
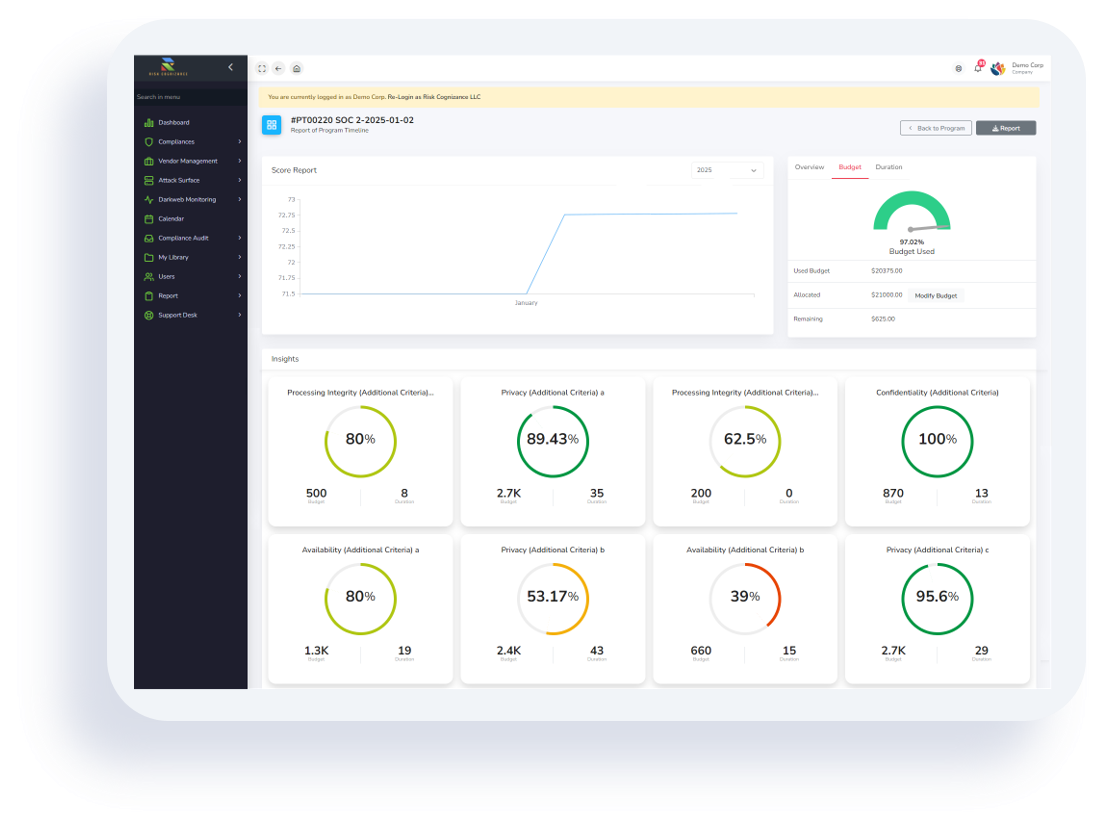
Overview
SOC-2 Compliance Management & Automation
In an era defined by ubiquitous data exchange and the relentless expansion of cloud services, the integrity and security of customer data are not merely operational considerations; they are the bedrock of trust and a critical component of enterprise resilience. For service organizations handling sensitive information, SOC-2 Compliance stands as the definitive benchmark of commitment to data security and operational integrity. It is not merely a certification; it is a declaration of a robust control environment.
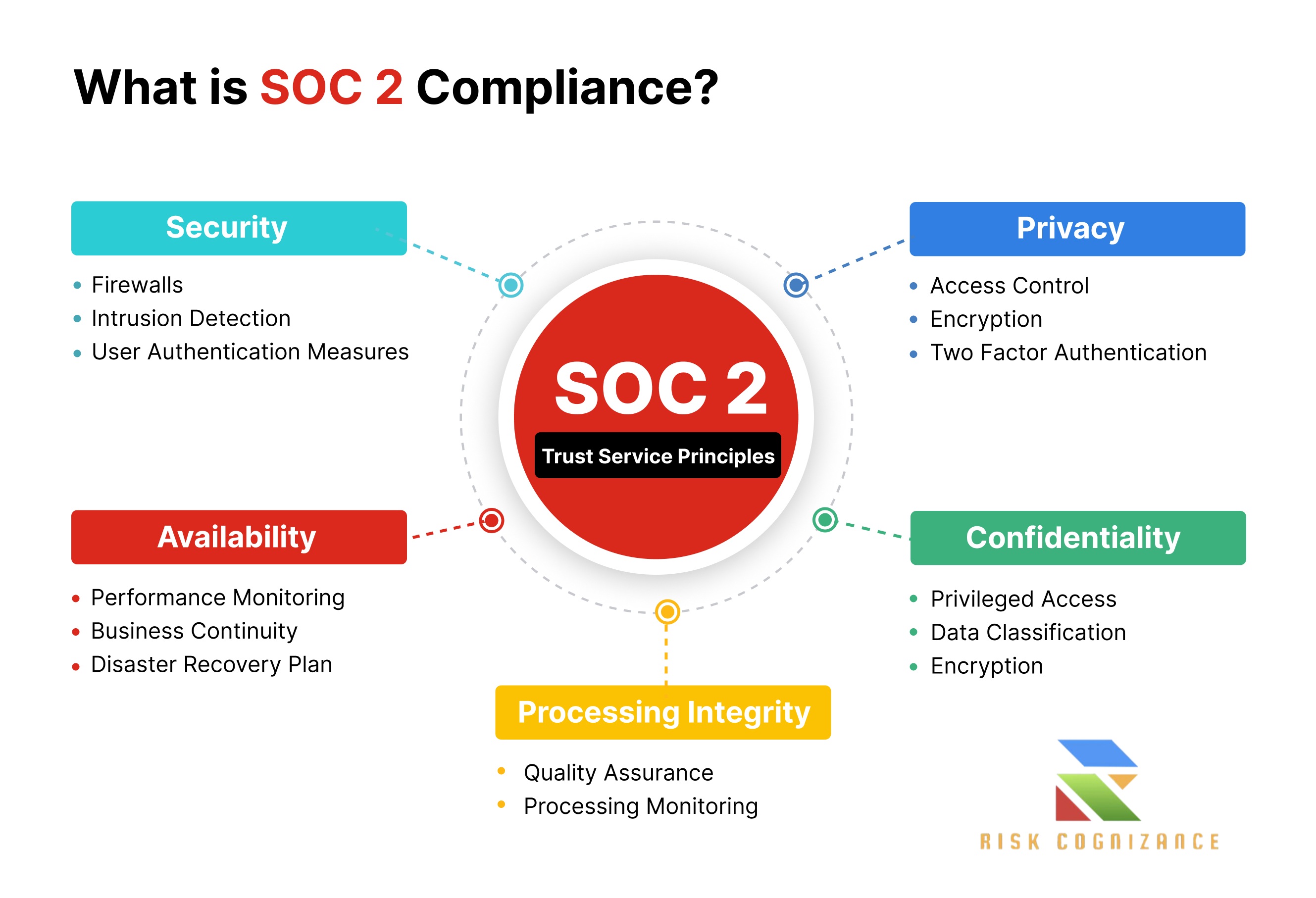
SOC 2, developed by the American Institute of Certified Public Accountants (AICPA), mandates that service organizations manage their data based on five Trust Services Criteria (TSCs): Security, Availability, Processing Integrity, Confidentiality, and Privacy. Achieving and maintaining SOC-2 Compliance demonstrates an organization's proactive stance against cyber threats, operational disruptions, and data misuse. A comprehensive GRC Solution from Risk Cognizance transforms this complex audit into a streamlined, continuous process, fortifying your operations and elevating stakeholder confidence.
The Mandate for SOC-2 Compliance: Why It Matters
The pressure for robust data security and operational transparency is escalating. For service organizations, SOC-2 Compliance has become a non-negotiable strategic imperative:
- Customer Imperative: Clients, especially those in regulated industries, increasingly demand proof of security and privacy assurances. SOC 2 reports provide this critical validation, often a prerequisite for business engagements.
- Regulatory Scrutiny: While not a direct regulation, SOC 2 controls align closely with principles found in data protection regulations like GDPR and CCPA, reinforcing broader compliance efforts.
- Supply Chain Resilience: As organizations scrutinize third-party risk, SOC 2 serves as a critical indicator of a vendor's security posture, safeguarding the entire supply chain from cascading vulnerabilities.
- Mitigating Breach Impact: A well-implemented SOC 2 framework establishes controls that actively reduce the likelihood and impact of data breaches, demonstrating due diligence in the face of cyber threats.
- Competitive Differentiator: In a crowded marketplace, SOC 2 compliance offers a tangible competitive advantage, distinguishing organizations committed to the highest standards of trust and security.
- Risk of Non-Compliance: Failure to meet customer or market expectations for SOC 2 can result in lost revenue, eroded trust, protracted negotiations, and ultimately, a significant decline in market position.
SOC-2 Compliance is a proactive investment in defensible security operations and enduring client relationships.
Challenges in Achieving and Maintaining SOC-2 Compliance
The path to SOC-2 Compliance is often fraught with complexity, particularly for organizations relying on manual or fragmented approaches:
- Defining Scope & Criteria: Accurately identifying the systems, processes, and data within the SOC 2 scope, and mapping them to the relevant Trust Services Criteria, is a significant initial hurdle.
- Extensive Evidence Gathering: SOC 2 requires continuous collection of vast amounts of evidence across diverse systems—from access logs and configuration changes to incident reports and training records. Manual collection is time-consuming and error-prone.
- Implementing & Documenting Controls: Establishing, documenting, and consistently enforcing hundreds of internal controls related to security, availability, processing integrity, confidentiality, and privacy demands meticulous attention.
- Continuous Monitoring: SOC 2 Type 2 requires continuous monitoring and demonstration of controls' operational effectiveness over an extended period (typically 6-12 months), making point-in-time assessments insufficient.
- Managing Third-Party Vendors: Ensuring that third-party service providers (SaaS, cloud, etc.) also meet security expectations adds another layer of complexity, often requiring their own SOC 2 reports or due diligence.
- Audit Readiness: Preparing for the rigorous external audit can be disruptive, demanding significant internal resources to organize documentation and respond to auditor inquiries.
- Evolving Threat Landscape: The dynamic nature of cyber threats means that security controls must constantly adapt, adding complexity to maintaining ongoing compliance.
Without an integrated solution, these challenges often lead to audit fatigue, increased costs, and persistent anxiety regarding compliance status.

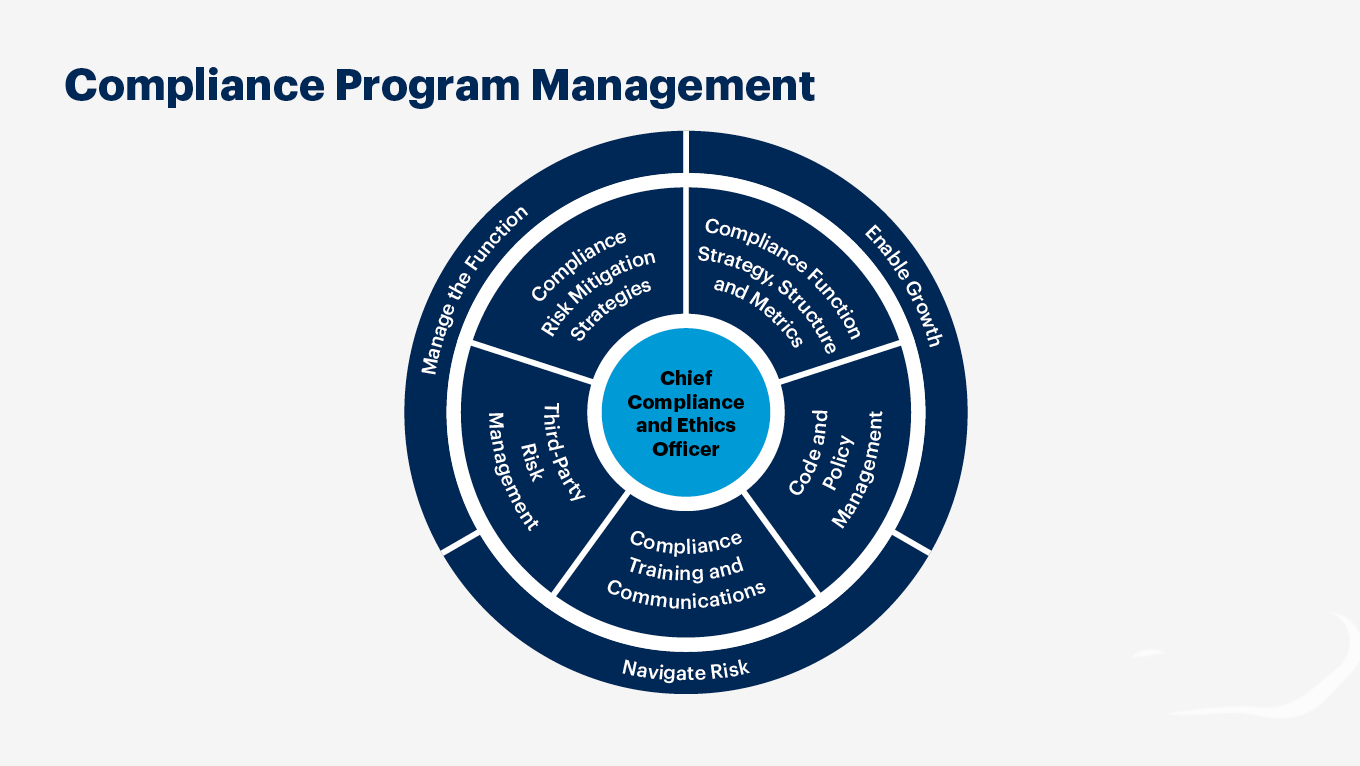
Risk Cognizance: Your Strategic Partner for SOC-2 Compliance
Risk Cognizance delivers not merely a SOC-2 Compliance checklist; we provide an integrated GRC Solution engineered to enable continuous, defensible SOC-2 adherence. Our platform streamlines every phase of your compliance journey, transforming a complex audit into a strategic advantage:
Integrated Connected GRC Solution: Our core platform unifies all GRC activities. It provides a single source of truth for all SOC 2 related policies, risks, controls, and evidence, ensuring consistency and eliminating data silos.
Compliance Management Solution:
- Centrally manages all SOC 2 specific controls and requirements.
- Maps controls directly to the Trust Services Criteria (Security, Availability, Processing Integrity, Confidentiality, Privacy).
- Automates evidence collection and tracks control effectiveness.
Policy Management Solution:
- Manages the creation, approval, and distribution of all security and privacy policies essential for SOC 2.
- Ensures consistent policy enforcement and employee attestation.
Internal Audit Management Solution:
- Facilitates continuous readiness assessments, simulating external audits.
- Manages internal control testing and tracks remediation efforts for any identified gaps before the official audit.
IT & Cyber Risk Management Solution:
- Addresses the foundational Security criteria of SOC 2.
- Identifies and assesses cyber risks, managing vulnerabilities and security controls crucial for data protection.
Vendor Risk Management Solution:
- Assesses and monitors the security posture of your third-party vendors.
- Ensures their controls align with your SOC 2 requirements, mitigating supply chain risk.
Case and Incident Management Solution:
- Streamlines the process for documenting, investigating, and responding to security incidents and breaches.
- Provides critical audit trails for the SOC 2 Security criteria's incident response requirements.
Regulatory Change Management Solution:
While SOC 2 is a framework, our solution keeps your broader security and privacy posture aligned with evolving regulations.
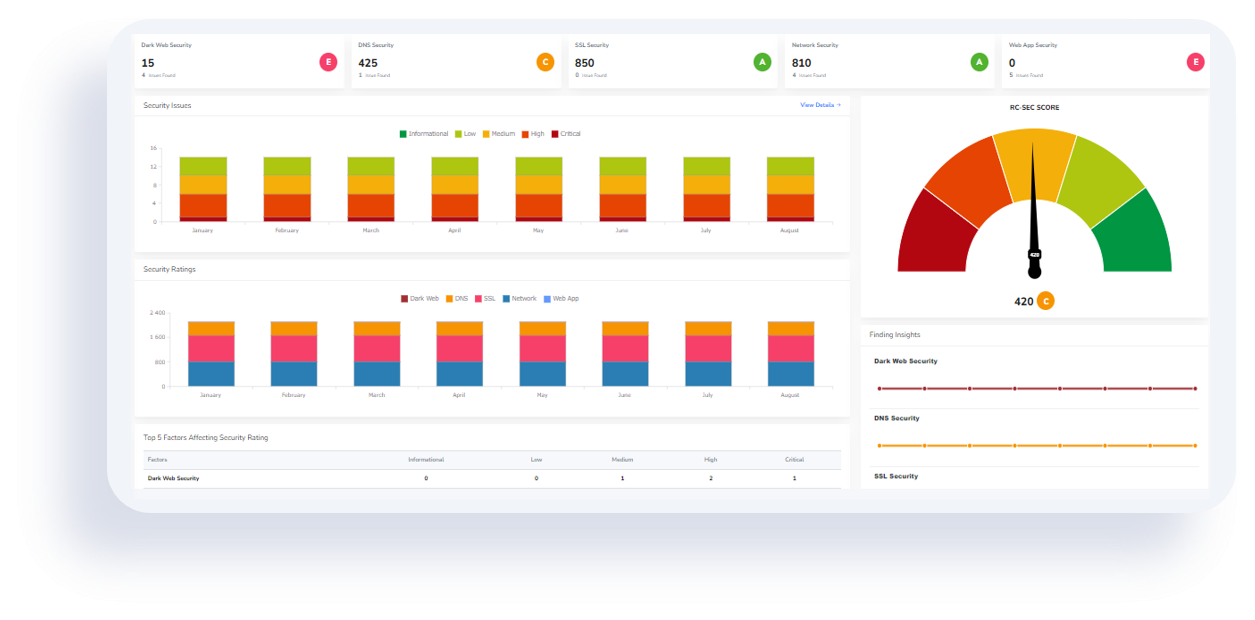
Attack Surface Management:
- Continuously discovers and monitors your external digital assets.
- Helps identify and prioritize vulnerabilities that could impact SOC 2 Security criteria.
Cloud Posture Scanner:
- Automatically scans cloud environments for misconfigurations.
- Ensures your cloud infrastructure adheres to SOC 2 security controls.
Dark Web Monitoring:
- Proactively searches for compromised credentials or data leaks related to your organization.
- Informs immediate action to mitigate risks affecting SOC 2 security.
Risk Cognizance integrates these capabilities to provide a holistic, automated approach to SOC-2 Compliance, ensuring audit readiness and proactive security.
The Strategic Imperative: Outcomes of a Robust SOC-2 Compliance Solution
Deploying an advanced SOC-2 Compliance Solution transitions an organization from a reactive stance to a position of fortified trust and market leadership. It delivers profound, measurable strategic outcomes:
- Enhanced Trust and Credibility: A SOC 2 report validated by an independent auditor immediately elevates your organization's credibility. It assures clients and partners of your unwavering commitment to data security and privacy.
- Competitive Differentiation: In a highly competitive digital landscape, SOC 2 compliance provides a distinct market advantage. It's often a key decision factor for potential clients, distinguishing you from less secure competitors.
- Streamlined Audit Posture: Automated evidence collection, continuous control monitoring, and centralized documentation dramatically reduce the time and resources traditionally consumed by SOC 2 audits. This establishes a posture of continuous audit readiness.
- Superior Security Posture: The rigorous requirements of SOC 2, when integrated with a robust GRC solution, drive significant improvements in your overall security controls, policies, and incident response capabilities, proactively minimizing risk.
- Operational Efficiency: Automating control testing, evidence gathering, and reporting frees up valuable security and compliance teams. They can then focus on higher-value activities like threat intelligence and strategic risk mitigation.
- Reduced Business Risk: By systematically addressing the Trust Services Criteria, organizations significantly lower their exposure to data breaches, operational disruptions, and the associated financial and reputational costs.
- Accelerated Sales Cycles: The ability to swiftly provide a comprehensive SOC 2 report to prospects often expedites sales cycles, removing a common hurdle in business development.
An integrated SOC-2 Compliance Solution is an investment that yields both immediate operational gains and long-term strategic value.
Securing Your Future: Partnering with Risk Cognizance for SOC-2 Compliance
The narrative of data security and client trust is pivotal for every service organization operating in the digital economy. Achieving and maintaining SOC-2 Compliance is a critical chapter in that story one that demands a sophisticated, integrated, and proactive approach. The era of manual, burdensome, and risky compliance processes is definitively over.
Today, a robust SOC-2 Compliance Solution from Risk Cognizance is not merely a technological enhancement; it is a fundamental pillar of organizational resilience and an indispensable catalyst for strategic leadership.
By embracing our integrated GRC Solution, businesses gain not only the operational efficiency, accuracy, and agility required to meet current demands, but also the strategic foresight and unyielding robustness to anticipate and decisively adapt to future security challenges.
Empower your teams, fortify your assets, and secure your reputation. Choose Risk Cognizance, and confidently architect the next chapter of your organization’s success story, guided by unparalleled control, proactive defense, and enduring trust.
Recognized as a
GRC Software Leader



