Overview
Attack Surface Management and Cyber Risk Assessment: Proactively Secure Your Digital Environment
Protect Your Organization’s Digital Assets with Comprehensive Attack Surface Management and Cyber Risk Assessment
As cyber threats become increasingly sophisticated, organizations are faced with growing challenges to protect their digital assets. Attack surface management (ASM) and cyber risk assessment solutions help businesses understand, identify, and mitigate the vulnerabilities that could potentially be exploited by attackers. Risk Cognizance offers advanced tools for continuous monitoring of your attack surface, comprehensive cyber risk assessments, and actionable insights to proactively defend against emerging cyber threats. With ASM and risk assessment capabilities, your organization can stay ahead of cyberattacks and enhance its overall cybersecurity posture.
Understanding Attack Surface Management (ASM)
Your organization’s attack surface is constantly evolving as new assets, applications, and third-party services are added to your digital infrastructure. Attack surface management involves continuously monitoring, identifying, and reducing potential vulnerabilities across your organization’s digital ecosystem. Whether it’s internet-facing endpoints, cloud services, third-party vendors, or IoT devices, ASM ensures that your entire attack surface is mapped, understood, and secured to minimize the risk of cyber threats.
The Importance of Cyber Risk Assessment
Cyber risk assessment helps organizations identify, evaluate, and prioritize potential threats to their assets, systems, and data. A thorough risk assessment provides organizations with a clear understanding of the cyber risks they face, allowing them to implement targeted mitigation strategies. By continuously assessing risks and vulnerabilities, organizations can reduce their attack surface and ensure the security of their digital environment.
With Risk Cognizance’s Attack Surface Management and Cyber Risk Assessment tools, businesses can gain real-time visibility into their digital infrastructure, understand where risks exist, and take action to close security gaps before they are exploited by attackers.
Key Benefits
Continuous Visibility into Your Attack Surface
A comprehensive view of your organization’s attack surface is crucial to identifying potential vulnerabilities. Our solution provides continuous visibility into all digital assets, ensuring that no endpoint or resource goes unnoticed, even as your infrastructure evolves.
- Automated Asset Discovery: Automatically identify all digital assets, including cloud services, endpoints, applications, and third-party vendors, across your organization’s attack surface.
- Real-Time Risk Identification: Continuously monitor for emerging risks and vulnerabilities, providing real-time alerts and insights into areas that need immediate attention.
- Dynamic Attack Surface Mapping: Continuously map and update your attack surface as your organization’s digital footprint changes, ensuring that you have an up-to-date view of your security posture.
Proactive Cyber Risk Assessment
Risk Cognizance’s Cyber Risk Assessment tools enable organizations to conduct comprehensive assessments to identify and quantify risks. By evaluating the likelihood and potential impact of various cyber threats, you can prioritize remediation efforts based on business-critical areas.
- Vulnerability Scanning and Risk Analysis: Regularly scan for vulnerabilities in your digital assets, applications, and third-party integrations to identify potential attack vectors.
- Risk Scoring and Prioritization: Automatically score and rank risks based on their severity, impact, and likelihood, allowing your security team to focus on the most critical areas.
- Scenario-Based Risk Modeling: Model potential attack scenarios to understand how vulnerabilities could be exploited and assess their impact on your organization.
Real-Time Threat Intelligence and Alerts
Cyber threats evolve quickly, and organizations need to respond promptly to prevent damage. Our ASM and Cyber Risk Assessment solution provides real-time threat intelligence and alerts to keep your security team informed about emerging risks.
- Threat Intelligence Integration: Integrate with threat intelligence feeds to stay updated on the latest threats, vulnerabilities, and cyberattacks targeting your industry.
- Real-Time Alerts and Notifications: Receive immediate alerts when new vulnerabilities or risks are detected across your attack surface, allowing your team to take rapid action.
- Automated Risk Reports: Generate automated risk assessment reports that provide detailed information on vulnerabilities, exposure levels, and recommended actions.
Enhanced Vulnerability Management and Mitigation
Our solution helps organizations manage vulnerabilities effectively by providing detailed insights into your digital assets and their potential weaknesses. By identifying and prioritizing vulnerabilities, you can implement targeted remediation strategies to strengthen your security posture.
- Automated Vulnerability Scanning: Perform regular, automated vulnerability scans to detect weaknesses in your network, endpoints, and applications.
- Vulnerability Prioritization: Rank vulnerabilities based on risk and impact to ensure that critical issues are addressed first, minimizing the chance of exploitation.
- Actionable Mitigation Strategies: Receive actionable recommendations for remediating vulnerabilities, whether through patching, reconfiguration, or other security measures.
Third-Party Risk and External Threats Monitoring
Third-party vendors, contractors, and partners can introduce significant risks to your organization’s security. Risk Cognizance’s ASM solution monitors external relationships and third-party assets to ensure they are properly secured and do not pose a risk to your attack surface.
- Third-Party Asset Discovery: Automatically discover and assess third-party assets and connections, including vendor applications and integrations, to identify potential risks.
- Third-Party Risk Scoring: Evaluate the security posture of third-party vendors and partners, scoring them based on risk exposure and security practices.
- External Threat Monitoring: Continuously monitor external threats and attacks targeting third-party vendors to ensure that your organization remains protected from indirect risks.
Explore Our Attack Surface Management and Cyber Risk Assessment Technologies
Risk Cognizance provides a suite of advanced tools designed to help businesses gain continuous visibility into their attack surface, assess cyber risks effectively, and implement mitigation strategies that reduce vulnerabilities and enhance overall security. Here are the key technologies behind our solution:
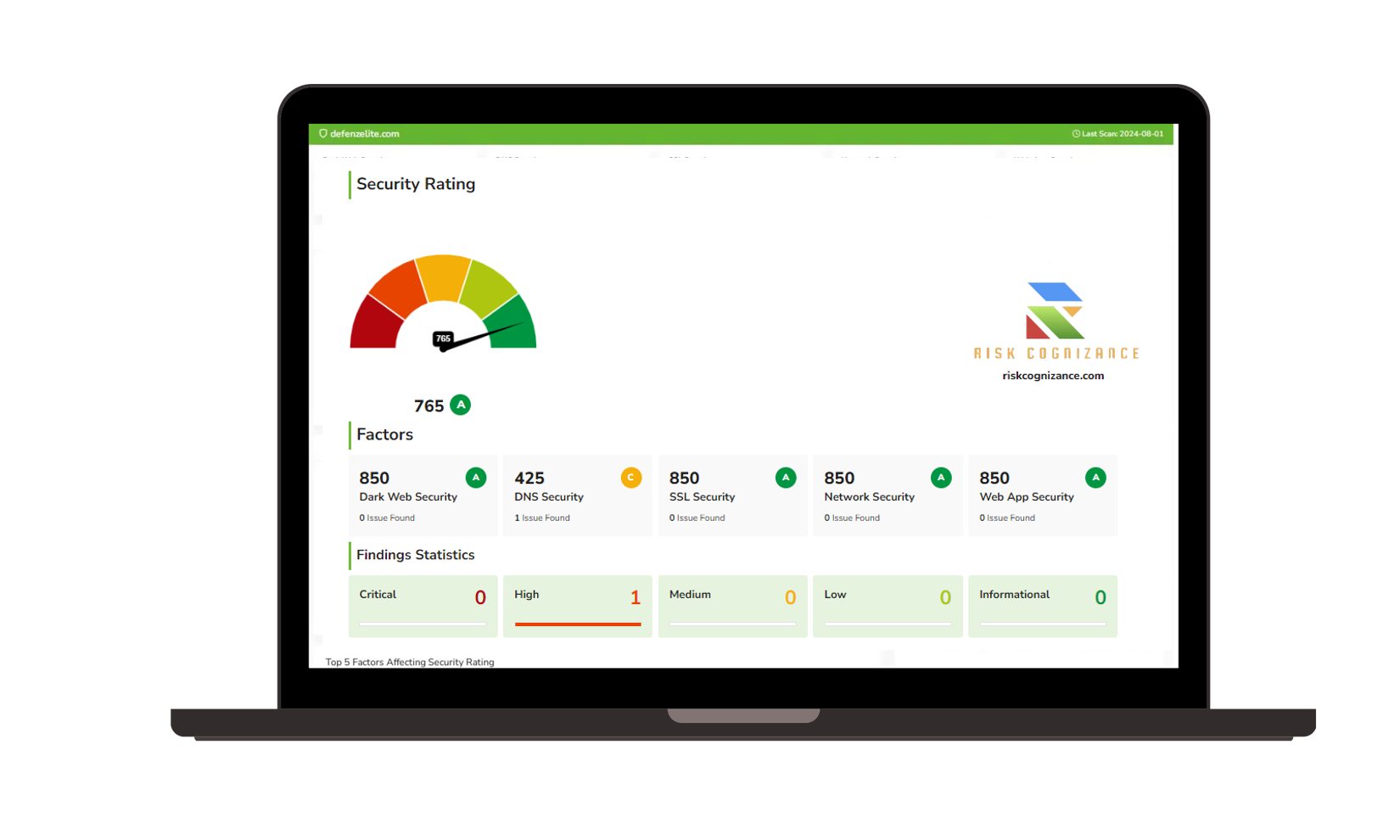
Attack Surface Discovery and Mapping
Gain a complete and accurate view of your attack surface with our automated asset discovery and mapping tools. From cloud services to network devices, every asset is continuously discovered and monitored for potential risks.
- Automated Asset Discovery: Automatically scan your network, cloud services, and endpoints to identify all devices, applications, and systems connected to your environment.
- Attack Surface Mapping: Map and visualize your organization’s attack surface, ensuring that every asset is accounted for and secure.
- Real-Time Asset Updates: Keep your attack surface map up-to-date with real-time updates as new assets are added or removed from your environment.
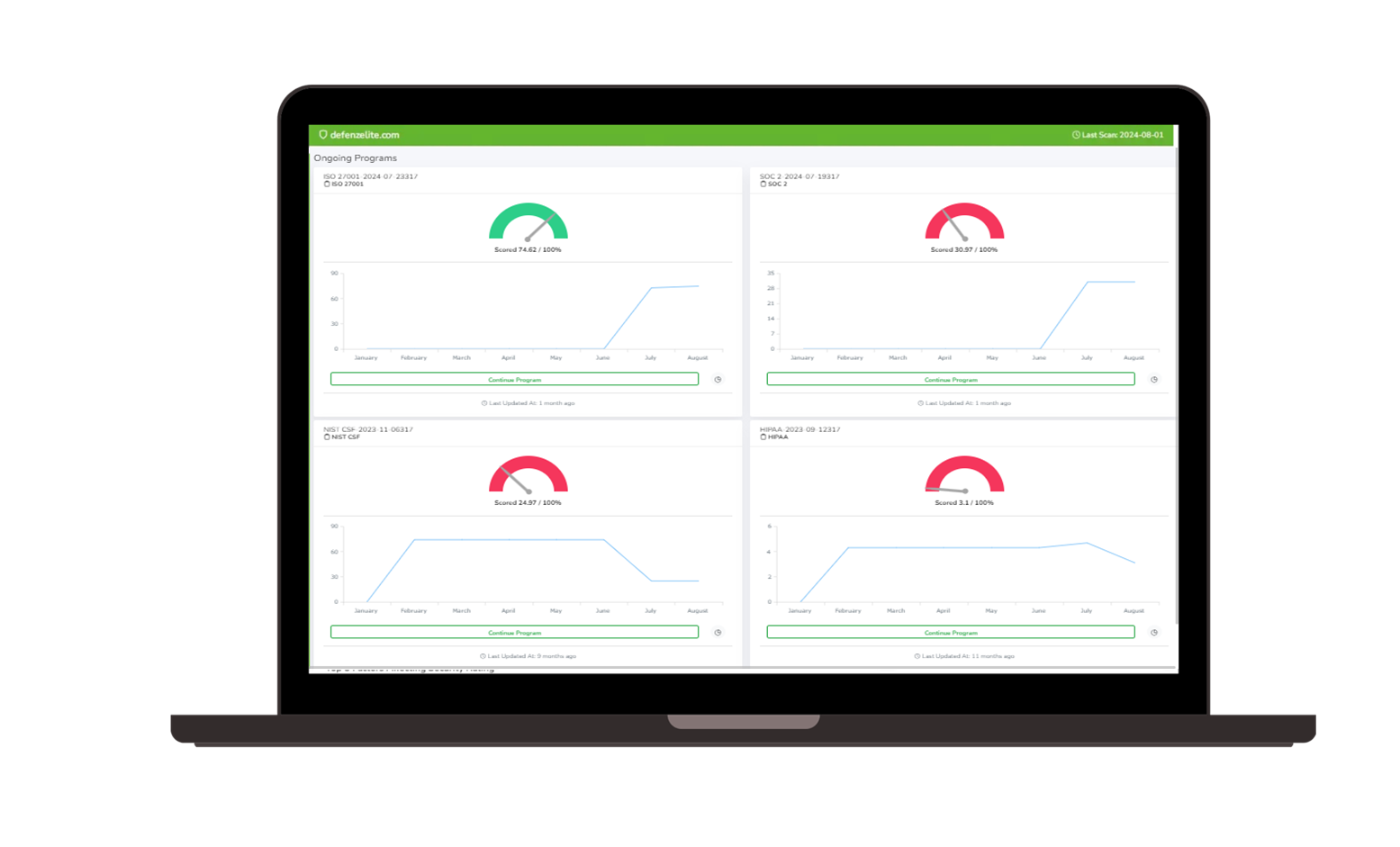
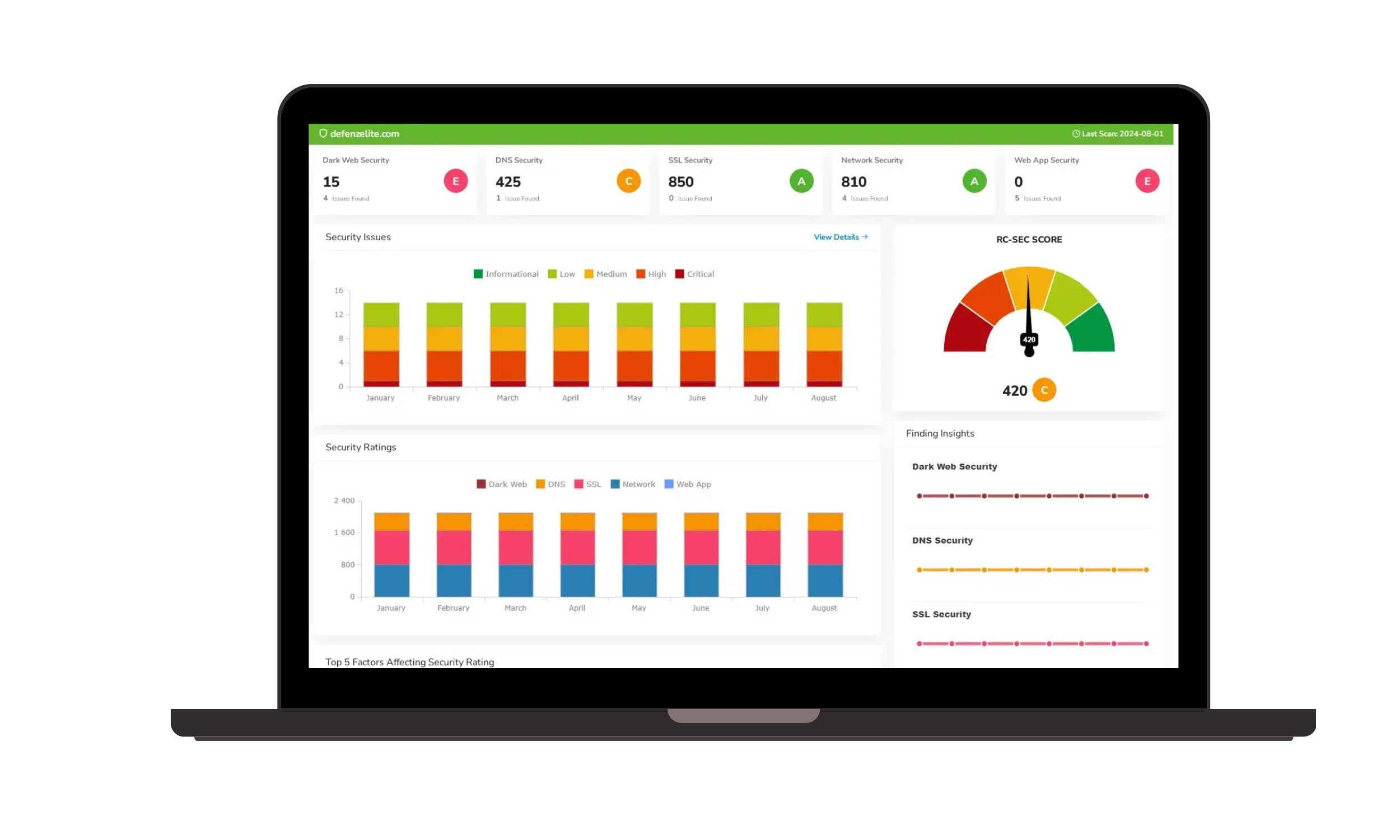
Cyber Risk Assessment Platform
Evaluate and prioritize risks across your organization’s entire attack surface. Our platform helps organizations conduct comprehensive risk assessments that include vulnerability scanning, risk scoring, and scenario modeling to ensure robust cybersecurity practices.
- Vulnerability Scanning: Conduct regular, thorough scans of your systems, networks, and applications to uncover weaknesses that could be exploited.
- Risk Scoring and Prioritization: Assign risk scores to identified vulnerabilities based on their severity and potential business impact, allowing for better prioritization.
- Scenario Modeling: Simulate potential attack scenarios to understand the impact of vulnerabilities and improve your security response strategies.
 |  |
 |  |
 |  |
Threat Intelligence Integration
Stay ahead of emerging cyber threats with real-time threat intelligence. Our solution integrates with industry-leading threat intelligence feeds, allowing you to receive up-to-the-minute updates on potential threats that may impact your organization’s digital assets.
- Threat Intelligence Feeds: Integrate with trusted threat intelligence sources to get continuous updates on new attack vectors, vulnerabilities, and threat actor tactics.
- Contextual Threat Alerts: Receive alerts with detailed context on how specific threats may impact your organization’s attack surface.
- Proactive Threat Monitoring: Continuously monitor for emerging threats that could compromise your security posture and take action before an attack occurs.
Vulnerability Management and Remediation
Efficient vulnerability management is critical to protecting your organization from cyberattacks. Our solution helps you identify, prioritize, and remediate vulnerabilities to reduce your attack surface and improve security.
- Automated Vulnerability Scans: Perform regular automated scans to detect vulnerabilities across your systems and networks.
- Risk-Based Prioritization: Prioritize vulnerabilities based on severity and potential impact, focusing resources on the most critical areas first.
- Actionable Remediation Recommendations: Receive actionable insights on how to mitigate vulnerabilities, whether through patching, reconfiguration, or other security controls.
Third-Party and Supply Chain Risk Management
Minimize the risks introduced by third-party vendors and supply chain partners with comprehensive risk assessments and monitoring tools. Ensure that third-party relationships do not create new vulnerabilities or security gaps.
- Third-Party Risk Assessment: Assess the security posture of third-party vendors and partners before engaging with them, ensuring they meet your security and compliance requirements.
- Continuous Third-Party Monitoring: Continuously monitor third-party systems and applications for vulnerabilities and threats that could affect your organization’s security.
- Supply Chain Security: Identify risks across your supply chain and ensure that partners and vendors have strong security practices in place to protect your data and systems.
Our Solutions
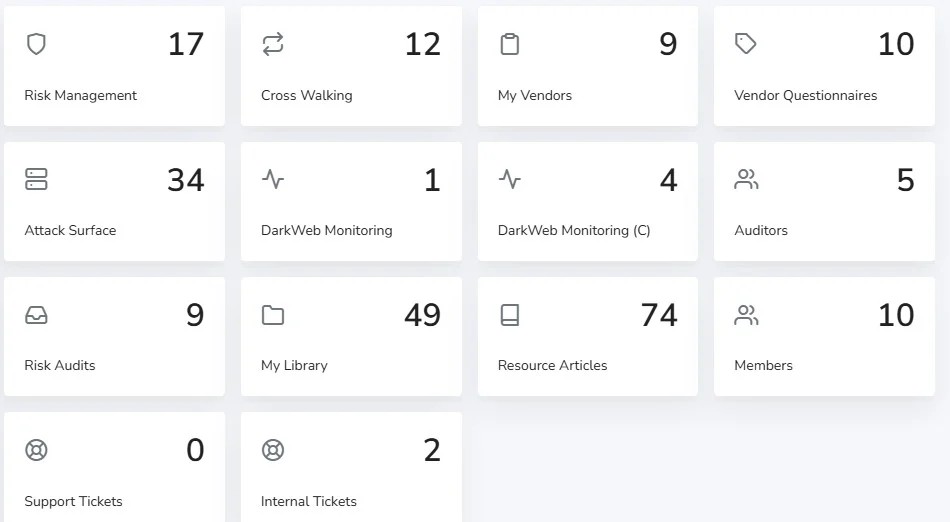
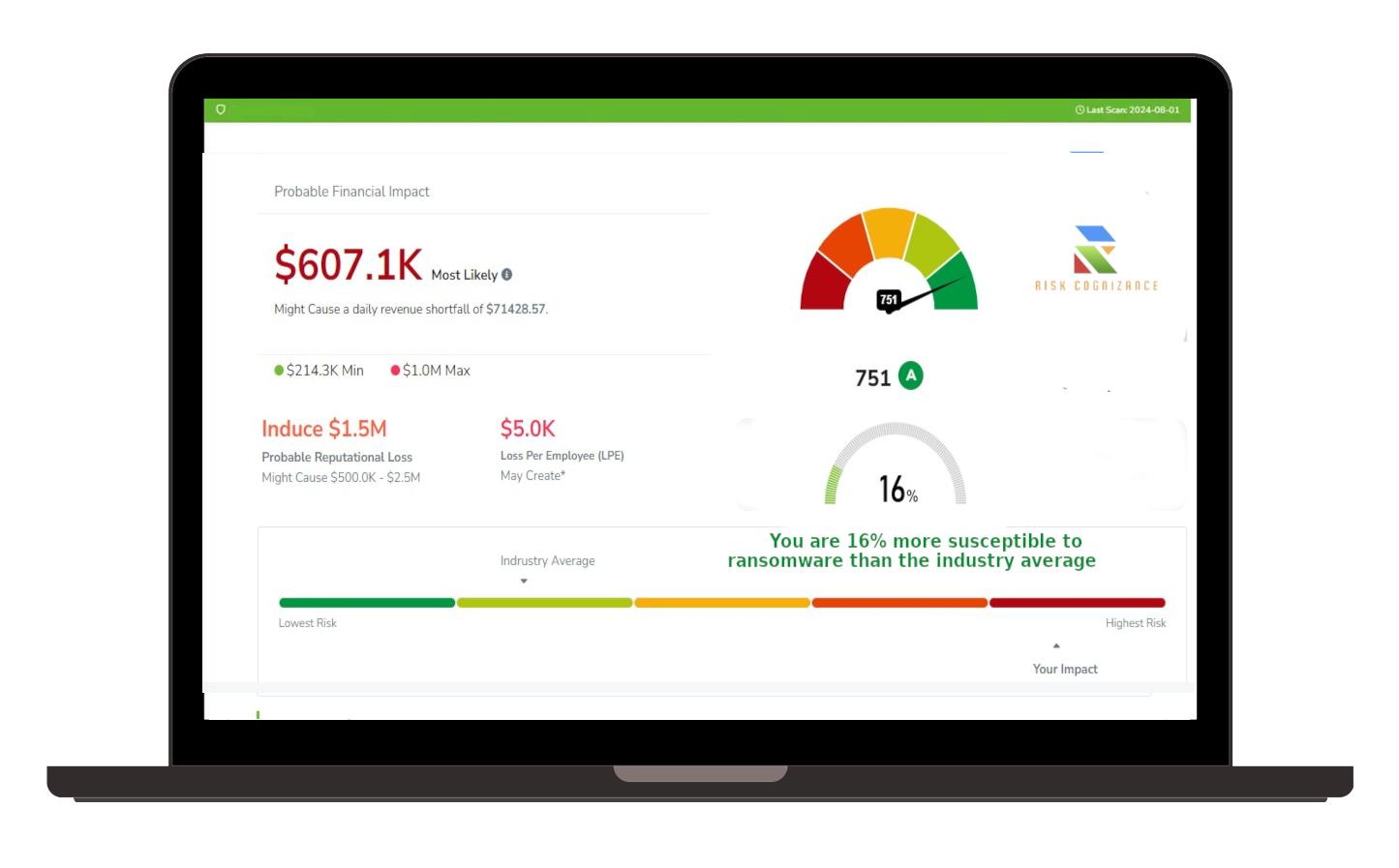
Attack Surface Management Dashboard
Gain deep visibility into your attack surface with our user-friendly dashboard. Monitor vulnerabilities, risks, and potential threats across your digital infrastructure and take action quickly to mitigate risks.
- Comprehensive Dashboards: View all your attack surface assets, their associated risks, and vulnerabilities from a single, interactive dashboard.
- Risk Analytics and Insights: Use analytics tools to visualize risk trends, identify weak points, and assess how emerging threats could impact your attack surface.
- Customizable Views: Tailor the dashboard to show the most relevant data, allowing you to focus on the areas that matter most to your organization’s cybersecurity.
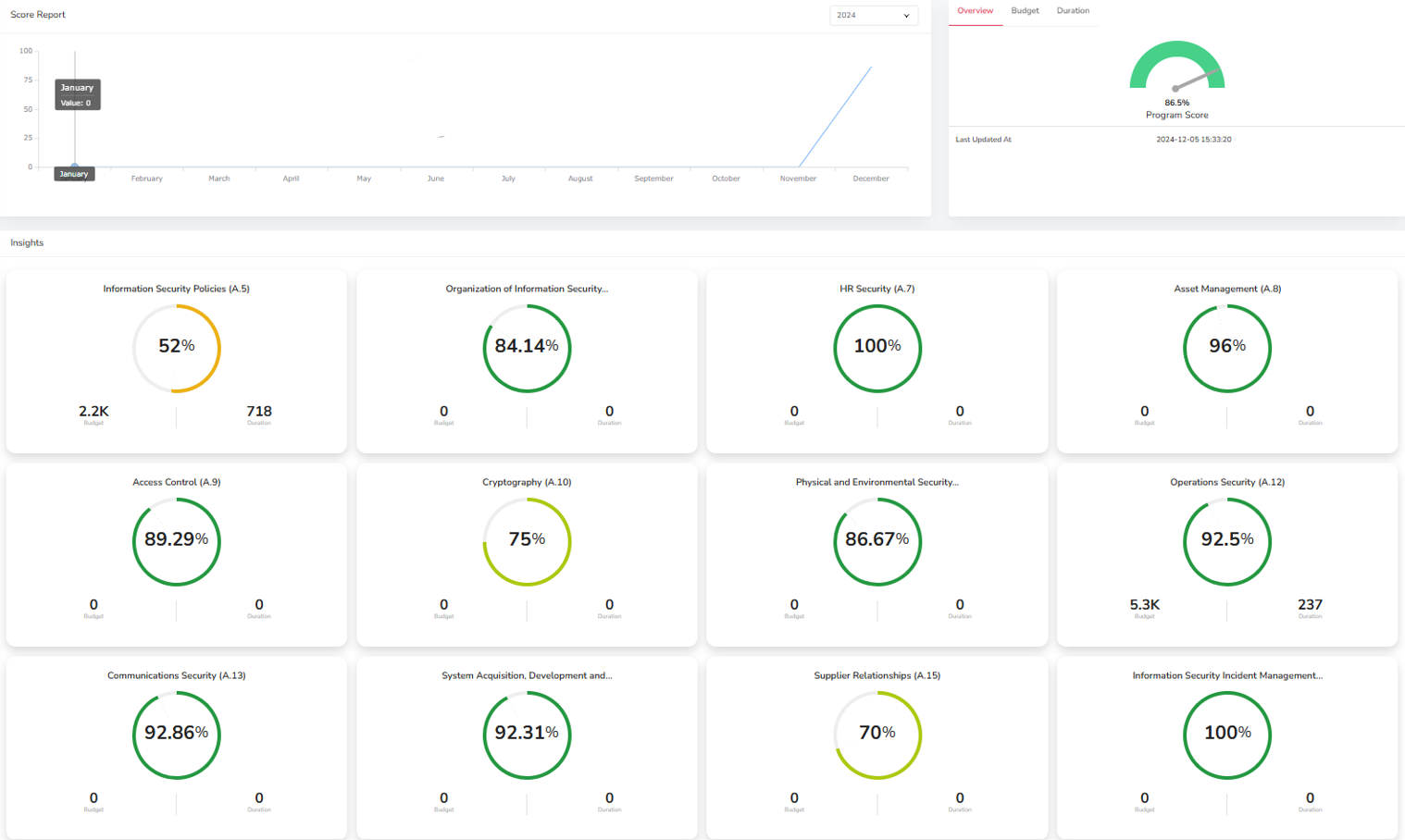
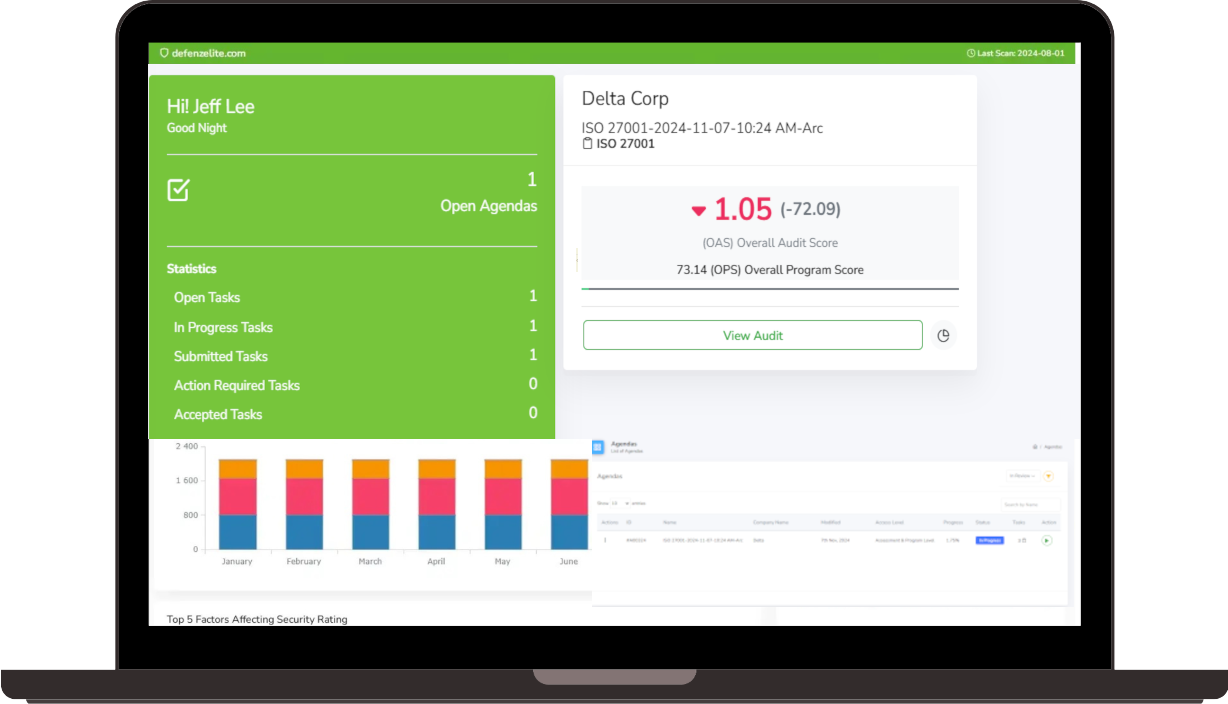
Cyber Risk Assessment Reports
Generate automated risk assessment reports to document your cybersecurity efforts, identify vulnerabilities, and guide remediation strategies. These reports provide transparency to stakeholders and help inform strategic decision-making.
- Risk Assessment Reports: Generate detailed reports based on vulnerability scans, risk scoring, and threat intelligence to guide your security decisions.
- Compliance Reports: Ensure compliance with industry regulations and standards by creating reports that demonstrate your organization’s adherence to security best practices.
- Incident and Breach Reports: Automatically generate reports when a vulnerability or threat leads to an incident
Request Callback

