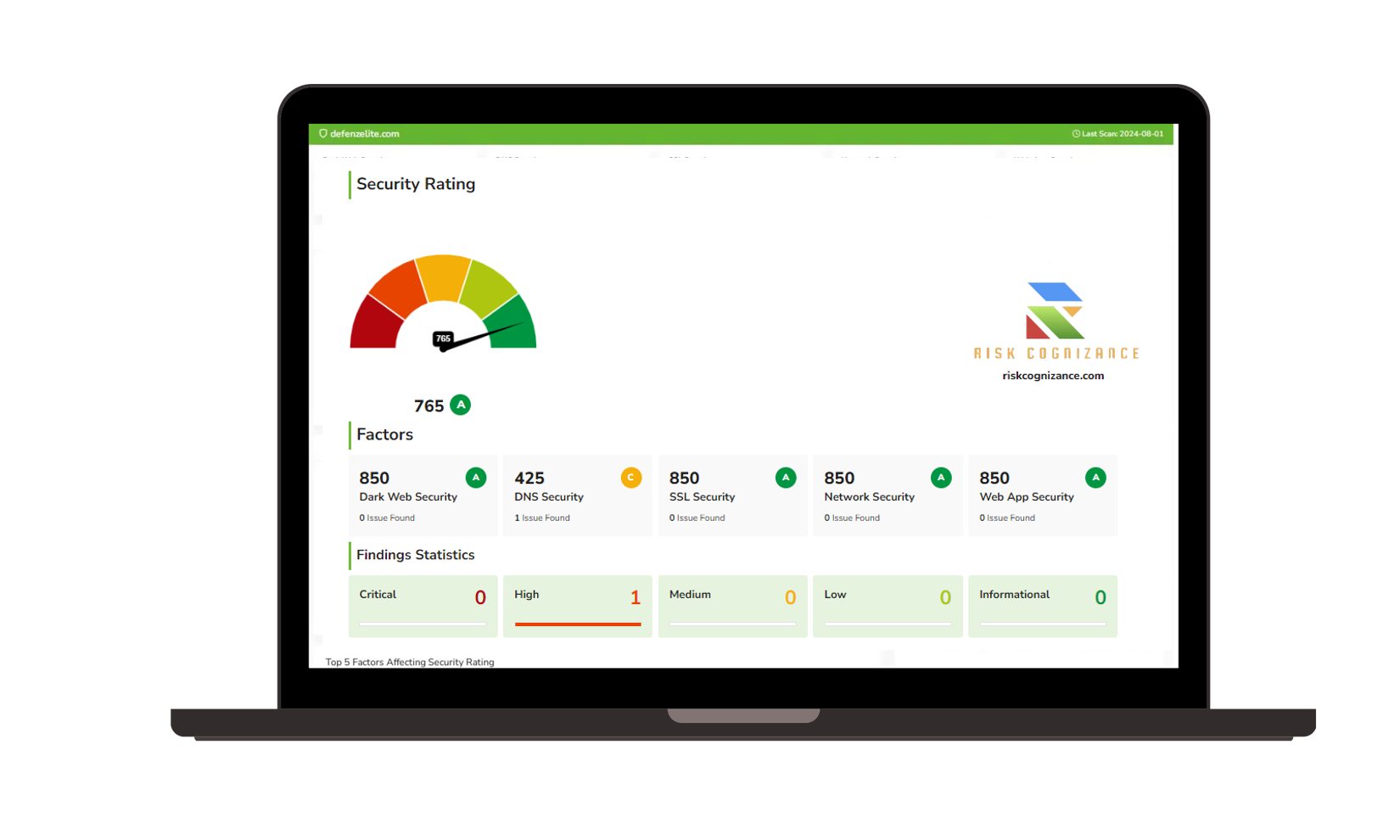
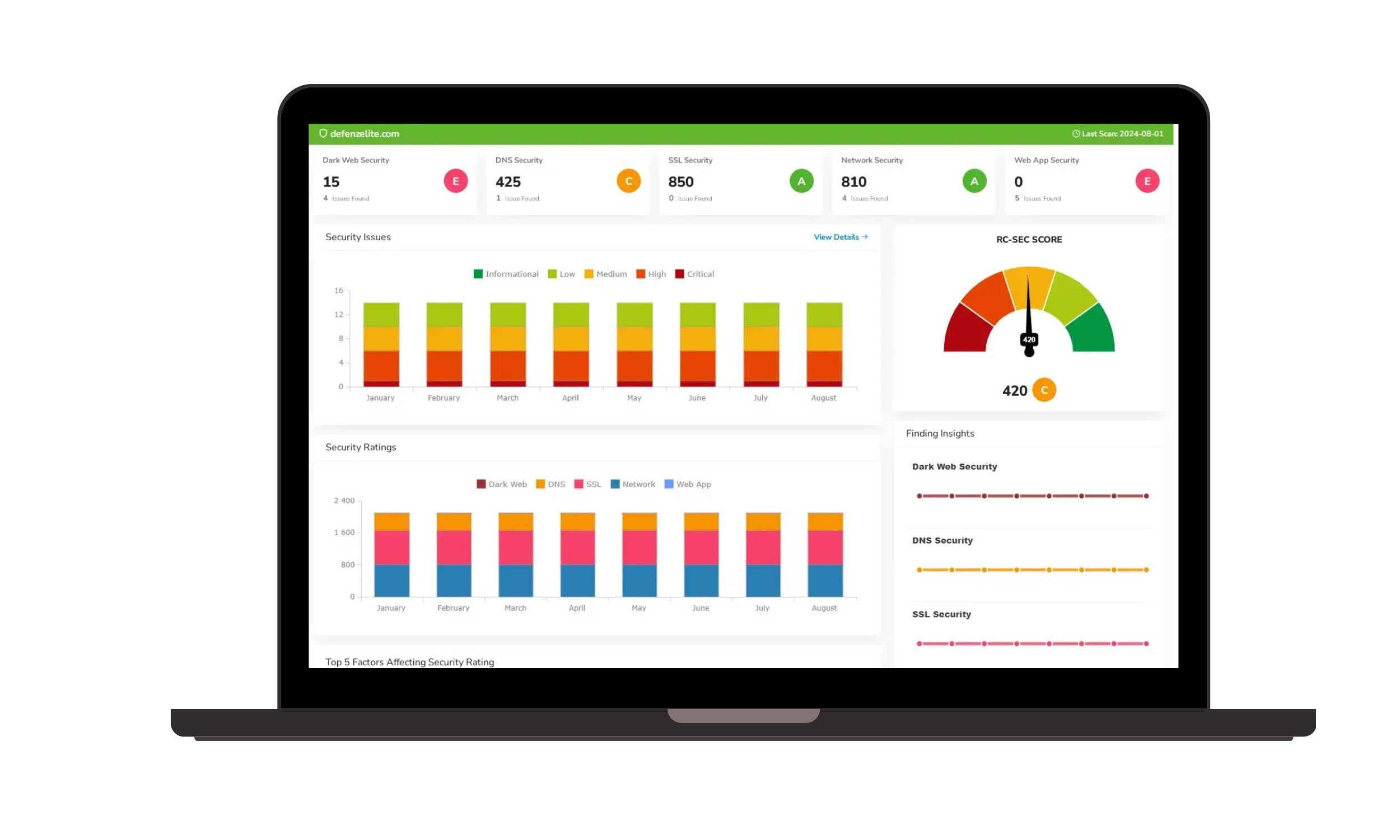
- Real-Time Scanning: Our solution continuously scans the deep and dark corners of the internet to detect any threats or unauthorized use of your business data. This includes hidden marketplaces, dark web forums, encrypted networks, and private messaging platforms.
- Data Theft Detection: We track and identify stolen customer information, login credentials, internal documents, and proprietary data being sold or traded online.
- Threat Intelligence Reports: Detailed insights into which data has been exposed, the severity of the breach, and potential consequences, helping you understand the extent of the threat.
2. Advanced Threat Intelligence
- Customizable Alerts: Set up alerts tailored to your organization’s specific needs. Receive notifications about potential risks associated with your brand, employees, or sensitive data.
- Actionable Insights: Beyond raw data, we provide comprehensive threat intelligence to guide your response. This includes recommendations for mitigating the threat, securing exposed data, and preventing future breaches.
- Fraud and Brand Protection: Protect your organization from identity theft, brand impersonation, and account takeovers, all of which can damage your reputation and lead to financial loss.
3. Early Breach Detection
- Instant Alerts: If your company’s sensitive information is detected on the dark web, you’ll receive real-time alerts so you can act swiftly. This helps you stop cyberattacks before they manifest into data breaches or larger security incidents.
- Contextual Information: Each alert includes detailed context about the detected data (e.g., passwords, social security numbers, credit card details), the specific site it was found on, and the associated risks.
4. 24/7 Monitoring & Support
- Proactive Monitoring: Our team of experts monitors your digital footprint continuously, ensuring that no emerging threats are overlooked, even during off-hours or weekends.
- Dedicated Response Team: In the event of a detected breach or threat, our cybersecurity team is available 24/7 to assist in the mitigation process and help protect your assets.
5. Compliant & Secure
- Regulatory Compliance: Our monitoring solution helps you adhere to data privacy laws such as GDPR, HIPAA, CCPA, and more, ensuring that your business remains compliant while protecting your customers and employees.
- Secure Data Handling: We follow best practices in cybersecurity to ensure that the data we process remains safe, encrypted, and secure, giving you peace of mind.
Why Choose Cyber Risk Cognizance?
Tailored Solutions for Every Industry
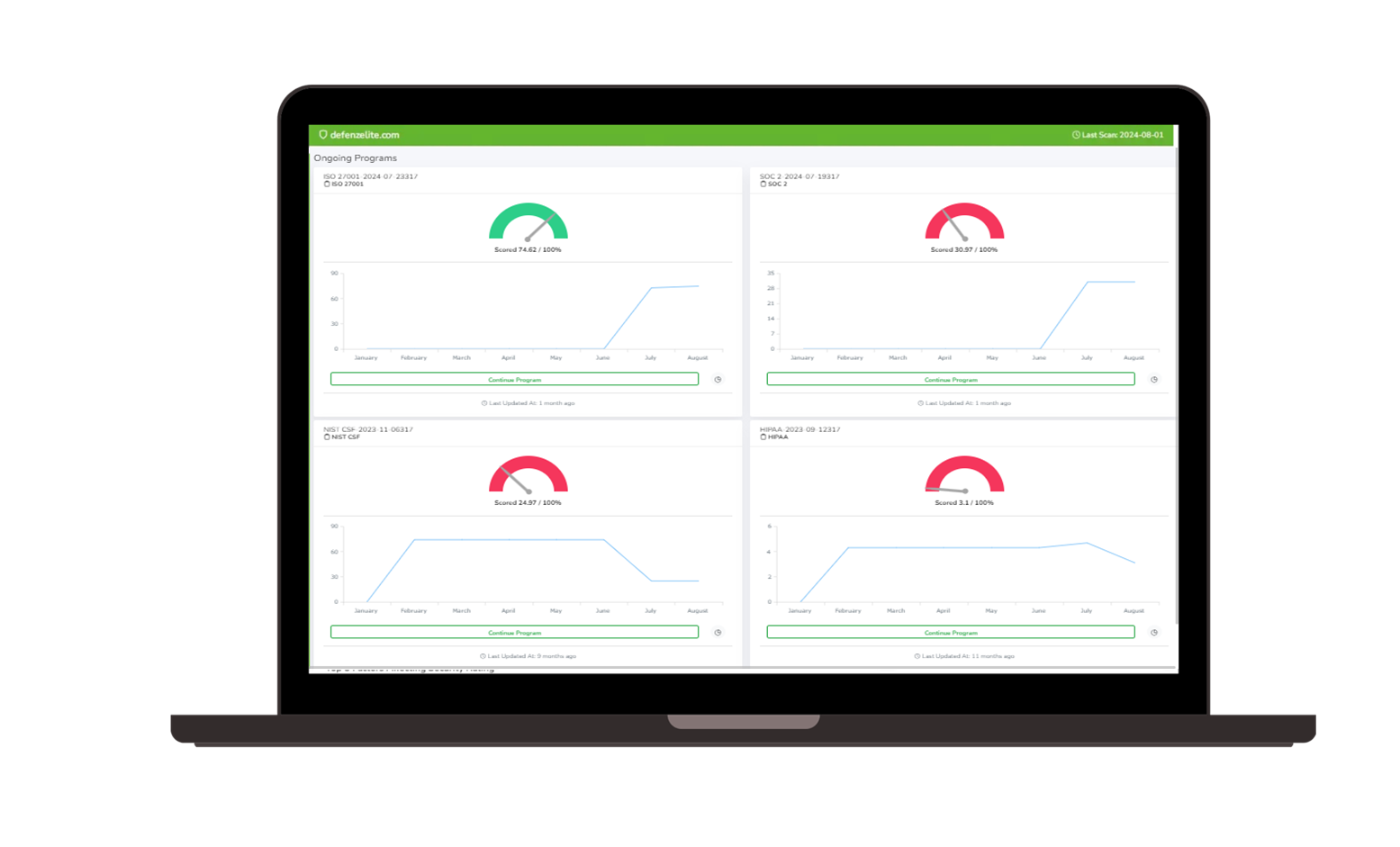
We offer a flexible and scalable solution that can be customized to meet the specific needs of your industry, whether it’s healthcare, finance, e-commerce, or technology. Our experts will configure the monitoring service to match your data security priorities and business risks, providing you with a tailored approach to deep and dark web monitoring.
.
 |  |
 |  |
 |  |
Proactive Threat Detection
With Cyber Risk Cognizance, you don’t need to wait for a breach to occur before acting. We help you detect threats before they escalate, ensuring your business is prepared for potential risks and capable of mitigating them early. Real-time alerts allow you to respond immediately to unauthorized access, safeguarding your assets and reputation.
Actionable Insights
We provide more than just data—we offer insights. Our monitoring platform generates detailed reports and threat intelligence, empowering your team to take swift, effective actions. We ensure that you not only understand the risks but have the information needed to eliminate them.
Scalable for Growing Businesses
Whether you are a startup or an established enterprise, our monitoring services scale to meet your needs. As your business grows, so do your digital security requirements, and our platform adapts to monitor new assets, networks, and threat vectors.
How It Works
Initial Setup & Customization
Our team works closely with you to understand your business needs, set up monitoring parameters, and configure alerts. This includes specifying the types of data you want to monitor (e.g., employee credentials, financial records, intellectual property).
Continuous Scanning & Monitoring
Our system continuously scans hidden forums, marketplaces, and encrypted sites for any signs of your data being exposed. We keep an eye on evolving cybercriminal trends to ensure we detect the latest risks.
Real-Time Alerts & Reporting
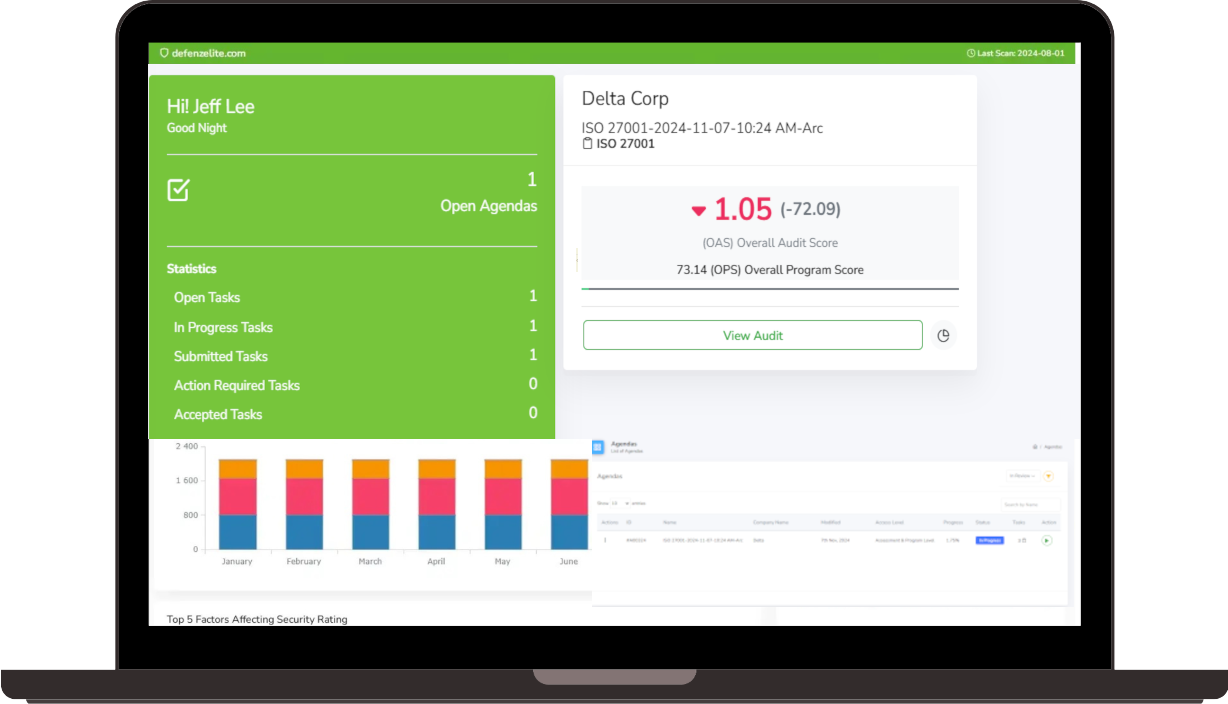
If your data is found in illicit locations, you will receive an immediate alert. Our reporting system includes a detailed analysis of the threat, including what was compromised, where it was found, and what steps to take.
Mitigation & Remediation
Upon identifying a threat, our experts will guide your team through remediation. This could involve removing the compromised data from the dark web, changing exposed passwords, and implementing additional security measures to prevent future breaches.
Benefits for Your Business
- Prevent Data Breaches: By continuously monitoring hidden parts of the internet, we help you detect stolen data before it’s exploited.
- Strengthen Your Cybersecurity Posture: Enhance your cybersecurity defense by actively monitoring potential threats in the deep and dark web.
- Protect Your Brand’s Reputation: Prevent reputational damage by catching brand impersonation and identity theft early.
- Save Time & Resources: Avoid the costly consequences of cyberattacks by detecting threats early and acting proactively.
Who Needs Deep and Dark Web Monitoring?
- Financial Institutions: Protect sensitive financial data and customer information.
- Healthcare Providers: Safeguard patient health records, research data, and confidential healthcare information.
- E-Commerce & Retailers: Secure customer payment data, intellectual property, and your brand reputation.
- Technology & Startups: Safeguard your intellectual property, proprietary code, and internal data.
Customer Testimonials
"The real-time alerts provided by Cyber Risk Cognizance have been invaluable in helping us identify potential threats before they turn into major breaches. Their expertise and proactive monitoring have saved us time and money."
— Sarah L., IT Security Manager, Global Retailer
"We’ve been able to identify and act on potential vulnerabilities that we wouldn't have been aware of without this service. It's an essential part of our cybersecurity strategy."
— David M., Chief Information Security Officer, Financial Services Firm
Pricing & Plans
Choose from flexible pricing plans to suit your business size and needs. From startups to large enterprises, we have a plan that works for you.
- Basic Plan: Ideal for small businesses looking for essential dark web monitoring.
- Professional Plan: Comprehensive monitoring and tailored threat intelligence for growing organizations.
- Enterprise Plan: Full-scale monitoring with custom risk assessments, advanced reporting, and priority support for large organizations.
Start Protecting Your Business Today
Don’t wait for a data breach to happen. Take control of your business's cybersecurity now.
Sign up for a free consultation or demo today to learn how Deep and Dark Web Monitoring for Business can help you stay ahead of cyber threats.
FAQs
What is the Deep Web and Dark Web?
The Deep Web refers to any online content that is not indexed by traditional search engines, including private databases and subscription-based sites. The Dark Web is a small, hidden part of the Deep Web, often used for illegal activities such as selling stolen data.
Why is Dark Web Monitoring Important for My Business?
Cybercriminals often use the Dark Web to sell or trade sensitive information, including stolen data and login credentials. Monitoring these areas helps identify breaches before they impact your business.
How Does the Monitoring Service Work?
Our service continuously scans hidden forums, marketplaces, and encrypted sites for your company's information. If any suspicious activity is detected, we send immediate alerts, followed by detailed reports on the nature of the threat.
Cyber Risk Cognizance: Secure your business today with advanced, actionable insights into the Deep and Dark Web.
Request Callback

