Overview
Ransomware susceptibility refers to an organization’s vulnerability to ransomware attacks, which are malicious events where attackers encrypt data or lock users out of their systems until a ransom is paid. This susceptibility is influenced by various factors, including outdated software, weak network configurations, and ineffective user practices. Critical vulnerabilities such as unpatched systems or insecure network settings can provide entry points for attackers. Additionally, user behaviors, such as falling for phishing scams or using weak passwords, can further increase risk. Inadequate backup practices and a lack of robust incident response plans also contribute to heightened susceptibility. Assessing and addressing these weaknesses through regular vulnerability scans, effective patch management, and comprehensive user training are essential steps in reducing an organization’s risk and enhancing its overall security posture against ransomware threats.
- Ransomware Susceptibility: Provide an overview of the organization’s vulnerabilities to ransomware attacks. Highlight key areas of weakness in security measures, system configurations, and user practices.
- Business Impact: Summarize the potential operational disruptions, data loss, reputational damage, and regulatory implications that could arise from a ransomware attack.
- Financial Loss: Outline the estimated financial consequences, including potential ransom payments, recovery costs, revenue loss, and other financial impacts.
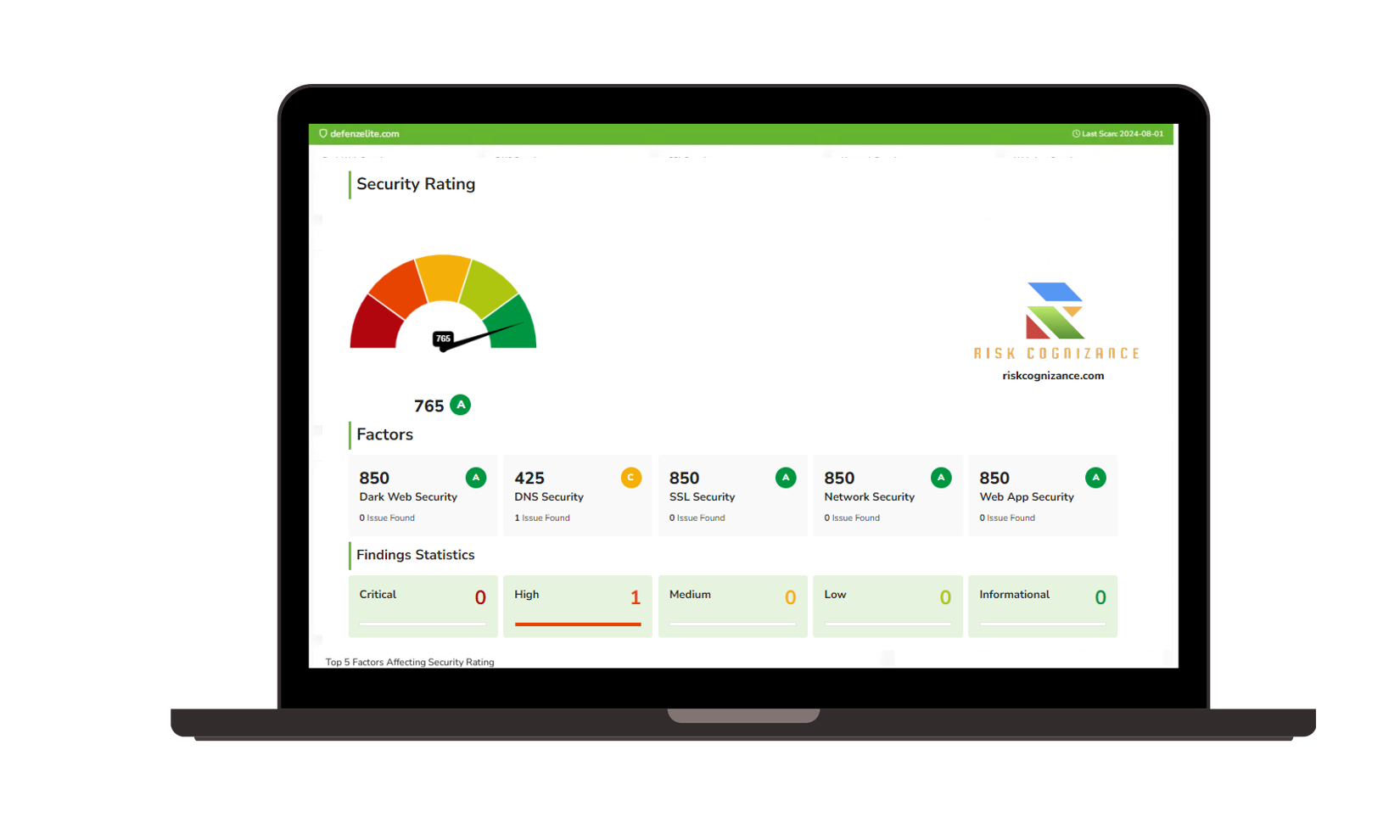


2. Methodology
- Assessment Techniques: Based on vendor questionnaire, attack surface, and security posture
- Tools and Frameworks: NIST CSF
3. Current Security Posture
- Existing Security Measures: Outline current security measures in place, such as antivirus software, firewalls, and backup systems.
- Incident Response Plan: Review the organization’s plan for responding to ransomware incidents.
4. Vulnerability Assessment
- System Vulnerabilities: Identify any vulnerabilities in software, hardware, or network configurations.
- User Behavior: Assess risks related to user practices, such as weak passwords or susceptibility to phishing attacks.
- Patch Management: Evaluate how effectively the organization manages and applies patches and updates.
5. Risk Assessment
- Likelihood of Attack: Analyze the probability of a ransomware attack based on identified vulnerabilities.
- Potential Impact: Evaluate the potential impact on business operations, including data loss, financial costs, and reputational damage.
6. Business Impact
- Operational Disruption: Assess how a ransomware attack could disrupt normal business operations, including downtime and loss of productivity.
- Financial Costs: Estimate the potential financial impact, including ransom payments, recovery costs, and loss of revenue.
- Data Loss: Consider the implications of data loss, including impacts on customer data, intellectual property, and compliance with regulations.
- Reputational Damage: Evaluate how a ransomware incident could affect the organization’s reputation and customer trust.
- Regulatory and Legal Consequences: Outline possible legal and regulatory ramifications, such as fines or legal action due to data breaches or non-compliance with data protection laws.
