Risk Cognizance GRC Platform: Revolutionizing Governance, Risk, and Compliance
{strip_tags(Str::limit($blog->description , 140))}
Read MoreNavigating Legal Risks in Cybersecurity – A CISO’s Guide to Avoiding Consequences
{strip_tags(Str::limit($blog->description , 140))}
Read MoreSimplify Compliance and Enhance Cybersecurity with Risk Cognizance
{strip_tags(Str::limit($blog->description , 140))}
Read MoreElevating GRC with Risk Cognizance: A Comprehensive Solution for Modern Organizations
{strip_tags(Str::limit($blog->description , 140))}
Read MoreThe General Data Protection Regulation (GDPR): A Guide to Protecting Personal Data
{strip_tags(Str::limit($blog->description , 140))}
Read More
.jpg)
.jpg)





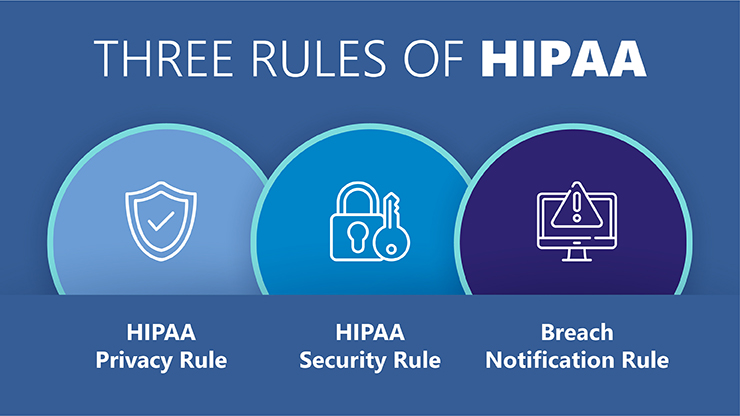

.jpg)