Overview
CIS v8 Compliance Management Software
Adhering to the Center for Internet Security (CIS) v8 benchmarks is essential for organizations striving to protect their IT infrastructure against cybersecurity threats. The Risk Cognizance CIS v8 Compliance Automation Platform offers a robust solution to simplify, automate, and streamline the process of achieving and maintaining compliance with CIS v8 controls. Designed for organizations of all sizes, this platform helps you align your security practices with industry-leading benchmarks, ensuring a fortified defense against cyber threats.
Complete Better CIS v8 Compliance with Risk Cognizance
Risk Cognizance provides an all-in-one platform tailored to manage every aspect of CIS v8 compliance. From implementing security controls to continuous monitoring and audit readiness, our software enables organizations to efficiently meet the 18 CIS v8 control families. Empower your team to safeguard critical assets, reduce vulnerabilities, and enhance overall cybersecurity resilience.
 Governance, Risk, and Compliance (GRC) | 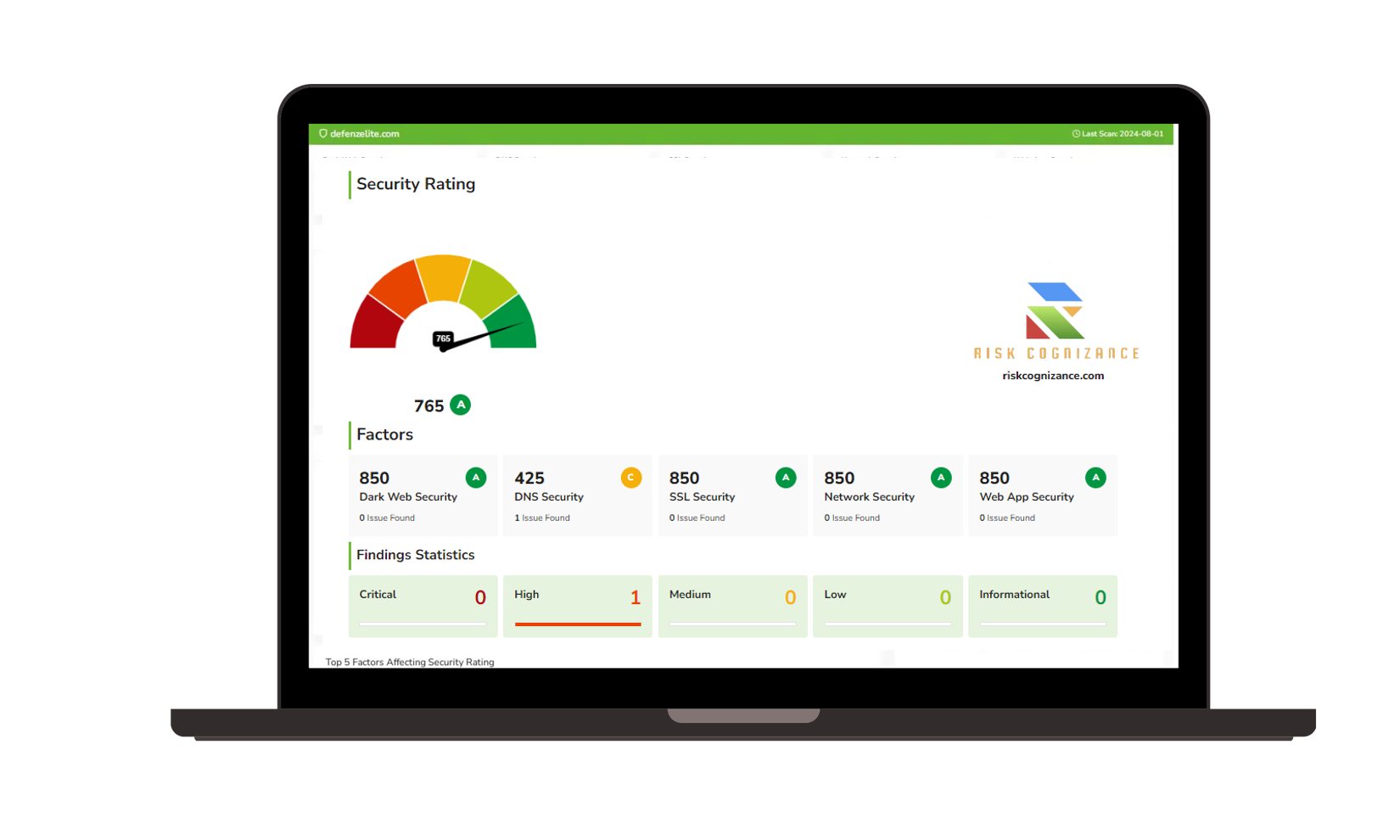 Third-party Risk Management |
 Ransomware Susceptibility | 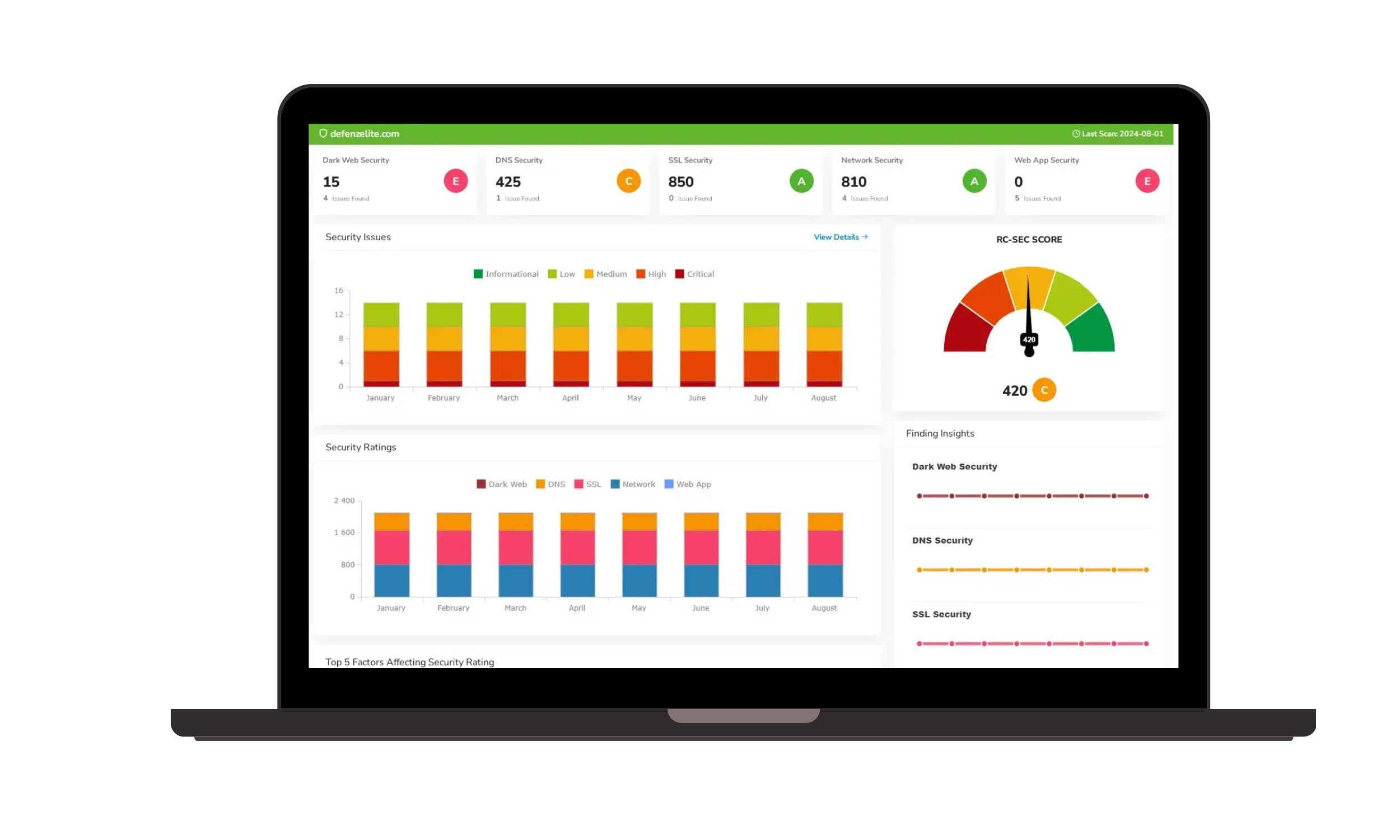 GRC and Attack Surface |
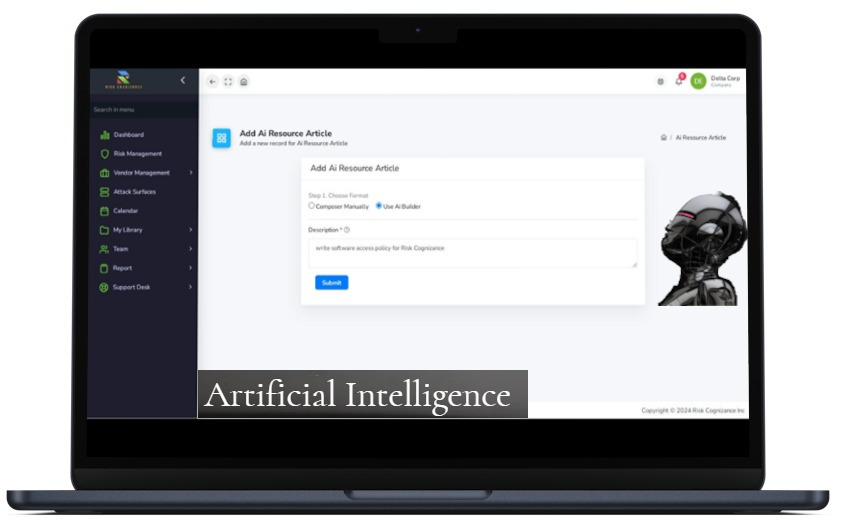
Artificial Intelligence | |
Key Features and Capabilities:
Automated Compliance Workflows:
- Streamline the implementation of CIS v8 controls across your organization.
- Automate compliance tasks, minimizing manual effort and reducing human error.
- Ensure consistent and effective application of security controls.
Comprehensive Control Family Coverage:
- Implement and manage all 18 CIS v8 control families, from Inventory and Control of Enterprise Assets to Penetration Testing.
- Customize your compliance approach to meet your organization’s specific security needs.
- Document and manage controls to align with CIS v8 benchmarks effectively.
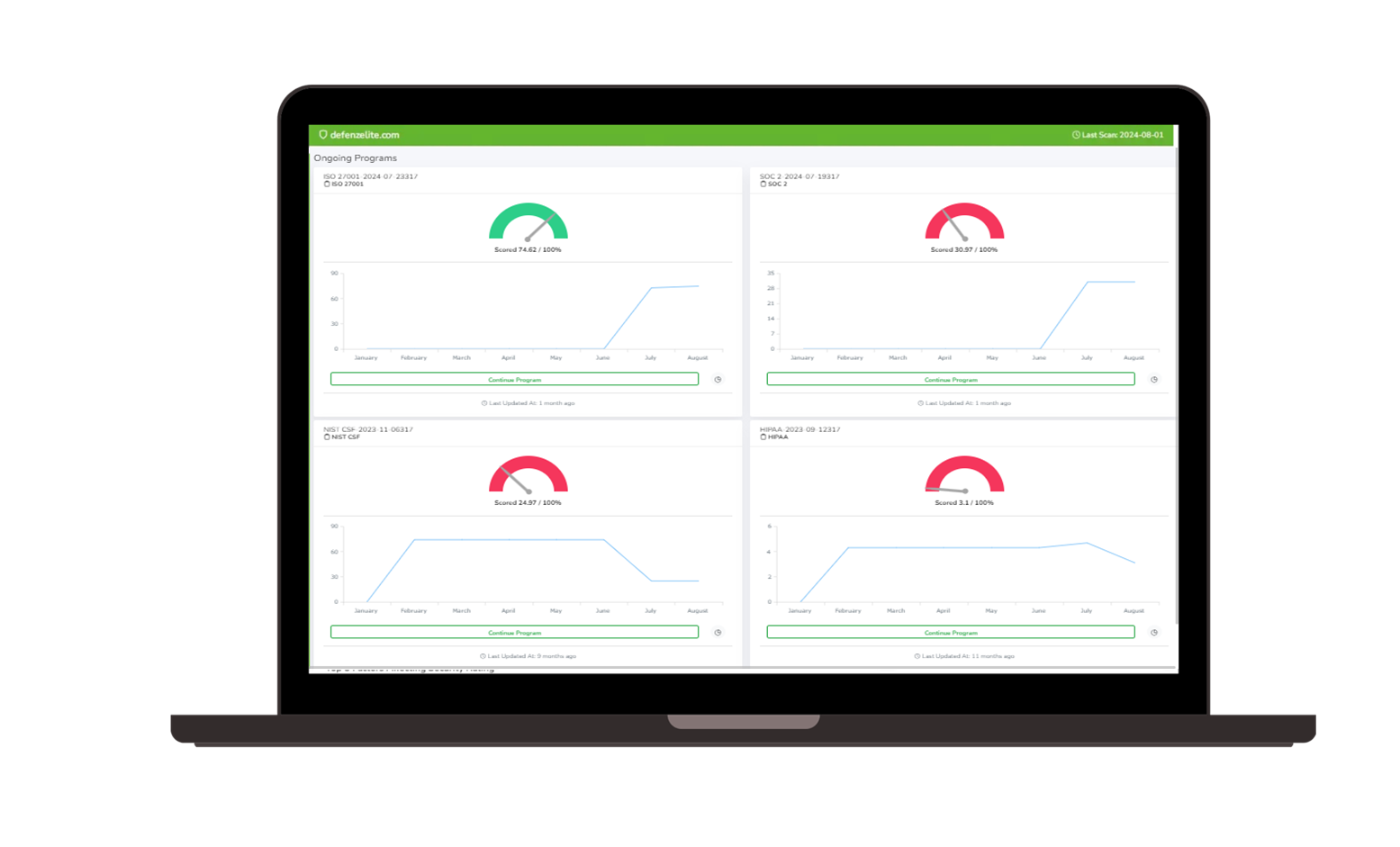
Gap Analysis and Readiness Assessments:
- Perform comprehensive gap analyses to identify areas where your organization needs improvement to meet CIS v8 standards.
- Use readiness assessments to evaluate your current compliance posture and prepare for audits.
- Develop targeted remediation strategies to address identified gaps.
Centralized Documentation Management:
- Manage all CIS v8-related documentation, including policies, procedures, and evidence, in one centralized location.
- Maintain an organized, audit-ready repository for easy access and updates.
- Ensure documentation is consistently updated to reflect the latest compliance efforts.
Continuous Monitoring and Control Testing:
- Implement continuous monitoring to assess the effectiveness of your CIS v8 controls.
- Automate control testing and generate reports that are ready for audit review.
- Gain real-time insights into your compliance status to proactively address potential issues.
Security Incident Management:
- Integrate incident response with your CIS v8 compliance framework.
- Automate the management and reporting of security incidents in accordance with CIS v8 standards.
- Minimize the impact of incidents while ensuring ongoing compliance.
Internal Audits and Continuous Improvement:
- Conduct internal audits to assess the effectiveness of your CIS v8 compliance efforts.
- Identify areas for improvement and implement corrective actions to enhance your cybersecurity program.
- Foster a culture of continuous improvement to maintain a strong security posture.
Customizable Dashboards and Reporting:
- Access real-time dashboards for a comprehensive overview of your CIS v8 compliance status.
- Generate detailed reports tailored for internal stakeholders, auditors, and regulators.
- Customize reporting to meet the specific requirements of your organization and compliance obligations.
Employee Training and Security Awareness:
- Develop and manage security awareness programs that align with CIS v8 requirements.
- Track employee participation in training programs to ensure compliance.
- Cultivate a security-focused culture across your organization.
Policy and Procedure Management:
- Create, distribute, and manage CIS v8-compliant policies and procedures.
- Automate the distribution and acknowledgment tracking of policies within your organization.
- Ensure all policies are up-to-date and aligned with the latest CIS v8 standards.
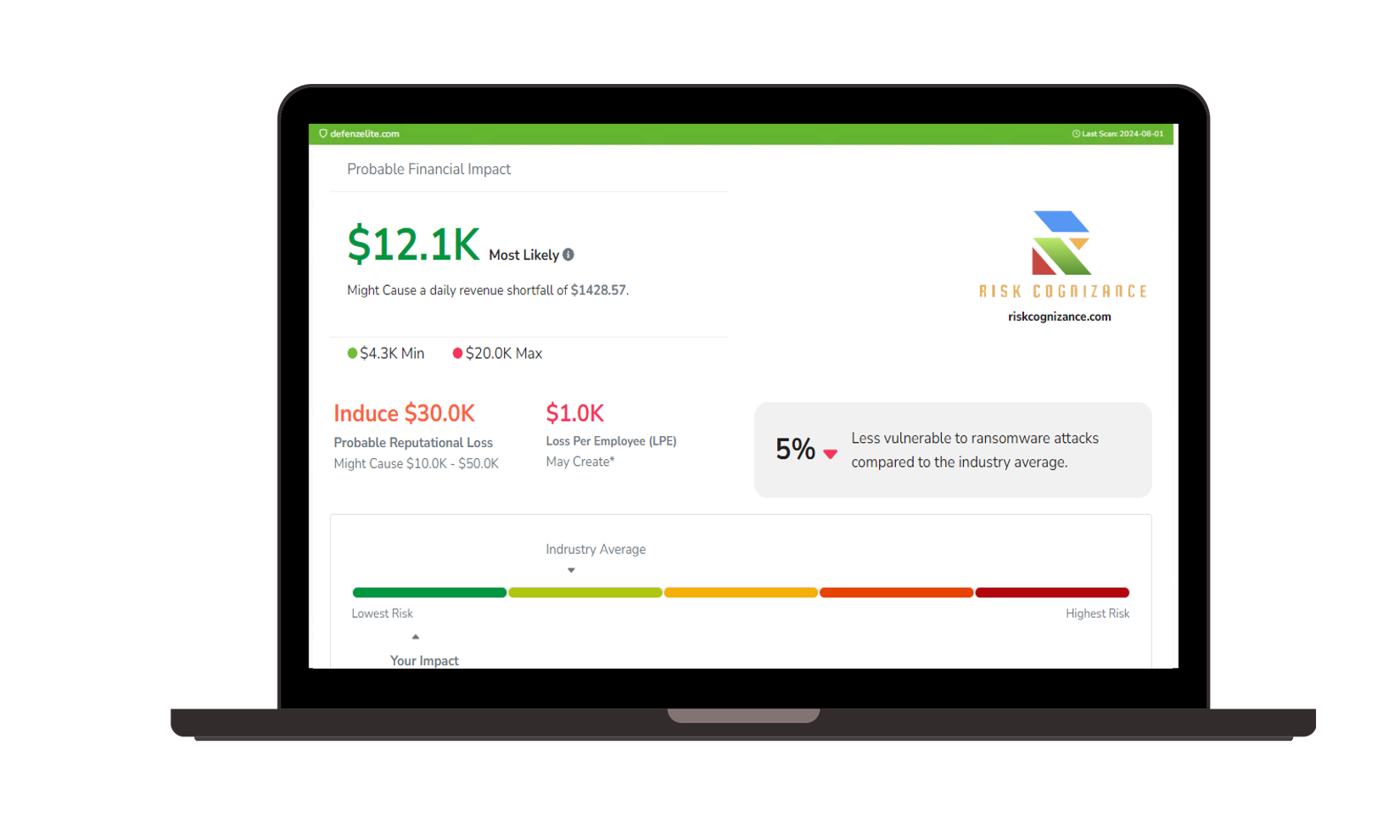
Risk Assessment and Management:
- Conduct ongoing risk assessments to identify and mitigate potential threats to your CIS v8 compliance.
- Automate risk management processes to ensure timely identification and remediation of risks.
- Integrate risk assessments with your overall cybersecurity strategy.
Third-Party Vendor Management:
- Evaluate and monitor third-party vendors to ensure they adhere to CIS v8 standards.
- Automate the process of vendor risk assessments and compliance checks.
- Secure your supply chain by ensuring vendors align with your security benchmarks.
Change Management and Regulatory Updates:
- Stay informed about updates to CIS v8 and related regulatory requirements.
- Assess the impact of changes on your compliance efforts and adjust controls accordingly.
- Maintain compliance with the latest standards through proactive change management.
Task Automation and Workflow Management:
- Automate routine tasks related to CIS v8 compliance, freeing up resources for strategic security initiatives.
- Use automated workflows to ensure timely completion of compliance activities.
- Focus on critical cybersecurity functions while the platform handles compliance tasks.
Integration with Existing Systems:
- Seamlessly integrate Risk Cognizance with your existing IT infrastructure, including SIEM, IAM, and vulnerability management systems.
- Utilize API integrations for customized workflows and data sharing.
- Ensure a unified approach to cybersecurity and compliance across all business systems.
User-Friendly Interface:
- Navigate the platform easily with an intuitive, user-friendly interface.
- Role-based access controls ensure that sensitive data is managed securely.
- Customize the platform to meet the specific needs of your organization.
Dedicated Support and Continuous Platform Updates:
- Access dedicated customer support to ensure smooth implementation and usage.
- Benefit from regular platform updates to keep up with the latest CIS v8 standards.
- Continuous improvements enhance the platform’s capabilities to meet evolving cybersecurity needs.
Achieve CIS v8 Compliance with Confidence
The Risk Cognizance CIS v8 Compliance Automation Platform equips your organization with the tools needed to achieve and maintain compliance with CIS v8 controls. Our platform simplifies the process from control implementation to audit readiness, ensuring that your organization can protect its assets, reduce vulnerabilities, and enhance overall security posture.
Ready to streamline your CIS v8 compliance journey? Contact Risk Cognizance today to discover how our platform can help you meet CIS v8 requirements and strengthen your cybersecurity defenses.
Request Callback